Table of Contents
In this blog, we discuss the difference Proxy vs NAT in detail. First we will understand the two terms, different types of proxy server and NAT. Next we will deep dive into the differences between the two.
What is a Proxy?
A proxy server works like a bridge between you and the internet. It serves as an intermediator between users and the websites they visit. Proxy servers offer different levels of functionality, security, and privacy depending on specific needs, use case, or guidelines.
There are different types of proxy servers like: datacenter proxy, residential proxy (rotating residential proxy or static residential proxy), Anonymous Proxy, Private Proxy, Dedicated Proxy, Shared Proxy, Public Proxy, SSL/HTTP Proxy etc.
What is NAT?
Network Address Translation (NAT) allows a single, distinctive IP address to represent an entire collection of computers. Within the realm of network address translation, a private network computer or computers are assigned a public address by a network device, typically a router or NAT firewall.
Network address translation enables a single device to function as a mediator or intermediary between the local, private network and the internet, serving as a bridge between the two networks. there are different types of NAT like: Dynamic NAT, Static NAT, NAT Overload.
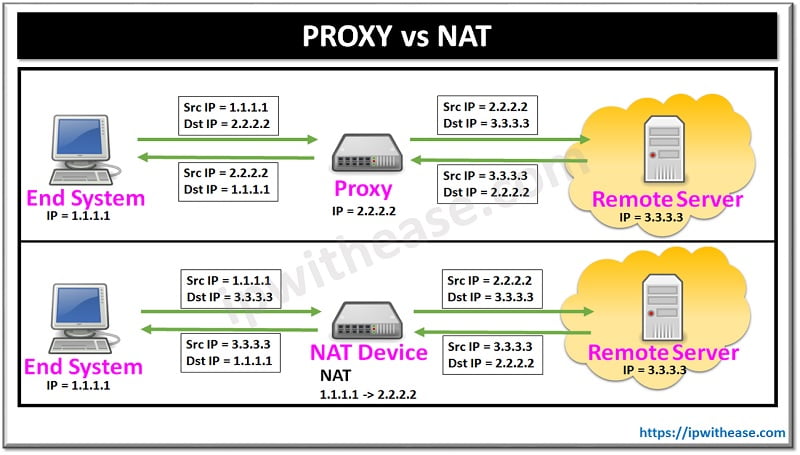
Proxy vs NAT
Proxy and NAT are 2 commonly used terms when planning for protecting a secured LAN environment in IT setups of organizations.
- While NAT alters the Local IP of end systems to Public IPs for communication over the Internet, Proxy provides application-level security to end systems and mitigates vulnerabilities which may directly affect the end systems.
- Proxy functions up to layer 7 of the OSI model whereas NAT functionality is limited to Layer 3 and 4.
- Proxy is meant to work at application levels like HTTP and FTP while NAT is inclined towards hiding the private address in LAN and minimizing the usage of Public IP addresses (Public IPs incur the cost and are limited in number).
Related – What is Reverse Proxy
Comparison Table: Proxy vs NAT
Below table provides a detailed view of the difference between Proxy and NAT:
| PARAMETER | PROXY | NAT |
|---|---|---|
| Terminology | Proxy is terms used for device which sits between an end system and remote server and acts as a mediator. The client requesting the resource connects to the proxy server and once validated proxy connects to remote server and provides the requested content to the client. | NAT alters IP address in a header of an IP packet and allows using Public IP for communication to outside world and private IP for communication to inside LAN. |
| Key functions | Provides secured Internet based application access to end hosts. | Conversion of private IP to Public IP |
| Layer of function | Layer 7 | Layer 3/4 |
| Protocol Specific | More Protocol Specific like HTTP,FTP etc. | More inclined towards IP addresses and less protocol specific. |
| End host Configuration | May require end host to be configured in case of explicit proxy. Transparent proxy may not require configuration at end host system. | No Configuration required at end host system. |
| NAT/Proxy device visibility | Proxies act as middlemen between 2 parties in which both end points know they are communicating with the proxy | The 2 communicating parties don’t know there is a NAT device in the middle. |
| Application requirement | Does not need any special application software to operate | Applications behind a proxy server must support proxy services and should be configured to use the proxy server. |
| Target Solution | Recommended for corporates where the user count is high and used in conjunction with NAT. | Recommended for corporates where the user count is low and light traffic flow |
| Cost | Costly since a dedicated proxy device is required to perform the functionality. | Cheap and no dedicated NAT device is required. NAT can be performed on any layer 3 or above device like Router, Firewall, L3 Switch etc. |
| Placement in network | Generally placed in DMZ Zone in a corporate network | Generally NAT is performed by Perimeter device like Internet Router or Internet Firewall. |
| Traffic Flow | Typical scenario – The Source system sends to traffic towards proxy with source IP as its own and destination IP that of Proxy. The proxy initiates a new session with its own IP as Source and destination IP that of remote Server. | Typical scenario – The Source system (using private IP) sends to traffic towards destination remote Server. The NAT device converts the source/destination private IP into Public IP and sends towards remote Server. |
| Data Caching | Supported | Not Supported |
| Information and Traffic Control | High level of Control since works upto Layer 7 | Limited level of traffic control |
| Overhead | High associated overhead since in proxy each packet is analyzed and then action performed. | Much simpler and very less associated overhead |
| Key Benefits | Improved security and control over end System access to outside world | NAT is hiding a number of private IPs behind a smaller number of public IPs to alleviate the shortage of IP addresses |
| Related terms | Explicit proxy, transparent proxy, caching, URL and content filtering | NAT overload, PAT , Static NAT etc. |
Download the comparison table: Proxy vs NAT
Continue Reading
ABOUT THE AUTHOR

You can learn more about her on her linkedin profile – Rashmi Bhardwaj