Table of Contents
Introduction to DDoS Attack
DDoS attacks are a very dangerous type of attack that concerns a lot the cyber security community nowadays.
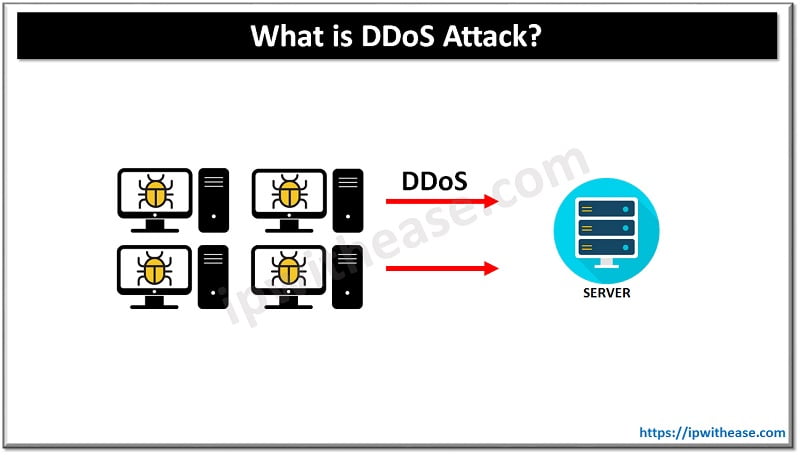
DDoS or otherwise Distributed Denial of Service is a kind of attack that targets the server and not the client computer in order to overload it with multiple connections. DDoS attacks have a high succeed rate when they are coordinated by “botnets”, resulting in an increased power.
DDoS is one of the 5 most dangerous cyber attacks on the planet and in order for a DDoS attack to be successful, the attacker should possess under control a computer network, commonly known as “zombie net”.
In order for these computers to become “zombies” they will have to be infected by some kind of virus or a Trojan. If the above is accomplished, the hacker is now able to affect these computers as a complete network. The result of this attack by the “zombie net” can now be the increased bandwidth overload of a webpage, resulting to a server failure and unavailability.
Related – Zero Day Attack
DDoS Attack Tools
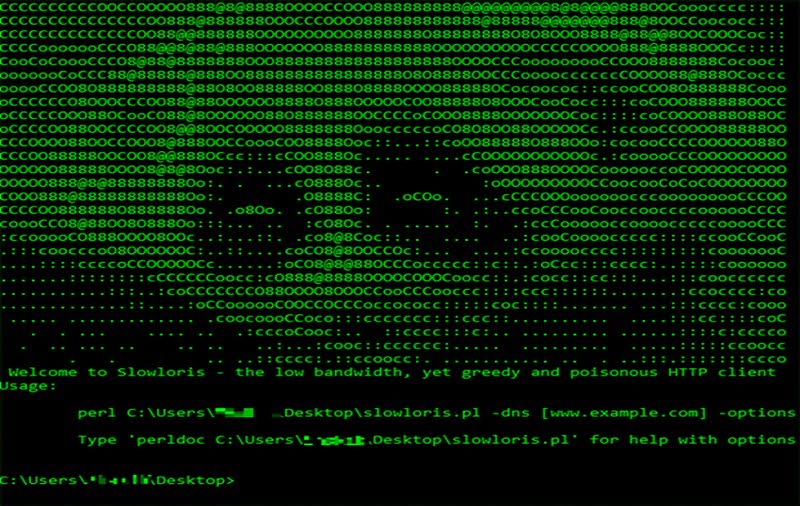
A very famous tool for performing a DDoS attack is known as “slowloris”. This type of tool was created in 2009 from “Rsnake” and it has a few different characteristics. The first one is the ability to create a server failure with only 1 computer (client) and second one is the low network resources needed for such a failure.
This low network resource give the advantage to keep complete privacy of the “hacker”. Furthermore “slowloris” tries to keep as many connections as possible to the “server”.
Other very common DDoS attack tool is the “Low Orbit Ion Cannon (LOIC)”, which is an open-source type application. It is a very user friendly program and utilizes TCP and UDP protocol layer attacks to be carried out.
In addition to the above, a very handy tool, which is an updated version of the “Low Orbit Ion Cannon (LOIC)’ is also available. Its name in the IT community is known as “High Orbit Ion Cannon (HOIC)” and has the advantage of using HTTP protocol instead. The software is designed to have a minimum of 50 people working together in a coordinated attack effort.

Reasons for DDoS Attack
The main reasons for a DDoS attack are the following:
- Overloading HTTP Attacks: The mission of such an attack is clearly the need to exhaust the resources of the target. By overloading the HTTP connections an attack can be extremely powerful and complicated to be treated by a simple server.
- Protocol Attacks: Protocol attacks can cause the interference of services of a server, occupying most of the capacitance that a server can supply.
- Volumetric Attacks: Those kind of attacks can cause a sort of misalignment between the target’s bandwidth and the rest of the “zombie’s” network. A huge amount of data is sent to the target using a form of mass movement, like in case of a “Botnet”.
- DNS Overloading: A DDoS attack on the DNS can cause the server to be overloaded by opening multiple connections and waiting for the server to respond. This results in an overloaded server due to increased bandwidth.
Related – DOS vs DDOS
Mitigation of DDoS Attacks
Experts in computer security domain are investigating on ways to prevent DDoS attacks and are faced a real challenge. Most grueling is how to recognize a DDoS attack that opens connections, from real connections.
A practical scenario is on “Black Fridays” when webpages are overloaded with high load of traffic and protecting the applications from DDoS attacks will be a total failure.
Thankfully, nowadays cyber security has invented solutions dealing with DDoS attacks such as:
- Traffic Isolation: The traffic of a web page is isolated using a “rate limiter”, therefore increasing security but on the other hand compromising on user experience.
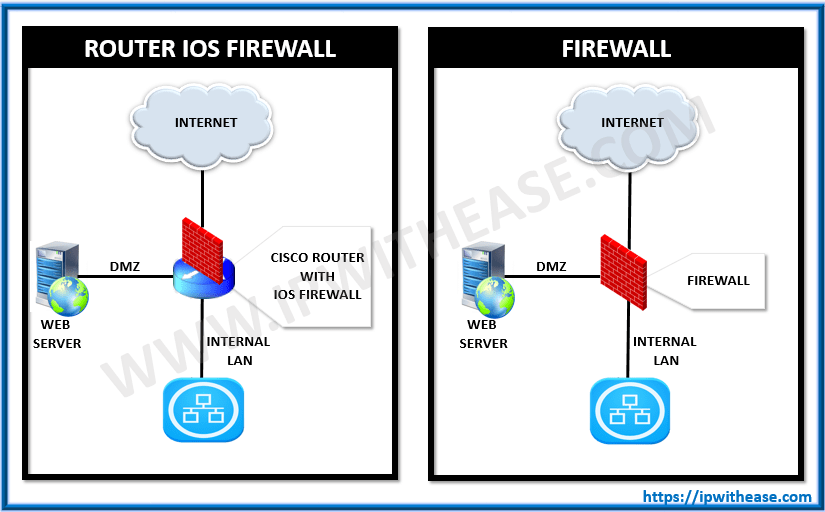
- WAF: Commonly known as Web Application Firewall, it is kind of firewall that works as an inverted proxy. This technology protects the server and the web page from malicious traffic.
- CDN: Using CDN (Content Delivery Network) results in a very stable operation of the web page due to the fact that this technology allocates the web page in multiple servers. This makes it impossible to lose the service.
ABOUT THE AUTHOR

You can learn more about her on her linkedin profile – Rashmi Bhardwaj