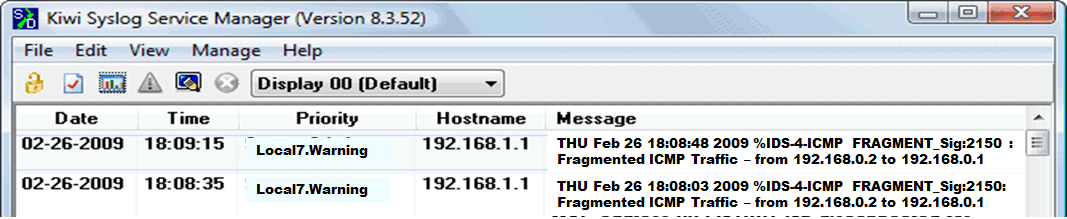
The Cisco IOS Firewall IDS feature is supported on Cisco Router platforms. It is ideal for any network perimeter and especially locations in which along with a router, additional security check is required between network segments. As an imperative Security control, It also protects intranet and other semi secure zones like DMZ and Extranet.
The Cisco IOS Firewall IDS feature identifies 59 of the most common attacks using “signatures” to detect patterns of misuse in network traffic. The signatures represent severe breaches of security and the most common network attacks and information-gathering scans.
When Cisco IOS IDS is enabled, Cisco IOS Firewall is automatically enabled. Thus, IDS uses Cisco IOS Firewall default parameter values to inspect incoming sessions
Below diagram will help understand how to configure IDS feature set on Cisco IOS Router –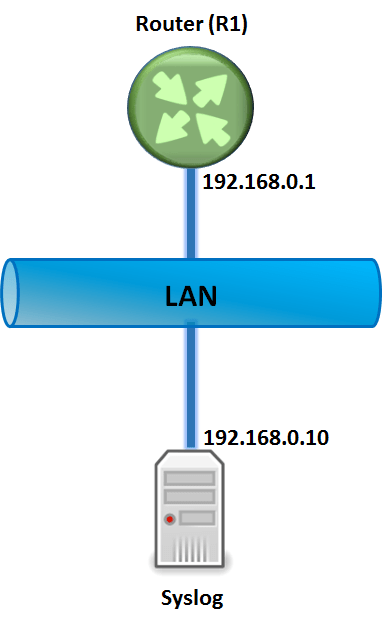
In global configuration Mode:
R1(config)# logging console
(enable logging on router console)
(The above command mention the syslog server address)
R1(config)# logging trap 7
(logging severity level)
(set the alarm action against the matching signatures, and TEST is the name of audit specification)
Router(config-if)# ip audit TEST in
(implementation on router inside interface)
ABOUT THE AUTHOR

You can learn more about her on her linkedin profile – Rashmi Bhardwaj