What is a Honeypot?
Honeypot term refers to a fake device which is deployed in a network to attract unknown traffic. As an example, a honeypot could be a virtual server, network device, network port, web server which is designed to give the impression of an active device.
It contains dummy files and data which looks useful to the attacker.
Administrators install minimal protection on honeypot devices so that intruders can easily approach the honeypot.
Traffic will be analysed by the admin to find out what kind of attacks are performed on the honeypot device and based on the attack which prevention method is required to secure the network.
What is a Honeynet?
It is an entire set of servers or devices which act as a honeynet. Bundle of honeypot is known as honeynet. Both honeypot and honeynet come under detective devices which detect unwanted and unauthorised access to the network.
They look and act like genuine systems, but they do not host data of any actual value for an attacker.
Administrators configure honeypot/honeynet in such a way that it looks vulnerable to outsiders. The goal is to grab the attention of intruders and keep the intruders away from the legitimate network that is hosting valuable resources. Legitimate users wouldn’t access the honeypot, so any access to a honeypot is most likely an unauthorized intruder.
Honeypot/honeynet are always configured in different zones from production. Such a setup allows the administrator to analyse the traffic and types of attack without compromising the live network.
The longer the intruder spends time with honeypot/honeynet data, the more time an administrator must inspect the attack.
Honeypot/honeynet most used by large enterprises and organisations for cybersecurity research.
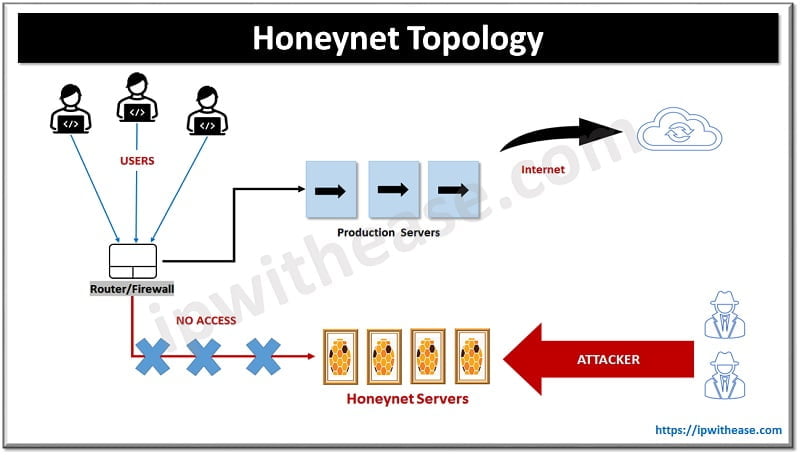
Topology of Honeynet/Honeypot
Exact location of honeynet/honeypot in the network
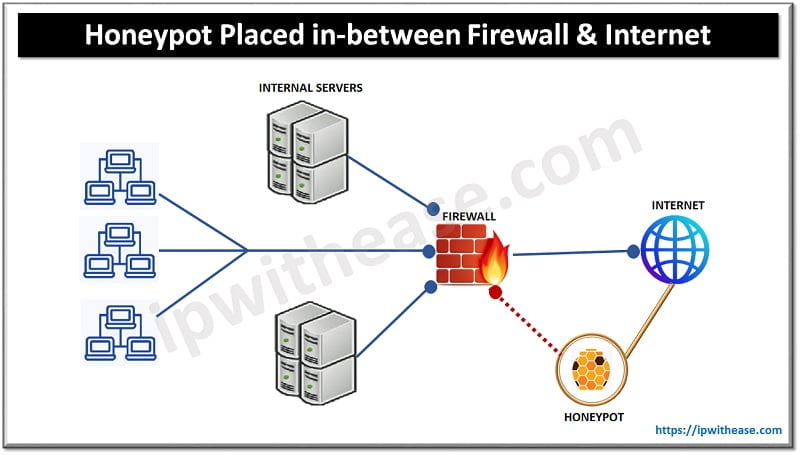
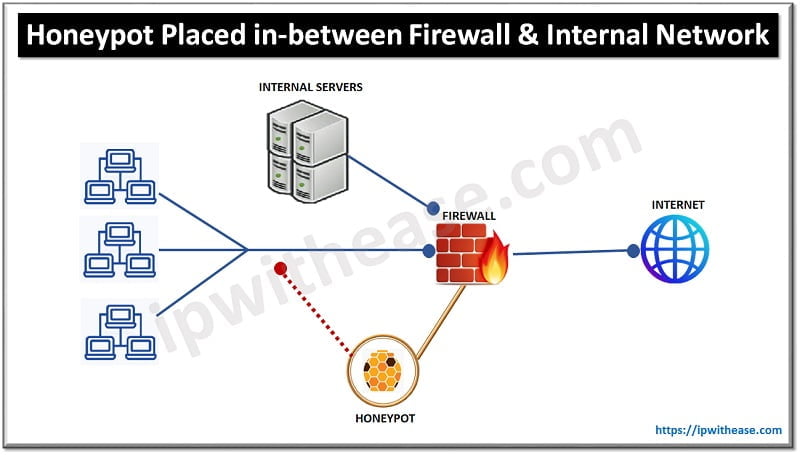
- We can put a honeypot inside the network after the firewall to analyse the inside intruder of the local LAN network.

- We can even place honeypot/honeynet outside the network before the firewall for external traffic by using different segments to detect attempts to enter the internal network.

Types of Honeypots
Based on application feature-
- Email Honeypot: It has long list of malicious/spam emails which could spread virus/worm inside network. All the spam emails scanned in the email honeypot server and suspicious traffic stops at the initial level.
- Malware Honeypot: Malware could be any file, link or folder which is delivered over the network and infects, steal, exploit the data. Malware honeypot detects such traffic to go inside the network.
- Database Honeypot: Attacks on Database like SQL-Injections are very common. Database honeypots help to detect pre-defined malicious database traffic.
Purpose Based Honeypots-
- Research Honeypot: Here, honeypots are deployed and used by Network Administrator to analyse the traffic for better understanding of malicious connections. This technique is used to research the vulnerability, threat, and weakness of the network. Concerned team takes appropriate action post data analysis on the Honeypot server.
It fulfils below strategies
- Threat analysis
- Vulnerability detection
- Defence towards suspicious traffic
- Future security requirement of any organisation
- Production Honeypots: Production honeypots are deployed within any organization’s network along with other production servers. In production-based Honeypots, traffic is captured in the production/live network. It is mainly deployed to identify live attacks on the internal and external network and divert or mislead hackers from attacking authentic servers.
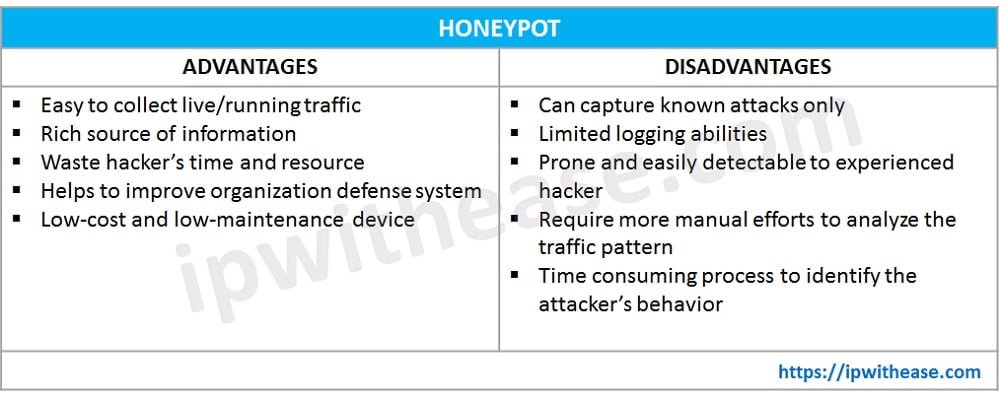
Advantages of Honeypot
- Helps to improve and expand organisation security. It acts as a defence system and helpful to identify loopholes, vulnerability in the network.
- Helps to identify zero-day attack, types of attack and behaviour of attacker
- Divert/ distract attackers from the real production network. Attackers will not have time to harm a real network if they spend time on a honeypot server.
- Low-cost device with minimal maintenance charges.
- Honeypot is easy to deploy. Installation of honeypot isn’t hard. All we need is computer/server (Linux or Windows) with logging and auditing capabilities.
Disadvantages of Honeypot
- More manual efforts are required to analyse the traffic as Honeypot can only collect the suspicious traffic but doesn’t perform any action on traffic.
- It can identify direct attacks only
- Other network zones can be identified by the attacker if honeypot server is compromised.
Benefit of using Honeynet
- Honeynet is a honeypot with some extra value-added features, honeynet analyzes the intruder actions, simultaneously it eliminates risk to others on the internet.
- It stops any infected connection.
- Moreover, it stores a large number of loggings sessions which give a clear view of what bad guys want to do in the network.
Honeynet has log file storage, however attackers can delete those files easily. So, it is recommended to send a copy of logs to another internal server as well. We can enable encryption in honeynet servers which helps us to forward data to any other destination in encrypted format. This technique helps to secure the network in a better way.
We can create a honeynet within a single server or device by using the concept of virtualization. Virtualization makes you run multiple virtual systems on a single host.
Cloud Honeypot/Honeynet
As we all know that cloud technology is used by most of the application developer to store /process the data over the cloud network,
Honeypot/Honeynet can be used to protect cloud infrastructure and deal with suspicious traffic by using threat intelligence features which prevent attack and strengthen the network.
We can use a public cloud to host Honeynet/Honeypot to create a fake network. It separated the actual cloud servers from attacks and doesn’t risk client machine’s sensitive data.
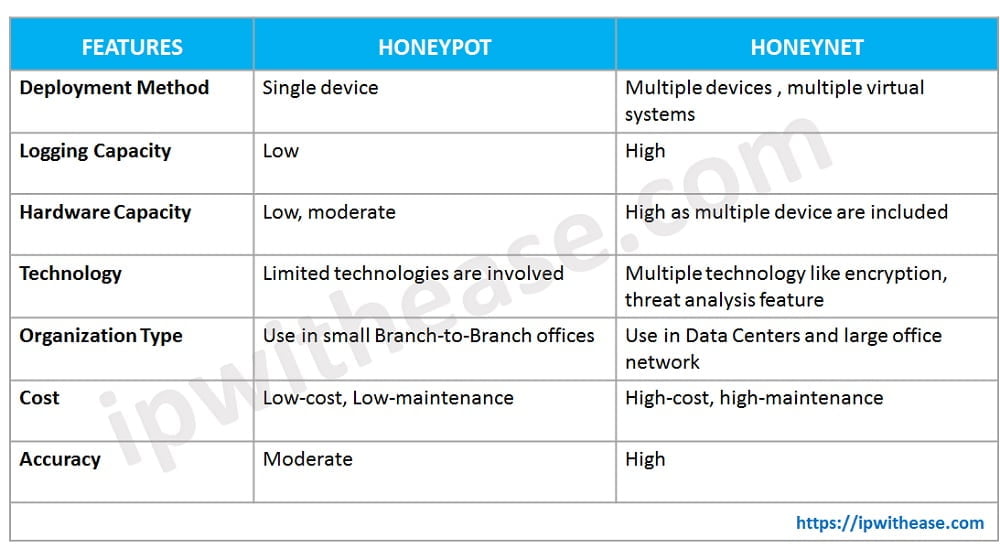
Comparison Table: Honeypot vs Honeynet
Below table summarize the differences between the two:
Conclusion
The purpose of a honeypot or honeynet pointedly affects the measures that need to be taken to ensure that attacks on the honeynet do not compromise the infrastructure on which it is implemented. In a research environment, this can be done by isolating the honeynet system.
Honeynet/Honeypot is a cost-effective approach to identify malicious traffic. Such production honeypots in industrial environments need to ensure that they cannot be compromised by attackers, as well as ensure that they do not interfere with the communication and control processes (i.e., operational resources) of the existing industrial devices.
Continue Reading:
What is Encryption? Detailed Explanation
ABOUT THE AUTHOR

You can learn more about her on her linkedin profile – Rashmi Bhardwaj