Table of Contents
NSX-V to NSX-T Migration
Migrating from VMware NSX-V to NSX-T can be complex but beneficial, as NSX-T offers greater flexibility, supports multi-cloud environments, and integrates well with Kubernetes and container-based applications. In this blog, we will explore the step by step guide to migrating from VMware NSX for vSphere (NSX-V) to NSX-T.
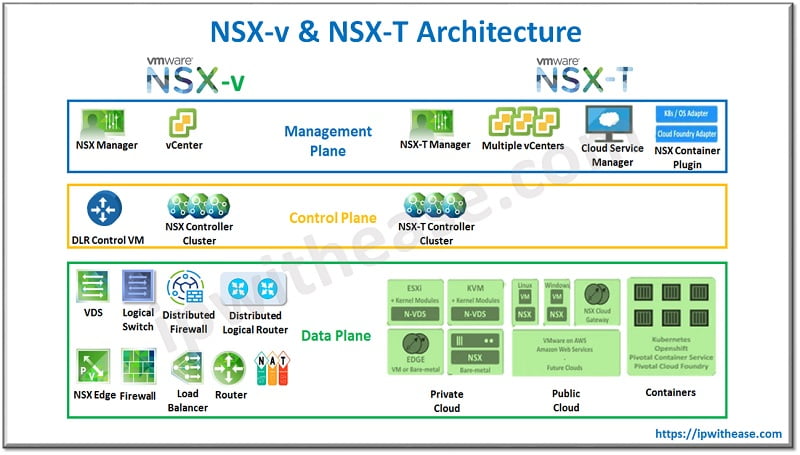
Differences Between NSX-V and NSX-T
Before exploring the migration process, lets discuss some of the major differences between NSX-V and NSX-T :
- Architecture: NSX-V is designed specifically for vSphere environments, while NSX-T supports heterogeneous environments, including multi-hypervisor and cloud-native workloads.
- Routing: NSX-T offers Tier-0 and Tier-1 routers, providing a clear separation of north-south and east-west traffic.
- Security: NSX-T has advanced security features, including distributed firewalls for containers and microsegmentation in multi-cloud environments.
- Integration: NSX-T supports integration with Kubernetes, OpenShift, and multiple cloud platforms, providing a better solution for hybrid and multi-cloud strategies.
Migrating from VMware NSX for vSphere (NSX-V) to NSX-T
1. Migration Planning
- Assessment: Begin by assessing your current NSX-V setup, including networks, firewall rules, load balancers, and VPN configurations. Identify which elements are essential to migrate.
- Compatibility: Confirm the versions of vSphere, vCenter, and NSX-T for compatibility. NSX-V to NSX-T migration is supported only from specific versions of NSX-V.
- Mapping: Map NSX-V components (logical switches, routers, firewalls) to NSX-T components. Understand how NSX-V Distributed Logical Routers (DLRs) and Edge Service Gateways (ESGs) translate to NSX-T Tier-0 and Tier-1 routers.
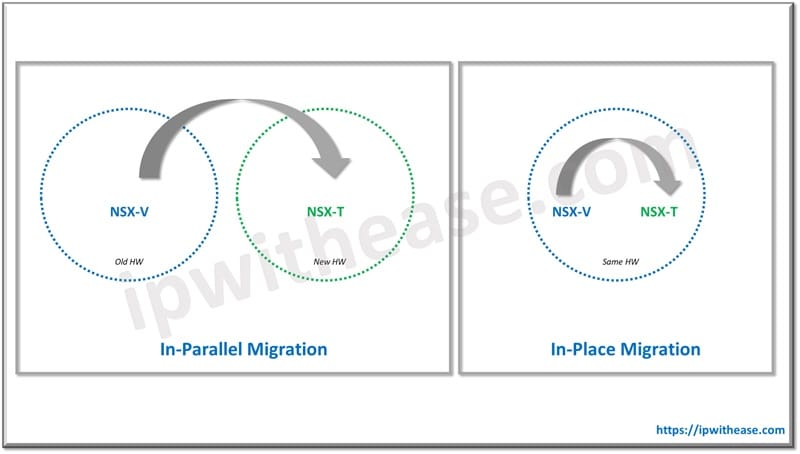
2. Migration Approaches
- In-Place Migration: This is supported by VMware’s Migration Coordinator tool, which helps automate the migration process but requires an NSX Manager upgrade to a compatible version.
- Greenfield Deployment(or In-Parallel Migration) : Deploy NSX-T in parallel with NSX-V. This is suitable if you want to gradually transition workloads to NSX-T while maintaining NSX-V operations.
- Lift-and-Shift Migration: Move workloads from NSX-V to NSX-T without retaining the old environment. This method works best for simpler network setups or environments that can tolerate temporary downtime.
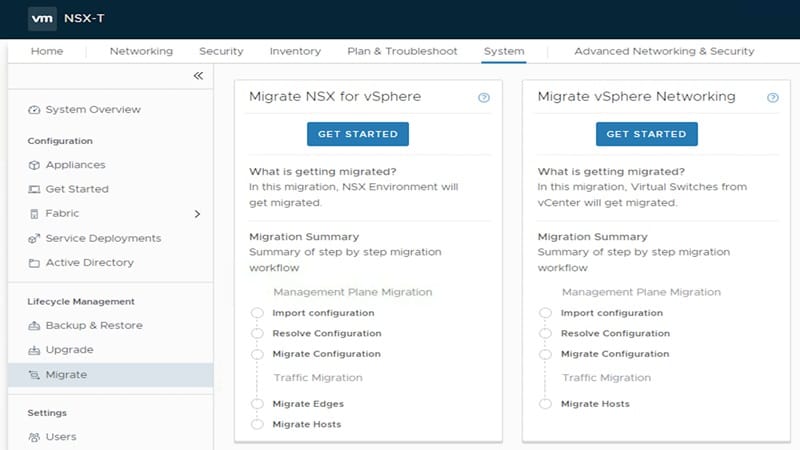
3. Migration Coordinator Tool
- VMware provides a Migration Coordinator tool embedded in NSX-T, which helps with an automated in-place migration.
- Preparation: Make sure both NSX-V and NSX-T environments meet the prerequisites for the migration. You’ll need to set up migration objects in the NSX-T environment, like transport zones and edge clusters.
- Execution: The tool allows for a phased migration approach, letting you migrate components such as the NSX-V DLR, firewall rules, and logical switches incrementally.
- Testing: Testing each migrated component is essential to verify that applications and services function as expected after the migration.
4. Network and Security Policy Translation
- NSX-T uses different constructs for security policies, which may require reconfiguration or manual adaptation of NSX-V policies.
- Microsegmentation: While NSX-V supports microsegmentation, NSX-T provides enhanced controls and options, especially for workloads in dynamic environments like Kubernetes.
- Firewall Rules and Policies: Review and update firewall rules, as NSX-T’s rule set may be more granular.
5. Operational Changes Post-Migration
- Day-2 Operations: Familiarize your team with NSX-T’s monitoring and management interfaces, which differ from NSX-V.
- Policy and Automation: NSX-T has a new policy framework and may require adjustments to automation scripts and management workflows.
- Maintenance and Troubleshooting: Understand new NSX-T troubleshooting commands and workflows, as they may differ from NSX-V’s. NSX-T provides improved tools for debugging and diagnosing network issues.
6. Testing and Validation
- Functional Testing: Ensure that all workloads, policies, and network connections are working as expected in NSX-T. Test firewall rules, connectivity, and load balancers to confirm no disruptions.
- Performance Testing: NSX-T may change network performance characteristics, so conduct performance tests to identify any issues.
- Security Validation: Verify that security policies have been applied correctly and that NSX-T’s distributed firewall functions as intended.
7. Documentation and Training
- Document all steps taken during migration to ensure clarity for future reference or rollbacks.
- Provide training to network and security teams on NSX-T’s new interface and tools, which are different from NSX-V’s.
Post-Migration Optimization
- Analyze Logs and Metrics: Use NSX-T’s enhanced logging to review network flows and adjust settings for optimal performance and security.
- Refine Security Policies: NSX-T offers more flexibility in security policy configuration. Refine policies to take full advantage of NSX-T’s capabilities.
- Monitor and Scale: Continue to monitor network performance and scalability, especially if your environment includes containerized or cloud-native applications.
Migrating from NSX-V to NSX-T enables your organization to leverage multi-cloud environments and microservices architectures. While the migration requires careful planning, it positions your infrastructure for greater flexibility, security, and scalability.
ABOUT THE AUTHOR

You can learn more about her on her linkedin profile – Rashmi Bhardwaj