Table of Contents
In the modern world, businesses are faced with unseen threats on a daily basis. The Internet has made the world smaller and enabled connections to be made much more quickly than before, but this also means that malicious actors can identify potential victims much faster than ever before. Intrusion prevention systems (IPS) are one of the most important measures you can take to protect your business from cyberattacks.
There are many different types of IPS solutions available today, but not all of them are suitable for every business or budget. In this article we will look at some of the IPS Systems that should keep your business safe against cyberthreats. Let’s get started!
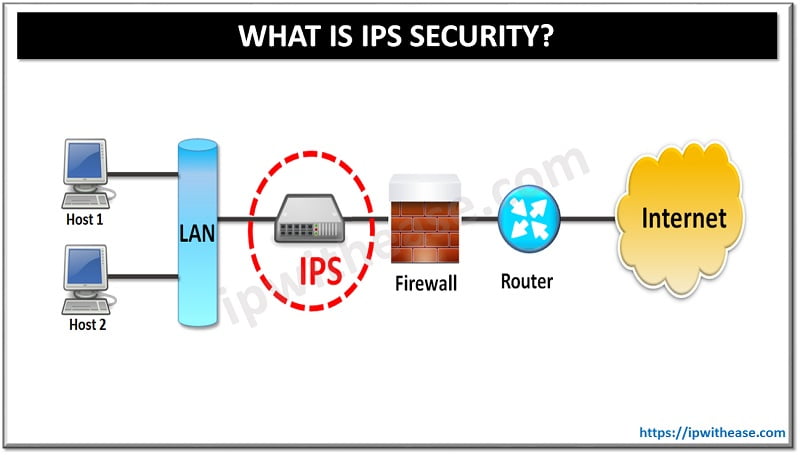
What is an Intrusion Prevention System (IPS)?
An intrusion prevention system (IPS) is a network security device that inspects traffic in and out of your business’s network for malicious content or behavior. If something suspicious is found, it blocks the traffic and prevents the malicious activity from reaching its intended destination or having any harmful impact on your network or computers.
Intrusion prevention systems are often referred to as a “first line of defense” against network intrusions because they are designed to detect and stop malicious traffic before it has a chance to reach your computers. An intrusion prevention system differs from an intrusion detection system (IDS) in that it actively blocks traffic it has identified as malicious, whereas an IDS merely logs the activity as a potential threat. IPS systems are generally deployed on the network’s edge, as they are responsible for monitoring inbound and outbound traffic.
IPS Features and Benefits
IPS systems include a variety of security tools and features, including –
- Network traffic monitoring – with network traffic monitoring, the IPS device monitors network traffic for malicious content or network abuse.
- Network anomaly detection – network anomaly detection looks for unexpected or anomalous network activity that might indicate a cyberthreat.
- Rule-based blocking – enables the IPS to block specific types of malicious or unwanted network traffic as soon as it appears.
- Network vulnerability assessment – helps the IPS device identify security issues and possible areas of weakness in the network.
- Real-time threat intelligence – enables the IPS to instantly identify new malware and other cyberthreats that appear in the wild.
- Network traffic flow optimization – helps ensure the IPS device doesn’t have a negative impact on network performance.
- Network threat visualization – enables the IPS to graphically display threats and cybercriminal activities so that IT admins can quickly recognize any red flags.
List of Intrusion Prevention Systems
SolarWinds Security Event Manager (SEM) IDS/IPS
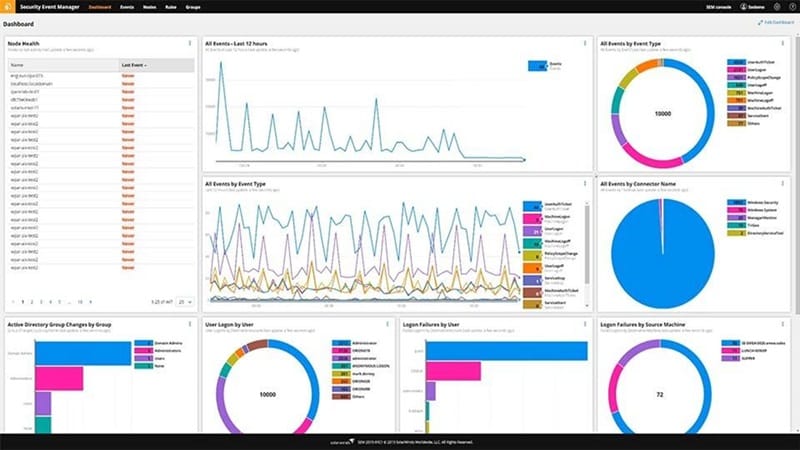
SolarWinds SEM is an advanced network and security monitoring solution that provides security and threat analysis, end-point management and compliance auditing.
- It also provides real-time visibility through log management, network performance monitoring and more than 70 plugins.
- It has built-in intrusion detection and prevention capabilities with pre-built rules for over 2700 threats.
- SolarWinds SEM can integrate with your other security solutions to provide more detailed alerts and create better remediation plans.
- It also provides granular network flow analysis, so you can identify and troubleshoot network issues quickly and easily.
Trellix Intrusion Prevention System
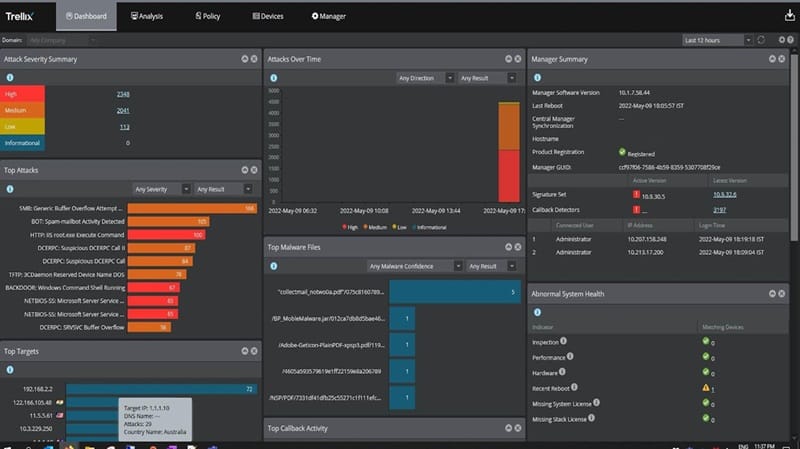
With the need of securing your data, Trellix offers a complete security solution with Intrusion Prevention System that protects against viruses, malware and attacks with a built-in firewall and anti-virus.
- Trellix IPS is firewall security software built on advanced IPS technology to ensure your network and data are safe from malicious threats.
- Trellix IPS provides real-time protection and monitoring of your network and data.
- It detects and prevents viruses, worms, Trojans, and other malicious scripts, like the Crypto-Locker, from infecting your data.
- Trellix IPS also has a built-in firewall to prevent unauthorized users from accessing your data.
Snort Intrusion Prevention System
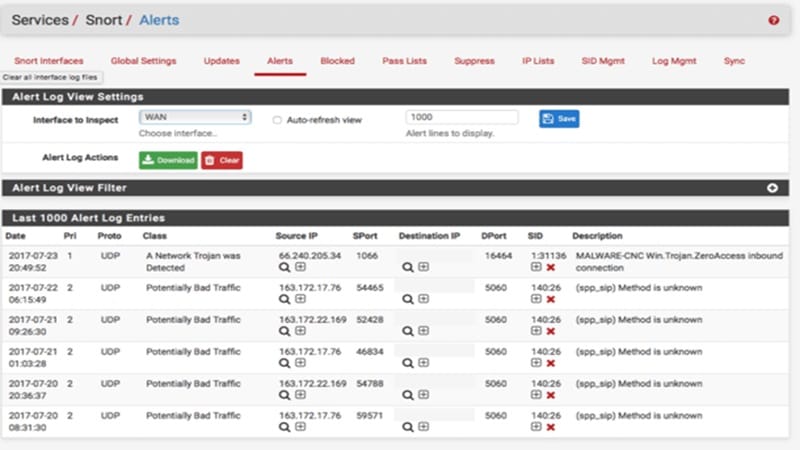
Snort is an open source Network Intrusion Prevention System (NIPS) and Network Intrusion Detection System (NIDS) that can be used to monitor network activity for suspicious activity such as potential computer viruses or hackers trying to break into your network.
- Snort is highly flexible and configurable, enabling you to set up rules to block specific IP addresses or hostnames, log all activity, or simply ignore everything.
- Snort can be used both on Windows and Linux machines and can be integrated with other security solutions.
OSSEC Intrusion Prevention System
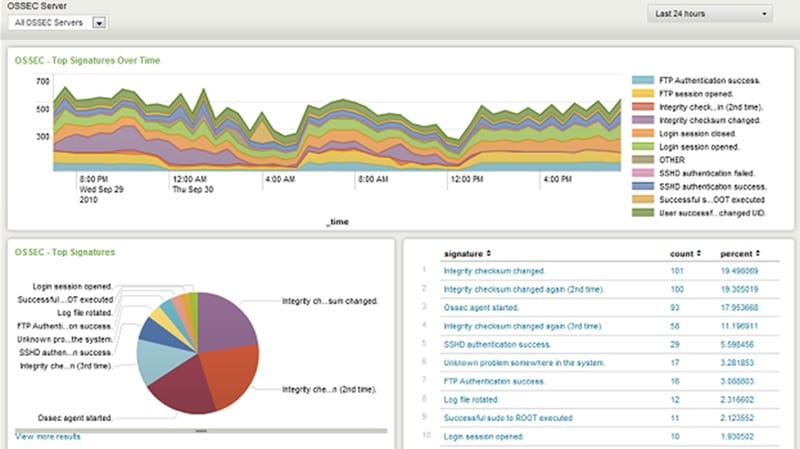
OSSEC is an open-source network monitoring and security auditing tool that can detect and prevent both internal and external threats.
- OSSEC uses signature-based detection, anomaly detection, and log analysis to identify and block suspicious activity.
- It can be installed on a wide range of devices, including Windows and Linux servers, switches, routers, and laptops.
- OSSEC also includes a management console where admins can review alerts and configure settings.
Zeek Intrusion Prevention System
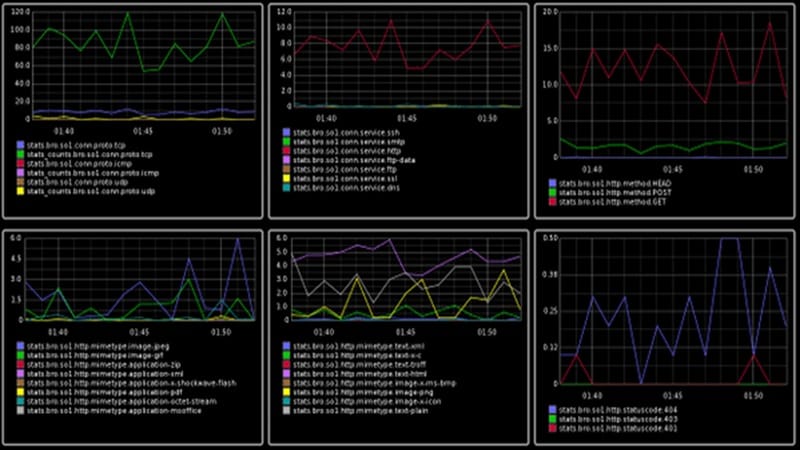
Zeek is a powerful IPS with a wide range of security and auditing capabilities.
- Zeek can detect and block threats, track and control network activity, and generate network reports.
- Zeek’s detection and blocking capabilities include an extensive list of viruses and malware, plus rules designed to block IP addresses and hostnames associated with malicious activity.
- Zeek also monitors network activity and detects suspicious behavior such as outbound connections.
Comparison: SolarWinds Security Event Manager vs Trellix vs Snort vs OSSEC vs Zeek IPS systems
| Feature | SolarWinds Security Event Manager | Trellix (formerly McAfee IPS) | Snort | OSSEC | Zeek (formerly Bro) |
| Type | SIEM | Commercial IPS/IDS | Open-source IDS/IPS | Open-source HIDS | Open-source IDS |
| Deployment | On-premises, Cloud | On-premises, Cloud | On-premises, Cloud | On-premises, Cloud | On-premises, Cloud |
| Real-time Threat Detection | Yes | Yes | Yes | Yes | Yes |
| Signature-Based Detection | Yes | Yes | Yes | Yes | Yes |
| Behavioral Analysis | Yes | Yes | No | Yes | Yes |
| Anomaly Detection | Yes | Yes | No (requires additional tools) | Yes | Yes |
| Log Analysis | Yes | Yes | No | Yes | Yes |
| Packet Inspection | No | Yes | Yes | No | Yes |
| Host-Based Protection | No | No | No | Yes | No |
| Network-Based Protection | No | Yes | Yes | No | Yes |
| Automated Threat Response | Yes | Yes | No | Yes | No |
| Forensic Capabilities | Yes | Yes | No | Yes | Yes |
| Integration with SIEM | Yes | Yes | Yes | Yes | Yes |
| Open-Source | No | No | Yes | Yes | Yes |
| Cost | Paid | Paid | Free (with premium options) | Free | Free |
| Best Use Case | SIEM for log monitoring and event correlation | Enterprise-grade IPS for network security | High-performance network IDS/IPS | Host-based intrusion detection and log monitoring | Network traffic analysis and forensics |
Download the comparison table: Top IPS Systems Compared
Which IPS to Choose?
An IPS solution should have built-in firewall capabilities, including real-time updates, and be capable of protecting against all types of malware, including viruses and worms. It should also have the ability to log all activity and generate reports.
The best IPS for your business will be the one that is compatible with your existing network infrastructure, provides real-time protection, and can be easily integrated with your existing security tools.
ABOUT THE AUTHOR

You can learn more about her on her linkedin profile – Rashmi Bhardwaj