Time based ACL is an inbuilt feature on the Cisco IOS where we can block some access for a specified duration of time and allow access at all other times. Time based ACL uses time ranges to block the traffic during specified duration.
To demonstrate this feature we will use a simple topology as below using three routers where router 1 acts as the host and router 3 acts as some webserver. We will block the traffic from host to webserver for duration Mon-Fri between 8:00am to 6pm and allow traffic at all other times.
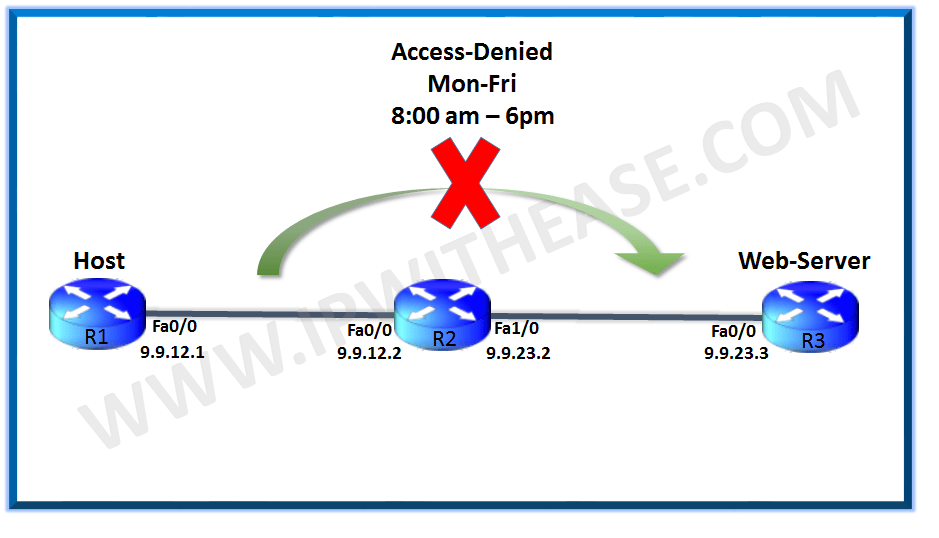
Now let us have a look at the configurations:
R1:
interface FastEthernet0/0
ip address 9.9.12.1 255.255.255.0
!
ip route 9.9.23.0 255.255.255.0 9.9.12.2
R3:
interface FastEthernet0/0
ip address 9.9.23.3 255.255.255.0
!
ip route 9.9.12.0 255.255.255.0 9.9.23.2
On R2 we will have to do most of the configuration for the time based access.
Interface FastEthernet0/0
ip address 9.9.12.2 255.255.255.0
!
Interface FastEthernet1/0
ip address 9.9.23.2 255.255.255.0
!
First we define a time-range on R2:
time-range Business_hours
periodic weekdays 8:00 to 18:00
Then we define an ACL and call the time-range defined above in that:
ip access-list extended No_Youtube
deny tcp any host 9.9.23.3 eq 80 time-range Business_hours
permit ip any any
!
The above ACL denies all the traffic from R1 to R3 on port 80 between Mon-Fri 8am to 6pm and allows all other traffic.
Now let us apply the ACL to the interface.
R2(config)#int fa0/0
R2(config-if)#ip access-group No_Youtube in
R2(config-if)#int fa1/0
R2(config-if)#ip access-group No_Youtube in
The current time on the R2 is as below which falls in the time range for blocking the traffic.
R2#sh clo
*12:37:41.719 UTC Wed May 30 2018
So as result of it our connectivity between R1 and R3 on port 80 is blocked as below:
R1#telnet 9.9.23.3 80
Trying 9.9.23.3, 80 …
% Destination unreachable; gateway or host down
R2#sh ip access-lists
Extended IP access list No_Youtube
10 deny tcp any host 9.9.23.3 eq www time-range Business_hours (active) (1 match)
We also see all other ports traffic is allowed from R1 to R3 as below:
R1#telnet 9.9.23.3 23
Trying 9.9.23.3 … Open
Password required, but none set
[Connection to 9.9.23.3 closed by foreign host]
Now to test the time range let us manually set the time on R2 to a value out of our time range:
R2#clock set 19:00:00 30 May 2018
R2#
*May 30 19:00:00.003: %SYS-6-CLOCKUPDATE: System clock has been updated from 12:42:25 UTC Wed May 30 2018 to 19:00:00 UTC Wed May 30 2018, configured from console by console.
Now the time set on R2 is out of our time range so we see we are able to connect from R1 to R3 during this time.
R1#telnet 9.9.23.3 80
Trying 9.9.23.3, 80 …open
We see the time rage is now inactive on R2 as below:
R2#sh ip access-lists
Extended IP access list No_Youtube
10 deny tcp any host 9.9.23.3 eq www time-range Business_hours (inactive) (1 match)
ABOUT THE AUTHOR

You can learn more about her on her linkedin profile – Rashmi Bhardwaj