Table of Contents
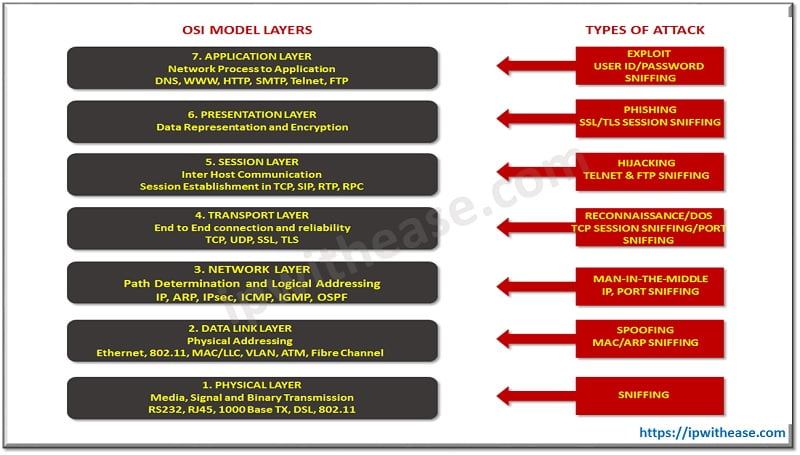
OSI model is a reference model to understand how computer networks operate and communicate. Using this ISO standard, organizations can understand where network vulnerabilities may exist within their infrastructure and apply controls appropriately. OSI is hierarchical model which supports in understanding of how packets move throughout a network and how attacks and can disrupt can occur at any level.
Network Vulnerabilities and the OSI Model Layers
Below table enlists the OSI layer, supported protocols and corresponding network vulnerabilities associated with the respective layer.
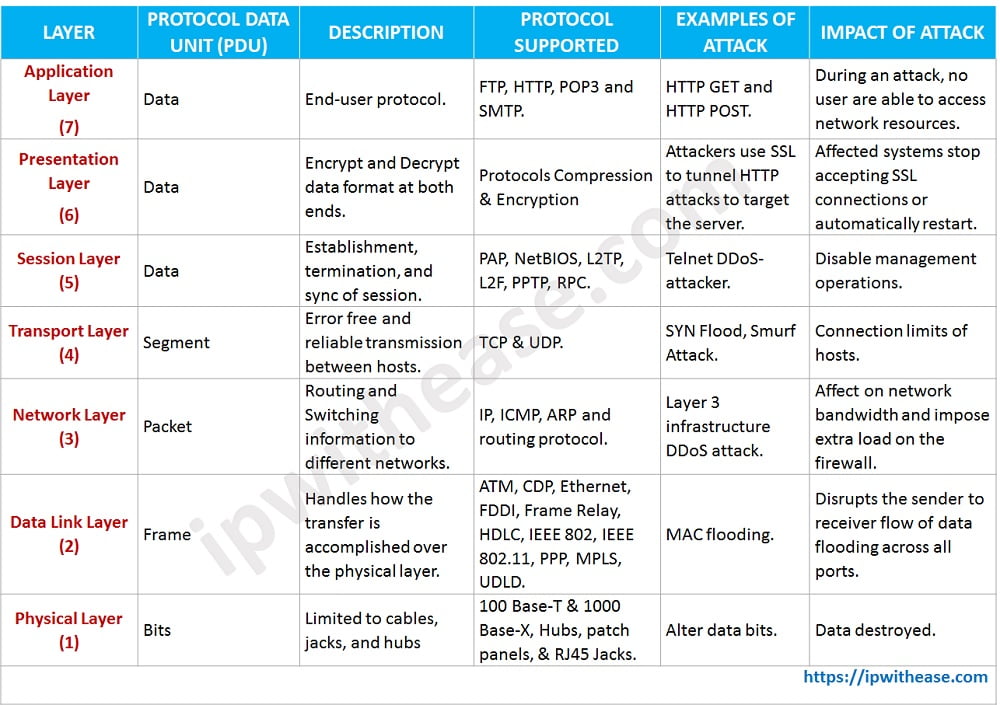
Download: Network Vulnerabilities and the OSI Model table
Why We Need Security at Each Layer of OSI Model
- Network demands security against attackers and hackers.
- Protecting confidentiality, integrity, availability of Data.
- Network Security includes two basic securities i.e. Information Security and Computer Security.
- Requires firewall for protecting systems or data from being attacked.
Top Network Vulnerabilities (Security Threats)
- Privilege Escalation
- Worm
- Virus
- Trojan
- Spyware
- Spam
- Botnet
- Logic Bomb
Related – Top 5 Data Breaches in Cyber Security
Layer 1 : Physical Layer Security
Layer 1 refers to the physical aspect of networking disrupting this service, primarily resulting in Denial of Service (DoS) attacks. Network vulnerabilities/threats which occur at this level are the following:
1) Access Control
- Permitting only authorized personnel to access.
- Physical security keeps safe from unauthorized access.
- Restricting access to critical servers and using strong passwords can prevent many attacks.
2) Damage data bits
3) Environmental issues
- Environmental issues at the Physical layer include fire, smoke, water.
- Less control over environmental factors such as temperature, humidity, dust, and ventilation can cause frequent failures.
4) Disconnection of Physical Links
5) Backup
Layer 2 : Data Link security (Switch Security)
Layer 2 of the OSI model is the data link layer and focuses on the methods of delivering frame. Normally, this consists of switches utilizing protocols such as the Spanning Tree Protocol (STP) and the Dynamic Host Configuration Protocol (DHCP). Switches provide LAN connectivity and majority of threats come from internal LAN-
1) ARPs/ARP spoofing
- ARP spoofing is targeted to rogue switch to forward packets to a different VLAN.
- Security vulnerability occurs at the lower layer of OSI model but affects upper layer security.
- To prevent these attack, configuration is performed to ignore gratuitous ARPs.
- Edge VLAN (Private VLANs) segregation and ARP inspection to mitigate this threat.
2) MAC Flooding
- MAC flooding is the attack on the network switch.
- MAC Flooding occurs when the MAC table of a switch reaches its capacity and then floods.
- A malicious user can sniff the flooded traffic to gather network sensitive information.
- Cisco switches have a port option that prevents such flooding. Configuration CLI is as below: –
- switchport port-security
- switchport port-security maximum 1
- switchport port-security violation shutdown
- Switchport port-security mac-address sticky.
- Authentication with AAA server.
3) Spanning Tree Attacks
- Occurs when an attacker inserts itself into a data stream and causes a DoS attack.
- STP attack begins with a physical attack by a malicious user who inserts an unauthorized switch. Attacker assigns a lower root priority. Assigning the lower root priority causes the network connection between two switches to be dropped. The attacker’s switch thereby becomes the root switch, and the attacker get full control to data transmitted between all switches.
- One-way of mitigating this problem is configuring a network’s root switch with Root Priority = 0.
Other Data Link attacks are –
4) Private VLAN attack
5) Multicast brute force attack
6) Random frame stress attack
Layer 3 : Network Security (Router Security)
Layer 3 is the Network layer, which utilizes multiple common protocols to perform routing on the network. Layer 3 protocol attacks consist of Internet Protocol (IP), packet sniffing and DoS attacks i.e. ICMP attacks or ping of death. These types of attacks can be performed remotely. To reduce the risk of these types of attacks, packet filtering controls should be used.
- IP Address Spoofing
- Routing attacks
- Back Hole/Selective Forwarding
1) IP Address Spoofing
- IP address spoofing is also known as IP address forgery or a host file hijack. This can be mitigated by deploying packet filtering to detect inconsistencies.
2) Back Hole
- In this attack malicious node pretends like normal node and forward packets but selectively drops some packets.
- Malicious node acts like a black hole, it discards all the packet passing through it.
Layer 4 : Transport Layer Security
Layer 4 is the transport layer and utilizes common transport protocols to enable network communication. This layer includes the Transport Control Protocol (TCP) and User Datagram Protocol (UDP). Port scanning is a method to identify vulnerable or open network port.
1) SYN Flood
- Also known as Half open attack or TCP Sync Flood.
- It includes DDoS attack on server.
- Attack involves having a client repeatedly send SYN (synchronization) packets to every port on a server, using rogue IP addresses in order to make it over consumed and unresponsive.
- Exploits TCP three-way handshake.
2) Smurf Attack
- Smurf arrack is a DoS Attack in which a system is flooded with spoofed ping messages.
- Attacker generates lots of ICMP Packets with the intended victims IP Address and Broadcasts those packets. As a result, most of devices in network respond.
Layer 5 : Session layer Security
Some of the most common attacks in this layer are –
1) Session Hijacking
- Security attack on a user session. A session hijacking attack works when it compromises the token by guessing what an authentic token session will be, thus acquiring unauthorized access to the Web server.
2) MITM Attack
- Common ways of Session Hijacking are Packet Sniffers and Cross Site Scripting (XSS Attack).
Layer 6 : Presentation Layer Security
1) SSL Hijacking
- Superfish uses a process called SSL hijacking to get user’s encrypted data. When Internet browser connects to the HTTP (insecure) site, HTTP server redirects to the HTTPS (secure) version. HTTPS server provides a certificate, this certificate provides an identification to user to get in and access to server. The connection is completed now.
Layer 7 : Application Layer Security
There are different attacks on application layer and some of them are: –
- Virus
- Worm
- Phishing
- Key Loggers
- Backdoors
- Program logic flaws
- Bugs
- Trojan Horses
Conclusion
OSI model is fundamental of understanding how networks communicate from the wire through to the application. This article has briefly looked at the OSI model, including the protocols and attacks that are utilized at each layer.
ABOUT THE AUTHOR

You can learn more about her on her linkedin profile – Rashmi Bhardwaj