Table of Contents:
Choosing an application security solution to invest in can be overwhelming. Will the tool you add to your infrastructure be effective? Will the solution you choose generate too many false positives? Can it be integrated with your existing developmental processes? Can it unite threat intelligence capabilities with the security solutions you already have?
There is a lot to consider when choosing such a tool. Let’s dive into the varying types of application security tools that can protect your assets.
Essential Application Security Tools
#1 Web Application Firewall (WAF)
Web Application Firewall, or WAF stands between the internet and web applications. It keeps an eye on all the incoming and outgoing traffic. In the process, it blocks the traffic flagged as malicious and allows the traffic marked as legitimate.
While WAF is an essential tool for application security, it has its limitations. That is, it can’t protect you from all the exploits out there. Most companies start with WAF and add other appropriate layers to create strong security.
As it safeguards website-based applications, it acts as a protocol layer of your defense. It’s the first line of defense that clients and popsicle cyber criminals have to surpass before they get to the server.
WAF is important because it can prevent common cyber attacks such as:
- File Inclusion and Remote File Execution
- Cross-Site Scripting (XSS)
- Brute Force Attacks
- SQL Injection
As you might have noticed, a lot of them have been listed among the OWASP’s Top Ten most common threats and vulnerabilities for web applications year after year.
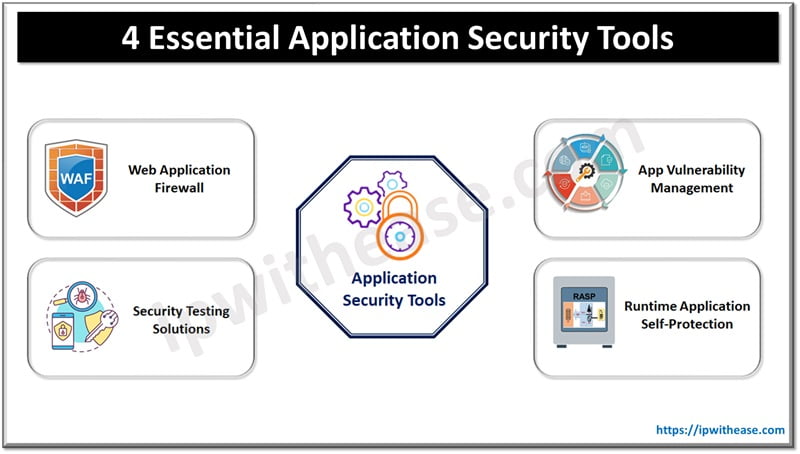
#2 Runtime Application Self-Protection (RASP)
RASP, or Runtime Application Self-Protection is another essential layer of application security. It safeguards an app from the most common vulnerabilities. How?
It’s integrated with the application you have, focusing on one app. From there, it can examine the state of the application layer security more thoroughly. During the investigation of the app security, it analyzes the data based on the context of the specific app
Since it’s focused on a single app, the number of false positives that it generates is minimal.
A major advantage of the security RASP gives you is that it tracks exploits that are both internal and external. This means that it can detect a wide range of cyber flaws and hacking attempts.
As a result, it can find the weaknesses that bypass other security solutions that you have in your arsenal of anti-hacking tools.
Types of attacks and weaknesses that this tool is designed to block are:
- SQL Injection
- API Security Threats
- Security misconfiguration
- Remote Code Execution (RCE)
- Cross-Site Request Forgery (CSRF)
RASP is great at mitigating external and internal attacks. Also, it prevents the accumulation of a large number of vulnerabilities that haven’t been addressed for too long.
#3 App Vulnerability Management
An effective security strategy stems from a well-managed one. This process is part of the basic cyber hygiene for companies. Governing has to continuously involve:
- Identification of threats and weaknesses
- Classification of vulnerabilities or possible exploits
- Prioritizing the high-risk exploits
- Patching of the discovered flaws
Vulnerability management can pinpoint which high-risk issues are threatening the system in real-time. Continual management ensures that the application is free of critical weaknesses at all times.
The tool compares your environment with databases such as the Common Vulnerabilities and Exposures (CVE) to ensure that your app is protected against the latest known flaws.
Some weaknesses are fixed automatically. Other, more sophisticated ones are reported to IT teams. Security professionals can mitigate the issue even before it escalates to a major hacking incident.
As there are often a large number of weaknesses, it’s critical to have a tool that can identify and help teams prioritize the most pressing issues.
For example, some flaws can lead to unauthorized access and leaking of sensitive data. Others don’t pose any imminent danger.
Errors in configuration and code are common and they can appear even within well-protected systems.
Understaffed teams rely on such insights to patch critical weaknesses first and other gaps in the security later. They might not have the time to address them all.
For your application, vulnerability management means that you’re one step ahead of the hackers at all times. You’re finding and fixing the weaknesses before they can even discover them.
#4 Security Testing Solutions
Security testing reveals whether your security points can defend the most important asset in the case of actual hacking. It can reveal suspicious code, damaging flaws in mobile apps, and more.
The type of application security you need to protect your assets depends on the apps you make or use. For example, some of the most common cybersecurity testing tools are:
- Interactive Application Security Testing (IAST)
- Mobile Application Security Testing (MAST)
- Dynamic Application Security Testing (DAST)
Most modern security testing solutions are automated. They can run in the background at all times to put the app to the test and uncover new flaws as they appear.
After testing, you can strengthen your application security and reduce the chance of damaging hacking exploits.
Many companies also perform traditional penetration testing. Security experts attempt to hack into parts of the system and see how well the security tools would work in a real-case scenario. Pen testers then share a report that pinpoints the weak parts of the security.
Application Security Tools Tailored to Your Needs
WAF, RASP, vulnerability management, and testing are fundamental cybersecurity points. Most companies have several different tools that work hard to protect every application layer they have.
A couple of other application security solutions and functionalities that aren’t covered here are:
- Cloud-native application protection platform (CNAPP)
- Software Bill of Materials (SBOM)
- Advanced bot protection
- API security
The exact stack of application security tools you need depends on your architecture.
It will depend on the type of technology that has to be protected from possible attacks, the kind of data that has to be guarded against data breaches, and what you can currently afford.
Continue Reading:
DAST – Dynamic Application Security Testing
Network Vulnerabilities and the OSI Model
ABOUT THE AUTHOR
IPwithease is aimed at sharing knowledge across varied domains like Network, Security, Virtualization, Software, Wireless, etc.