Table of Contents
Introduction to DevSecOps
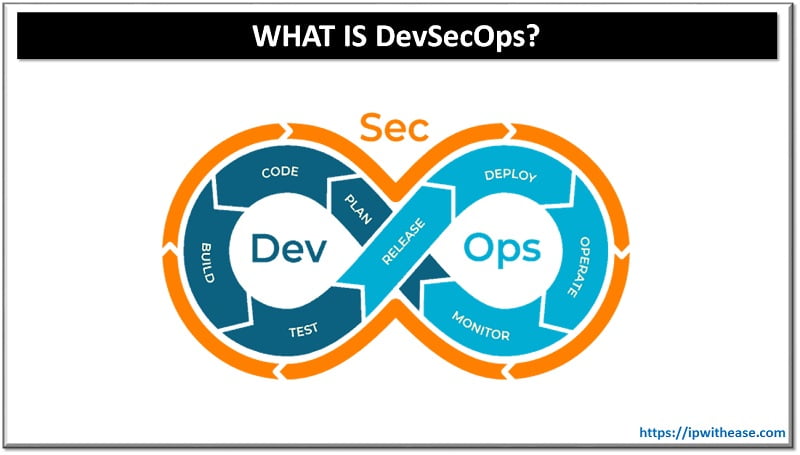
Nowadays, in the IT Security industry the term DevSecOps is a de facto name for development, security and operations. To be more specific DevSecOps is used at every phase of the software development lifecycle, in order to help the integration of security.
DevSecOps is an evolutionary process that represents a natural and necessary way of development for organizations, on how to deal with security. Therefore, it addresses security issues faster, easier and with less cost. In addition, DevSecOps has the ability to share responsibilities for application and infrastructure security to different in-house sectors such as development, security and IT operations teams.
Application Security Tools for DevSecOps Implementation
Today, in the cybersecurity industry many organizations and companies have the choice of application security tools (AST) to integrate in to their systems with intent to advocate DevSecOps. The most common type of these tools used are addressed below:
- Static application security testing (SAST): One of the most known tool in the industry for DevSecOps implementation is Coverity. Coverity, like the most SAST tools, scans proprietary code or custom created code, for structure errors and design flaws. Coverity tool is also used during the code build and development of Software Development Life Cycle (SDLC).
- Software Composition Analysis (SCA): The most commonly used tool for Software Composition Analysis is called Black Duck. The main function of the tools is to scan open source code and binaries, in order to identify weakness and third party components. Other SCA tools have also the ability to provide insight into security and license risks. A successful integration into organization’s systems can also detect new open source vulnerabilities, from build integration to pre-production release.
- Interactive Application Security Testing (IAST): In the cyber community industry, one of the most renowned tool for IAST is the Seeker. Seeker tool has the ability to run in the background during functional testing, web application analysis and runtime behavior. Like other IAST tools, it detects runtime vulnerabilities and automatically tests the data, providing detailed insights to the software developers which line of code contains the syntax error.
- Dynamic application security testing (DAST): One of the best tools in this category is the Tinfoil Security. Similar to the most DAST tools, it interacts with websites and finds vulnerabilities with a low rate of false positives. The difference with the above categories is that, DAST tools do not require access to developer’s source code or customizations to scan the written code. These tools also simulate “Hackers” behavior as a black box.
Related – Agile vs DevSecOps
Advantages of using DevSecOps Implementations
The advantages of using DevSecOps implementation have been presented below:
- Rapid and Cost-Effective Software Delivery: The most common problem in software creation techniques is the security optimization process. It needs a huge amount of time to write safe code in any programming language. Introduction of DevSecOps in IT environments minimizes time consumption and maintenance cost by avoiding unnecessary code rebuilds.
- Improved and Proactive Security: As mentioned above in the introduction, another crucial advantage is the fact that DevSecOps introduces security process from the beginning of the software development cycle. Therefore whole of the application code is reviewed, audited, scanned and tested for security errors. If a security error is found, it will be fixed immediately without consuming time for waiting the code to be re-compiled.
- Repeatable and Adaptive Process: As organizational services grow, their security posture matures as well. Further, DevSecOps also becomes a repeatable and adaptive process. This ensures security is effective consistently across the IT environment and adaptive to new technology requirements. A wise implementation of DevSecOps will maintain automation, management configuration and orchestration to a new level of security.
Conclusion
DevSecOps proves to be a reliable approach for organizational security. Its key benefits encourage software developers to integrate security coding into everyday life.
Furthermore, expert management skills are obtained from DevSecOps as they group developers with IT Security scientists together.
DevSecOps is due for mushroom growth across micro, small, medium and large enterprises and across all IT industries. As more companies search for ways to detect and fix security issues early in the software development process, the demand for tools to support DevSecOps will get a further boost.
Related – What is DevOps?
ABOUT THE AUTHOR

You can learn more about her on her linkedin profile – Rashmi Bhardwaj