Google ADs
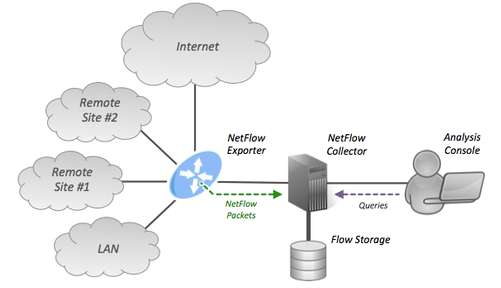
NetFlow is a network protocol developed by Cisco for collecting IP traffic information and monitoring network traffic. By analyzing flow data, a picture of network traffic flow and volume can be built. Using a NetFlow collector and analyzer, you can see where network traffic is coming from and going to and how much traffic is being generated.
As a general monitoring setup typical flow monitoring setup (using NetFlow) consists of three main components –
- Flow exporter: aggregates packets into flows and exports flow records towards one or more flow collectors.
- Flow collector: responsible for reception, storage and pre-processing of flow data received from a flow exporter.
- Analysis application: analyzes received flow data in the context of intrusion detection or traffic profiling, for example.
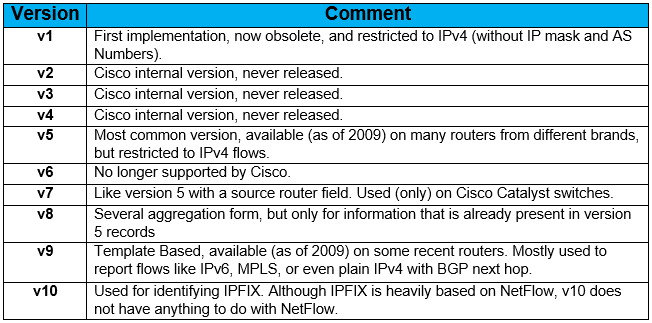
Typical flow analysis information found in a NetFlow data record includes :
Google ADs
- Source and destination IP address
- Source and destination TCP/ UDP ports
- Type of service
- Packet and byte counts
- Timestamps
- Interface numbers
- TCP flags and encapsulated protocol (TCP/UDP)
- Routing information
- next-hop address
- source autonomous system (AS) number
- Destination AS number
- Source prefix mask
- Destination prefix mask
Reference –
https://en.wikipedia.org/wiki/NetFlow
ABOUT THE AUTHOR

Founder of AAR TECHNOSOLUTIONS, Rashmi is an evangelist for IT and technology. With more than 12 years in the IT ecosystem, she has been supporting multi domain functions across IT & consultancy services, in addition to Technical content making.
You can learn more about her on her linkedin profile – Rashmi Bhardwaj