Table of Contents
In modern software development, security must be integrated from the beginning into both development and operations processes. Static Application Security Testing (SAST) tools are a fundamental part of this “shift-left” approach. They work by scanning source code to identify vulnerabilities before an application is run.
However, implementing a SAST tool does not automatically improve security. Many organizations run these tools but fail to establish a process for reviewing and addressing the findings.
This often results in a high volume of unaddressed alerts and a mistaken belief that the application is secure. To achieve real value, these tools must be fully incorporated into the CI/CD pipeline, with defined procedures for analyzing and acting on the results.
The Critical Roles in the SAST Lifecycle
For SAST to be effective, everyone must understand their part in the process. It’s a collaborative effort between development, security, and operations.
Modern SAST tools support this lifecycle by providing automated code analysis, centralized reporting, and integration with CI/CD workflows.
- Developer: Fixes vulnerabilities in their code. Uses local scans (e.g., in their IDE) for early feedback.
- Security Engineer: Manages and configures the SAST tool, tunes rules to reduce false positives, and defines security policy.
- DevOps Engineer: Integrates the SAST tool into the CI/CD pipeline and manages the underlying infrastructure for scans.
- Product Owner/Manager: Prioritizes the remediation of vulnerabilities based on business risk and release schedules.
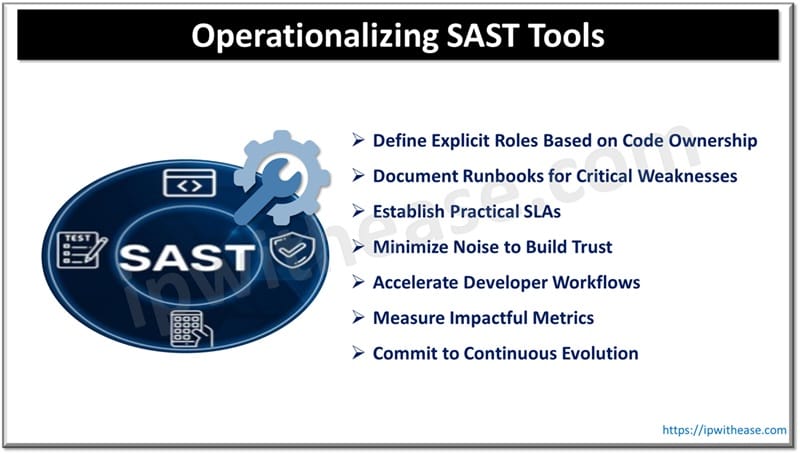
From Tool to Toolchain: Operationalizing SAST for Security and Speed
Acquiring a subscription for SAST tools is straightforward. However, operationalizing them to effectively reduce risk without impeding development requires a foundation of clear code ownership, explicit procedures, and respected service agreements.
The objective is not simply more alerts, but a predictable system for finding, assigning, and resolving vulnerabilities.
Define Explicit Roles Based on Code Ownership
Clarity begins with roles. Security teams own policy definition and auditability. Platform or DevEx teams are responsible for pipeline performance and SAST tool integrations. Service teams, following the principle of code ownership, are accountable for fixing issues within their domains. AppSec engineers amplify efforts by triaging complex findings and creating custom rules in SAST tools for recurring problems.
Document Runbooks for Critical Weaknesses
For each critical vulnerability class, such as those cataloged in MITRE CWE, create detailed runbooks. These should describe how the vulnerability appears, steps to reproduce it, the organization’s accepted fix, and code examples that pass the scan. Link directly to the official MITRE CWE entries and your internal secure coding libraries to direct developers toward vetted solutions.
Establish Practical SLAs
Universal SLAs are ineffective. Instead, segment them by data sensitivity and system exposure. Internet-facing services handling regulated data should have aggressive targets, while internal tools can have more flexible timelines. Crucially, start the SLA clock only when a ticket is formally placed in the owning team’s backlog, based on their code ownership, to prevent inaccurate reporting.
Minimize Noise to Build Trust
A high false-positive rate destroys confidence in SAST tools. Begin with a conservative ruleset and grow it deliberately. Track a precision score and mandate that it meets a minimum threshold before activating hard governance gates. Empower developers to propose suppressions with evidence, and review these requests regularly.
Accelerate Developer Workflows
The goal is to make developers faster, not just busier. Provide pre-commit checks and IDE hints for common issues, saving full scans for the CI pipeline. Automatically route findings to the correct service owners by using code ownership metadata, ensuring accountability and precision.
Measure Impactful Metrics
Security programs should be guided by metrics that directly inform risk reduction. Key among these are Mean Time to Resolution (MTTR), recurrence rates for specific MITRE CWE items, and the percentage of builds blocked by policy. The insights gained enable teams to strategically prioritize framework upgrades and guardrails that prevent entire vulnerability categories.
Commit to Continuous Evolution
SAST governance is not static. Publish a quarterly changelog for your ruleset, deprecating noisy checks and adding rules for new frameworks. Most importantly, encode lessons from security incidents as new rules or lints, ensuring the organization learns from a mistake once and only once.
Ultimately, operationalizing SAST tools is less about configuring dashboards and more about establishing operational clarity. Through defined roles, precise runbooks, and sensible SLAs, you transform SAST from a compliance checkpoint into a reliable asset that enhances engineering velocity and systematically reduces risk.
Defining the SAST Runbooks (The “How”)
The operationalization of SAST depends on runbooks that standardize vulnerability management. They provide a consistent framework for discovering, assessing, and fixing code flaws. This requires detailing not only when to scan but also the precise response to every result.
Here are three critical runbooks for embedding SAST into your DevSecOps pipeline.
Runbook 1: The Developer Pre-Commit Scan (Shifting Left)
This runbook empowers developers to find and fix issues before the code becomes part of the shared codebase, preventing vulnerabilities from ever entering the main branch.
- Objective: Catch common security anti-patterns instantly and educate developers in real-time.
- Trigger: A developer makes code changes locally and is preparing to commit.
- Action: The developer runs a lightweight, fast SAST scan directly from their IDE or via a pre-commit Git hook. This scan should be optimized for speed over comprehensiveness.
- Success Criteria: The scan completes in under 2 minutes, providing immediate feedback.
Outcome & Process:
- If Vulnerabilities Found: The developer reviews the findings. This is where detailed, context-aware runbooks for specific CWE classes are critical. For each finding, the runbook should document its appearance, how to reproduce it, the accepted fix, and link to code examples that pass. This turns a generic alert into a learning opportunity and a clear action item. The developer fixes the issue immediately before committing.
- If Clean: The code is committed to the version control system with confidence.
Runbook 2: The Pull Request (PR) Gate Scan (Quality Gate)
This is your automated quality gate, ensuring that no new code with security regressions can be merged. It’s the core of “shifting left” at the team level.
- Objective: Prevent new vulnerabilities from being introduced into a feature branch or the main branch.
- Trigger: A new pull request is created or updated.
- Action: The CI/CD pipeline (e.g., Jenkins, GitLab CI, GitHub Actions) automatically triggers a SAST scan on the feature branch. This scan is more thorough than the pre-commit scan.
- Success Criteria: The scan completes within a defined time budget (e.g., 10 minutes) to avoid stalling the development process.
Outcome & Process:
- If New Vulnerabilities are Introduced: The build fails or the PR is marked as “failed check.” This hard block mandates that the developer address the issues. To make this work, you must reduce noise early. Start with a conservative ruleset focused on high-confidence, critical vulnerabilities to maintain developer trust.
- If Clean: The PR is marked as successful for the security check, unblocking the path to merge.
Runbook 3: The Nightly Full Application Scan (Comprehensive Audit)
While PR scans catch new issues, this runbook is for continuous risk assessment of the entire application, tracking technical debt and emerging threats.
- Objective: Gain a comprehensive view of the security posture of the entire codebase, including legacy code and dependencies that may have been missed.
- Trigger: A scheduled pipeline (e.g., runs every night at 2 AM).
- Action: A full, in-depth SAST scan is run on the entire main branch or release candidate. This scan uses the deepest analysis level, which may take hours.
- Success Criteria: The scan achieves maximum code coverage and generates a detailed report for triage.
Outcome & Process:
- A consolidated report is generated for the security team review.
- AppSec engineers triage findings, removing false positives and identifying complex vulnerabilities.
- Risk-based SLAs are applied, with critical issues requiring fast remediation and lower-severity items treated as technical debt.
- Trend analysis (e.g., by CWE) guides strategic improvements to frameworks and guardrails.
By moving beyond simple bullet points to describe these runbooks with clear objectives and processes, you provide teams with the operational clarity needed to turn SAST from a compliance hurdle into a reliable asset.
Establishing Meaningful SLAs (The “When”)
Service Level Agreements (SLAs) transform security from an abstract concern into a measurable, accountable process. While runbooks define procedures for handling vulnerabilities, SLAs answer the critical question of required response timelines. These agreements establish the rhythm and predictability that prevent security issues from being overlooked in the development lifecycle.
The foundation of effective SAST SLAs lies in segmenting them by function. First, the SLA for Scan Execution ensures the security tooling itself doesn’t become a development bottleneck. A typical agreement might state that “SAST scans for pull requests must complete 95% of the time within 10 minutes.” This commitment balances comprehensive scanning with development velocity, ensuring security checks don’t unduly delay code integration.
Once scans complete, the SLA for Triage takes effect. This crucial window—often specifying that “all new critical and high-severity vulnerabilities must be triaged by the security team within 4 business hours of detection”—ensures that genuine threats receive immediate attention while false positives are quickly filtered out. This prevents alert fatigue and ensures development teams only spend time on real issues.
The most impactful SLA governs remediation timelines. However, a one-size-fits-all approach rarely works effectively. Instead, remediation SLAs should be segmented by both severity and context:
- Critical Severity: Remediate within 3 business days for vulnerabilities that could lead to immediate system compromise
- High Severity: Address within 10 business days for serious flaws that require prompt attention
- Medium Severity: Resolve within 30 business days for issues that present meaningful risk but allow for scheduling flexibility
- Low Severity: Incorporate into regular technical debt management cycles
Effective remediation requires SLAs calibrated to asset risk. High-exposure systems, such as internet-facing services processing sensitive data, necessitate stricter remediation timelines than low-risk internal applications.
To ensure accurate performance measurement, the SLA remediation clock should commence only upon a triaged ticket’s assignment to the owning team’s backlog. This eliminates accountability gaps and provides valid metrics.
This risk-based, tiered structure enables organizations to uphold security standards without impeding development velocity.
Conclusion
Effective SAST implementation moves it beyond a compliance task to become a core part of improving code quality and security. This requires defined roles, documented procedures, and practical response times. Integrating security this way makes it a shared responsibility, leading to earlier vulnerability fixes and more secure, efficient software releases.
ABOUT THE AUTHOR
IPwithease is aimed at sharing knowledge across varied domains like Network, Security, Virtualization, Software, Wireless, etc.