Table of Contents
One of the major milestones in network security is encryption and hashing. Hashing techniques are prevalent all across industries and widely used to secure data at rest or in transit. Open communication on the Internet or information lying on systems in plain text can be intercepted by hackers or threat actors, hashing provides a means to secure your data and information from prying eyes.
In today’s topic we will learn about SHA-2 encryption technology, learn about hashing in general, its key characteristics and how SHA-2 works?
What is Hashing?
Before we deep dive in understanding SHA-2 encryption we have to understand the underlying concept of hashing. Hashing is a process where raw data is scrambled up to a state that it can be reproduced back in its original state. The plaintext information is picked up and passed through a function which performs mathematical operations on it. We call this function hashing and output from this function is digest or value.
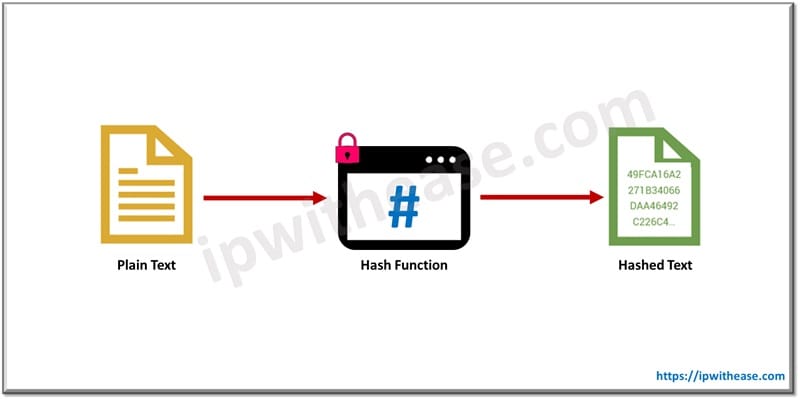
Hash function converts plaintext into hash digest. It is irreversible if input remains unchanged output will also not be changed whatever numbers of iterations undertaken.
Applications of Hashing
- Password Hashing – Hash value converted into password and stored on server. While login value stored in the database is compared with hash value provided.
- Verification of Integrity – When a file is uploaded to a website, hash value is also shared as bundled. While the user downloads, the file value of hash is recalculated and compared with integrity of data.
What is SHA-2 Encryption?
With NIST and NSA joint efforts in 2001 Secure hash algorithms such as SHA 256 are part of SHA-2 algorithm family and it is successor to SHA-1 which lost its strength in brute force attacks. Irrespective of plaintext size the hash value is always 256.
Characteristics of SHA-256 Algorithm
The length of the plaintext should be < than 264 bits. This is required to keep digest as random as possible.
Hash digest length would be 256 bits in SHA-256 and SHA-512 is 512 bits. Bigger the digest means more significant calculations (based on cost and space)
All hash functions are irreversible such as SHA-256. Getting neither plaintext before digest nor original value of digest is possible when you pass through its hash function.
SHA-2 Working Step by Step
The complete process is divided into five stages.
- Padding Bits – addition of extra bits into the message resulting in length which is exactly 64-bit short of 512 multiples. The first bit should be one and the rest all can be zeros.
- Padding Length – To make plaintext into 512 multiples 64-bits of data can be added. The 64-bits are calculated by application of modulus to the original plaintext without adding any padding.
- Buffer Initialization – The eight buffers are initialized with default values to be used in iterations. Also 64 keys need to be stored in an array starting from K(0) to (K63).
- Compression Function – The complete message is broken down in 512 bits for each block. Each block is put to 64 iterations of operation having output of each block serves as input to the following block.
- Output – With every iteration output of the previous block becomes input for the next block. Final output is considered as hash digest or value and this iteration will continue until we reach the 512 bit block.
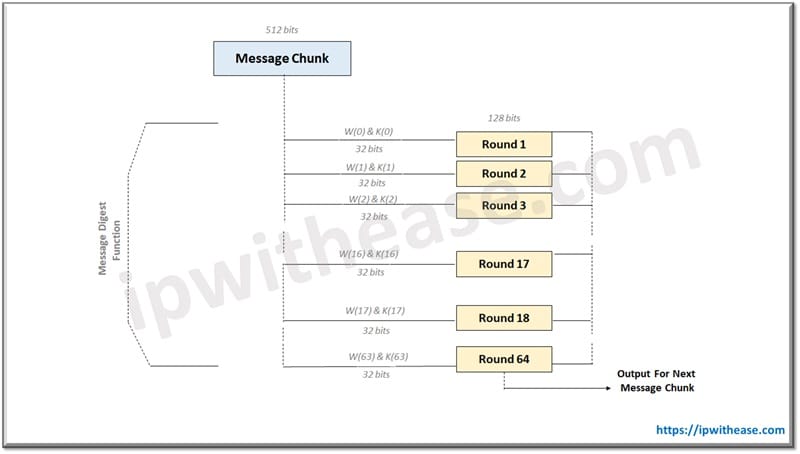
The value of K(i) in all iterations is pre-initialized and W(i) is another input which is individually calculated for every block based on the number of iterations processed at a time.
Applications of SHA Algorithm
Digitate signature verification uses asymmetric encryption for verification of document/ file authenticity.
- Password Hashing – Passwords are stored on websites in hashed formats to lessen load on databases having all digest in the same size and due to privacy concerns.
- SSL Handshake – For secure connection SHA function is used to perform SSL handshake during web sessions.
- Integrity Checks – file integrity is verified using SHA and MD5 algorithms to ensure they are not tampered and altered during transit.
ABOUT THE AUTHOR

You can learn more about her on her linkedin profile – Rashmi Bhardwaj