Table of Contents
Authentication mechanisms are crucial in the wireless world to ascertain identity of users and devices. Access control establishment happens based on user identity in the network such as users belonging to an enterprise required to access its internal network; however, guests are restricted to Internet access only. Additional access control mechanisms such as access permissions to hosts with specific IP address only or virtual LAN and subnet assignment to users based on their identity are also provided by some authentication protocols.
Today we look more in detail about PAP and CHAP protocols, their working, configuration, and features.
What is PAP (Password Authentication Protocol)?
Many protocols consist of passwords to provide authentication services. In Dial-in connections Point-Point-Protocol (PPP) is widely used. For user device authentication PPP authentication includes Password Authentication Protocol (PAP), Challenge Handshake Protocol (CHAP) protocols.
PAP (Password Authentication Protocol) is used to establish identity of peer to authenticator with two-way handshake. At initial link establishment this activity is performed.
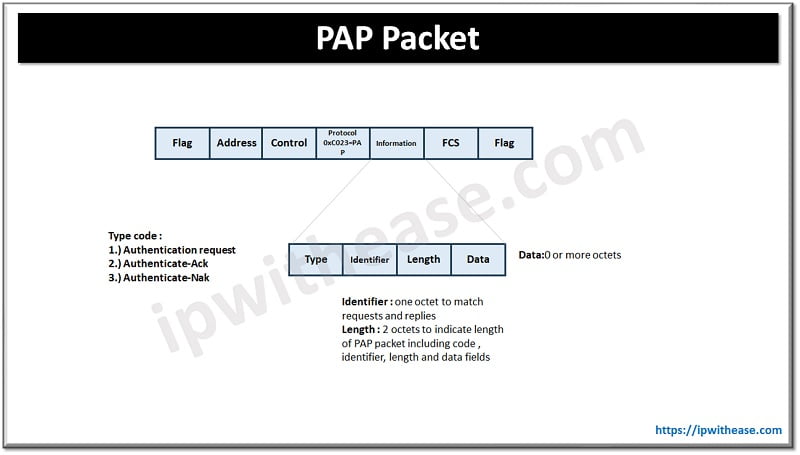
Once the link establishment is completed the authenticate-request packet initiates PAP authentication. The packet comprises of name and password as shown in figure below.
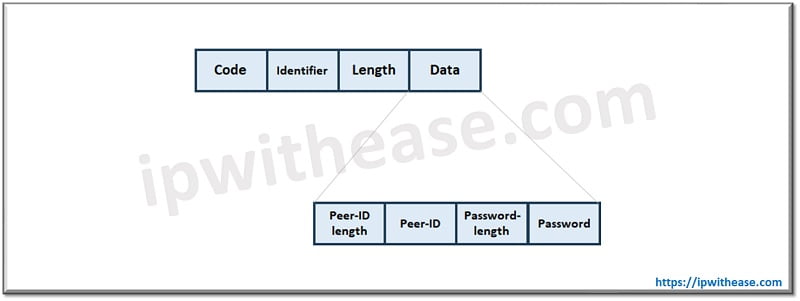
The request packet is transmitted recurrently until a valid response packet is received or retry counter is expired. On receiving a Peer-ID/Password pair which is valid and acceptable, reply is sent with Authenticate-Ack (where Ack is short for acknowledge). If it is not valid or acceptable, then Authenticate-Nak (where Nak is short for negative acknowledge) is sent by authenticator.
It is not a very strong authentication mechanism and passwords are sent in clear text. Which means there is no protection from replay or repeated trial and error attacks. Frequency is controlled by peer and timing of attempts also.
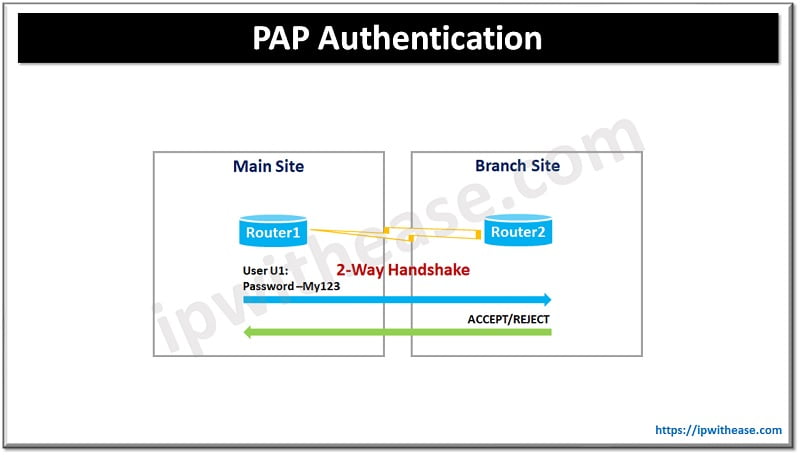
To enable PAP use command
Router1(config-if)#ppp authentication pap
Router1(config-if)#ppp pap sent-username U1 password My123
Router2(config-if)#ppp authentication pap
Router2(config-if)#ppp pap sent-username U1 password My123
What is CHAP (Challenge Handshake Authentication Protocol)?
The CHAP (Challenge Handshake Authentication Protocol) is a three-way handshake mechanism in which the identity of a user is verified periodically. CHAP can be performed through initial link establishment and repeated any time after link is established.
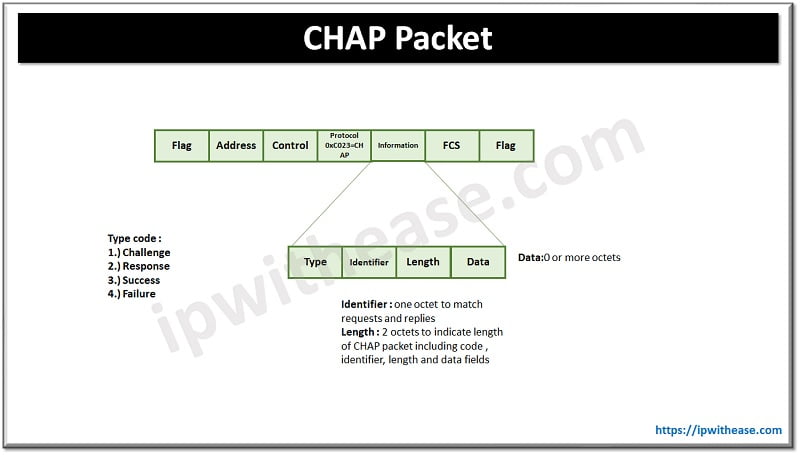
Network security in CHAP is ensured by mandating peers to share a plain text secret. The secret is never transmitted over a link. The secret is installed and exchange happens out of band. Once the link establishment happens the authenticator sends a challenge message to the peer. The challenge comprises of identifier ID, random number, hostname of local device or user name on remote device. The peer at the receiving end calculates the hash value of a random number with one way hash function; the secret is input for one way hash function.
Challenge response is sent by the peer having encrypted ID version, secret password , random number and host name or user name of remote device. Post receiving challenge authenticator verifies the secret by performing the same encryption operation. Response is compared with the expected hash value. If values match then authenticator sends a success message and link is established by LCP. Secret passwords need to be identical on both devices (local and remote). MD5 is used in a one way hash function.
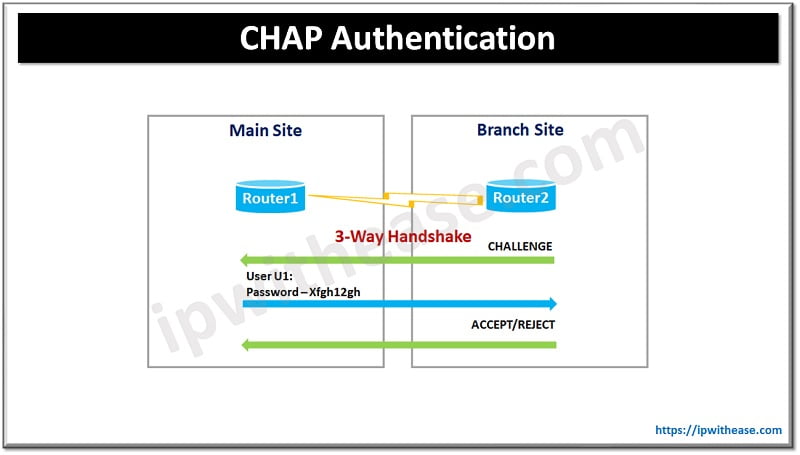
To enable CHAP use command
Router1(config-if)#username U1 password My123
Router1(config-if)#interface serial 0/0/0
Router1(config-if)#ppp authentication chap
Router2(config-if)#username U1 password My123
Router2(config-if)#interface serial 0/0/0
Router2(config-if)#ppp authentication chap
Comparison Table: PAP vs CHAP Protocols
Below table summarizes the differences between the two protocols:
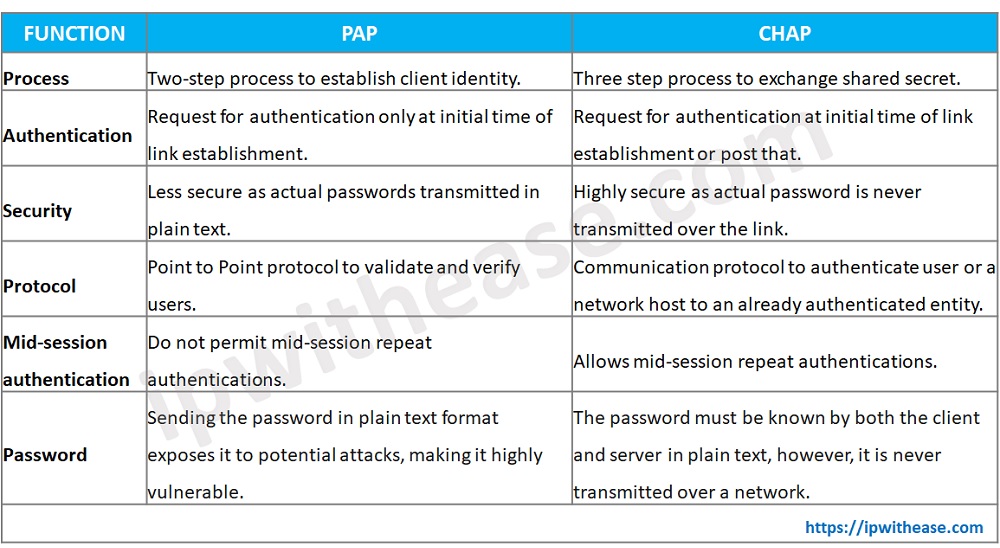
Download the comparison table: PAP vs CHAP
Advantages of CHAP Over PAP
- CHAP does not transmit the password over a network, whereas PAP exchanges the password between parties, making it highly susceptible to attacks that involve eavesdropping.
- Unlike PAP, CHAP employs periodic authentication challenges to verify that the client has not been compromised or substituted with a malicious entity.
Continue Reading:
Local & Remote Authentication in CISCO SD-WAN
Understanding AAA Authentication Login & Configuration
ABOUT THE AUTHOR

You can learn more about her on her linkedin profile – Rashmi Bhardwaj