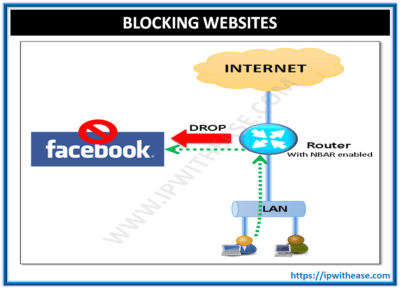
Cisco IOS has some wonderful set of features like restricting some websites access based on ACL or QOS which make use of the Layer 1, 2, 3 or 4 parameters to block/restrict. NBAR is a powerful tool of cisco which enables the IOS to do application level filtering.
Especially in scenario where customers have corporate site connected to internet via Cisco router and we want to block access to certain websites. The blocking of website becomes imperative in order to restrict employees from browsing social websites to increase productive official time. In normal practice this would be done using ACL on routers and then blocking the IP address of those particular websites. But we can use NBAR to match the websites exact address which makes it a lot user friendly.
Let us look at the configuration example –
We will first create a class-map and then use match protocol to use the NBAR.
In this example we will specifically block access to facebook.com and ‘*’ will be used to match all sub-domains of Facebook and restrict the access.
- R1(config)#class-map match-any Block_Website
- R1(config-cmap)#match protocol http host “*facebook.com*”
- R1(config-cmap)#exit
Next we create a policy-map which will use the class-map created above and will take the action on the matched address used in class-map.
- R1(config)#policy-map Drop
- R1(config-pmap)#class Block_Website
- R1(config-pmap-c)#drop
- R1(config-pmap-c)#exit
The policy-map has an action of drop for all the http traffic destined for facebook.com from a site connected to internet.
Lastly we apply this policy-map on the ISP facing interface of the router.
- R1(config)#interface fastEthernet 0/1
- R1(config-if)#service-policy output DROP
Verification –
R1#show policy-map interface fastEthernet 0/1 FastEthernet0/1 Related- Cisco Blocking Website You can learn more about her on her linkedin profile – Rashmi Bhardwaj
Service-policy output: Drop
Class-map: Block_Website (match-any)
1 packets, 300 bytes
5 minute offered rate 0 bps, drop rate 0 bps
Match: protocol http host “*facebook.com*”
1 packets, 500 bytes
5 minute rate 0 bps
drop
Class-map: class-default (match-any)
5000 packets, 44081 bytes
5 minute offered rate 10000 bps, drop rate 0 bps
Match: anyABOUT THE AUTHOR