Table of Contents
As communication happening over the Internet is not secure and can be intercepted by any malicious actor it is important to secure the communication before data flows through the channel. Cryptography and encryption techniques are widely used and standards have existed around it since generations. Encryption protocols are widely used to secure – data at REST and data in TRANSIT.
Encryption’s sole aim is to protect data during transit while scrambling it.
In today’s topic we will learn about SSL/TLS, how they work, why they are used, their key features and use cases.
About SSL/TLS Encryption
SSL/TLS was developed way back in 1994 by Netscape. A cryptographic protocol which provides secure communication on the Internet and commonly used to secure sensitive data while transmission such as login credentials, credit card details, personal information between a client and web browser. SSL/TLS establishes a secure connection which is encrypted between server and client to ensure any data transmission happening between two parties is secure and confidential, tamper proof and not possible to intercept by malicious actors. This encryption is achieved using cryptographic algorithms to convert data into unreadable format which can only be deciphered by the intended recipient.
Features of SSL/TLS Encryption
- One of the key features of SSL/TLS encryption is the use of digital certificates for server authenticity verification purposes. These certificates are issued by certificate authorities (CA) which contain information about the server, its domain name and public key. Whenever a client approaches the server, its certificate is checked to ensure validity and it is not being tampered. This helps in prevention of man-in-the-middle attacks where an attacker tries to intercept communication happening between server and client.
- SSL/TLS provides data integrity to ensure data received by clients is not modified during transit, Message authentication codes (MAC) are used to achieve this by using cryptographic algorithms which are added to the data frame. The client can verify data integrity by calculating MAC and compare it with MAC which is received. If they match that means data is tamper proof.
- SSL/TLS provides a server authentication mechanism. During SSL/TLS handshake the server presents a digital certificate to the client, to prove its identity. The client verifies the certificate authenticity to ensure its communication is happening with the intended server only.
- SSL/TLS protocols have evolved to address security vulnerabilities and improved performance. Each new version is enhanced to its previous counterpart with stronger encryption algorithms and more secure handshake.
- SSL is the predecessor of TLS. TLS 1.0 was defined in RFC 2246 by IETF which was an upgrade to SSL version 3.0.
Use of SSL/TLS
- Used on Internet widely all websites we visit are HTTPS which are secured by TLS
- Email with SMTP is SMTP + TLS
FTPS for file transfer is FTP + TLS
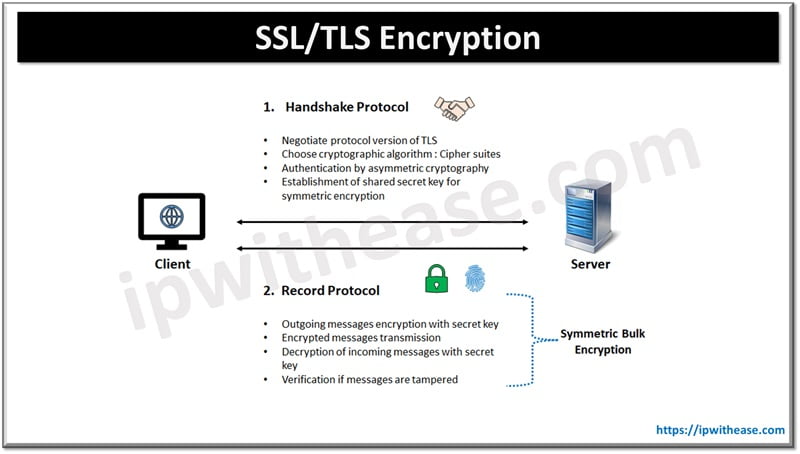
How does TLS work?
TLS communication works in two phases – handshake and record
- Handshake Protocol – Client and server negotiate protocol version in this phase. Selection of cryptographic algorithms happens, they authenticate each other by asymmetric cryptography and establish a shared secret key which will be used for symmetric encryption in the next phase of record. Main objective of the handshake phase is authentication and exchange of keys.
- Record Protocol – in this phase all outgoing messages will be encrypted with a shared secret key which was established in the handshake phase. Encrypted messages are transmitted and verified to ensure if there is any modification or tampering happening during the transmission. If there is no tampering identified then messages will be decrypted with the same symmetric secret key. This phase’s main objective is to preserve confidentiality and integrity of data.
Various symmetric algorithms are supported by SSL/TLS such as AES (Advanced encryption standard), 3DES (Triple data encryption standard), RC4 (Rivest Cipher 4) etc.
ABOUT THE AUTHOR

You can learn more about her on her linkedin profile – Rashmi Bhardwaj