Difference between WAF & RASP
Web Application Firewall WAF
WAF inspects incoming HTTP traffic for known attack payloads and patterns of abnormal usage. When a suspicious payload or abnormal pattern is detected, this can be reported and blocked. WAF blocks IP addresses and provides customization of set of rules in addition to real-time alerts and reporting.
WAF separates known bad traffic from good traffic and ensures that information is not getting processed which is not relevant. One more major benefit of the WAF solution is lower application infrastructure costs.
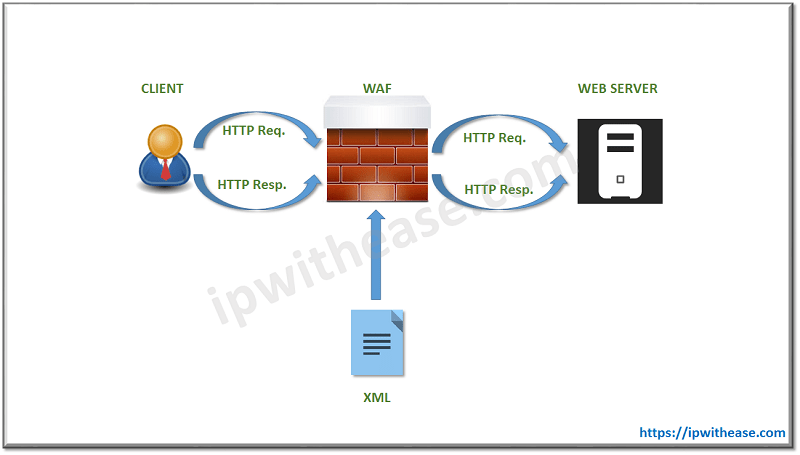
How Does a WAF Work?
WAF is a tool that protects web servers from cyber-attacks. It primarily works by serving as a filter between the web server and client and attacker detecting bad traffic. WAF protects from cyber-attacks in real-time but can also serve as a background monitoring tool that requires no human intervention. WAF blocks threats by detecting risk and there is risk of false positive detections may cause drainage of time.
Features of WAF:
- Prevent a Future Hack
- Virtual Security Patches
- Block Brute Force Attacks
- Mitigate DDoS Attacks
- Performance Optimization
Related – WAF vs Network Firewall
Run-Time Application Self-Protection (RASP)
RASP is a technology that runs on a server when an application runs. Run Time Application Self-Protection is designed to detect attacks on an application in real time. When an application is running, RASP can protect application from malicious attacks by analyzing both the app’s behavior and the context of that behavior. App can continuously monitor its real time behavior pattern of traffic, where attacks can be identified and mitigated immediately without human intervention.
When application is running on server, RASP unifies security into a running application. RASP intercepts all the traffic from the app to the system and secures the app data and validates data requests directly inside the app. RASP protects Web and non-web apps. RASP doesn’t affect the design of the app.
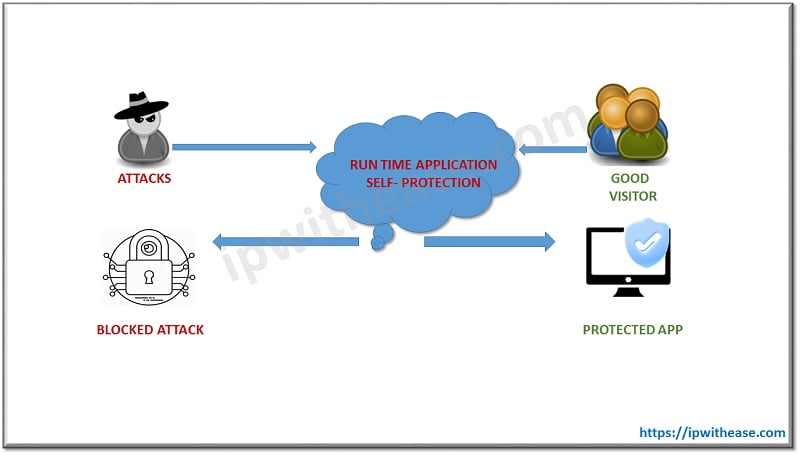
How Does RASP Solutions Work?
Runtime Application Self-Protection (RASP) operates in two modes: –
- Self-protection mode: Runtime Application Self-Protection (RASP) security tool inspects any possibility of execution of requests at run-time environment which might pave way for cyber-attacks owing to different vulnerabilities in codes of an application.
- Monitoring mode: In monitoring mode, this is where self-protection aspect comes to the picture. It works towards monitoring of vulnerabilities only.
Features of a RASP:
- Minimal performance impact without latency.
- Should not introduce vulnerabilities.
- Maintain distance from PII of users.
- Should not learn the bad stuff.
- Minimal headache in deployment.
- Zero code modification and easy integration.
- Detects both attacks and vulnerability.
- Apply defense inside the application.
- Have code level insights and telemetry.
- Lesser false positives.
- Better Attack telemetry.
- Identification of bugs.
- Injects security at runtime.
- Supports Pen Testing with greater visibility.
- Log events in custom apps.
- No use of blacklists.
Difference between WAF and RASP
- WAF is a network security device that detects and take action against attack while RASP technology detect attacks in real time.
- WAF is flexible and hybrid in deployment while RASP requires minimal intervention of administrator during deployment.
- WAF mitigates DDOS attack while RASP detect both attack and vulnerability.
- WAF protects mobile apps from malicious attack while RASP Identify bugs and Log events within custom apps.
Comparison Table : WAF vs RASP
Below table summarizes the difference between Web Application Firewall (WAF) and Run-Time Application Self-Protection (RASP) :
| PARAMETER | WAF | RASP |
|---|---|---|
| Full Form | Web Application Firewall | Run-Time Application Self-Protection |
| Attack prevention | Pattern matching | Runtime application self-protection |
| Attack & vulnerabilities | Primarily attack prevention | Detects both attacks and vulnerability |
| Working | Mitigate DDoS Attacks and Block Brute Force Attacks | Injects security at runtime |
| False positives | May occur | No. These are eliminated |
| Protection method | WAF protects web apps by filtering, monitoring, and blocking any malicious HTTP/S traffic traveling toward the web application by adhering to a set of policies. | RASP is designed to detect attacks on an application in real time. When an application begins to run, RASP can protect it from malicious input or behavior by analyzing both the app's behavior and the context of that behavior. |
| Insights & visibility | Attack insight and intelligence | Supports Pen Testing with greater visibility |
| Rule types | Static | Application specific |
| Alerts | Based on predictions | Based on application behavior |
| Protection & identification | Protection for mobile app’s and rest API and AJAX | Identification of bugs |
| Logs of activity | You can use the Web Application Security Event Logs screen to define tags and filters to help you find meaningful events. | RASP also logs security incidents and user actions (user identity, type of event, date and time, success/failure, origination, and name of affected system component) for improved forensics and post-mortem correlations. |
| Action against attack | WAF creates set of policies against all type of attacks like Brute Force Attacks, a SQL injection attacks and XSS Attacks and many others. | RASP tools offers multiple detection techniques like sandboxing, semantic analysis, input tracing and behavioral analysis to go along with signatures. |
| Deployment | Flexible, hybrid deployment | Minimal overhead of deployment |
| Defense level | Multi-layer defense/defense in | Applies defense inside the application |
Download the comparison table here.
Conclusion
Having both WAF and RASP (specific modules where you can do intrusive deployments and updates) does strengthen your defense. While a WAF will continue to block threats actively from DDOS, bot protection and common OWASP attacks, RASP can have deeper application specific policies.
Continue Reading:
ABOUT THE AUTHOR

You can learn more about her on her linkedin profile – Rashmi Bhardwaj