Table of Contents
Monitoring of networks and systems is one of their key requirements to spot suspicious intrusions from the outside world. This is required to keep organization data and information secured from prying eyes and cyberattacks. The monitoring can be done at two levels – the host level and the network level. Both have their own benefits and limitations but both are required to protect internal systems as well as network perimeter for protection of enterprise networks.
In today’s article we will understand and compare two important concepts related to monitoring of networks and hosts using an intrusion prevention system (IPS) at Host and network level, will understand their key differences, use cases, benefits and limitations.
Related: Network Based Firewall vs Host Based Firewall
What is Host based IPS (Intrusion Prevention System)
An intrusion prevention system is host and network security hardware or software which continuously watches the network and hosts behaviour for threats. IPS is one step ahead of intrusion detection systems (IDS) which detect malicious patterns and report them for further investigation to security teams. IPS only detects malicious threats or patterns but also reports and blocks traffic from particular source, drop packets, or reset the connections. Some IPS solutions can be configured as honeypot to lure and misdirect attackers and divert them from original targets.
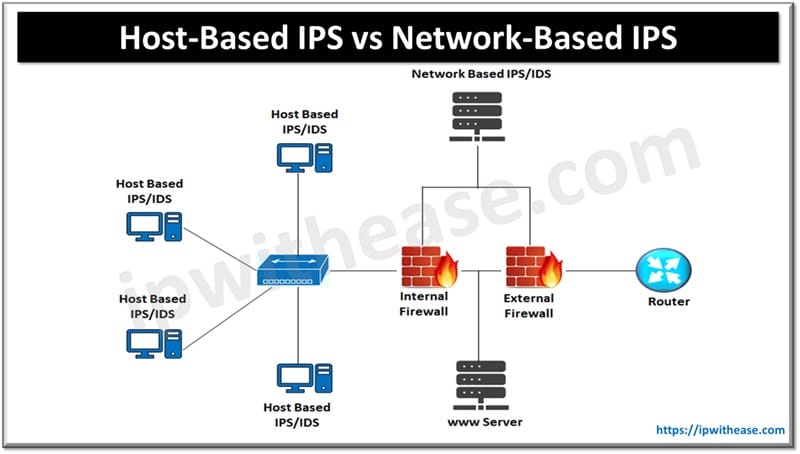
Host based IPS is installed on hosts and monitors traffic which is originating and coming to that particular host only. It also analyses the file system of host, user login activities, running processes, data integrity etc.
Pros and Cons of Host IPS
PROS
- Capability to identify if an attack was successful or not
- Monitor all user activities at the host level
- Capable of identifying attacks which originating from inside
- Can analyse and decrypt traffic to find attack signature virus
- Do not require extra hardware agent is installed on host
CONS
- Hosts are compromised as soon as server is compromised
- Could lead to performance issues on host system due to agent activity
What is Network based IPS (Intrusion Prevention System)
Network based IPS is based on your network location. They are positioned strategically on key network nodes to detect and prevent any attack on the hosts of that network segment. To capture all data passing through the network, the IPS needs to be placed at the entry/exit point of the network to the outside world. It can also be positioned at key strategic locations within internal networks. The network IPS comes in two types. Statistical anomaly IPS and pattern matching IPS. Statistical analysis model based IPS finds out user or system behaviour which is abnormal.it does profiling of every user and system during normal operations.
In pattern based IPS the IPS maintains a database of known exploits and attack patterns associated with them. During analysis of network packets if the pattern matches with one of those attack patterns then it triggers alarm and action. This kind of IPS requires every packet analysis.
Pros and Cons of Network IPS
PROS
- Ease of seeing attacks occurring across network
- Monitoring is at network level hence support not required for each OS system used in the network
CONS
- Fragmented traffic reconstruction could be an issue
- As network grows placement of IPS at one single location to capture all network traffic becomes a challenge
- Cost is increased as network grows as more sensors need to be placed
Comparison: Host-Based IPS vs Network-Based IPS
| Features | Host based IPS | Network based IPS |
| Data Source | Logs of operating system and installation application programs on host systems | Logs of network traffic generated on networks |
| Deployment | Host based IPs agent is installed on every host system which needs to be monitored. More effort required and deployment is complex as agent may vary as per installed operating systems | Network based IPS is installed on key network nodes, requires less effort and ease to deploy |
| Detection efficiencies | Numerous log processing is required, efficiency is low | High efficiency can detect attacks in real time scenarios |
| Traceability of intrusions | Process of intrusion tracking via system call paths | Process of intrusion tracking via IP address and timestamps |
| Limitations | Not meant to analyse network behaviour | Can monitor traffic passing through a specific network segment |
| Service providers | Portsentry | Realsecure, Securenet, Snort |
| Dependency | Host based IPS has dependency of type of operating system running on hosts | Network IPS has no dependency on type of operating system running on the network |
Download the comparison table: Host-Based IPS vs Network-Based IPS
ABOUT THE AUTHOR

You can learn more about her on her linkedin profile – Rashmi Bhardwaj