Table of Contents
These days, cybersecurity is a business issue as well as a technical one. Every business faces ongoing pressure to maintain system security, from safeguarding client information to adhering to legal requirements. The problem is that not all security checks are made equal.
Penetration testing and vulnerability scanning are two of the most popular techniques you’ll hear about. Both seek to expose your systems’ flaws, but they approach the task in quite different ways. You’re not the only one who doesn’t know how they differ or when to use one over the other. Let’s put it simply.
Vulnerability Scanning: What is It?
Vulnerability scanning can be compared to performing a routine auto diagnostic. It is quick, automated, and provides you with an overview of potential issues under the hood.
This is how it operates:
- An extensive list of known problems; such as out-of-date software, missing patches, or common misconfigurations; is compared to your systems by a tool.
- It quickly covers a large area, including all of your devices, apps, and network.
- It should be done on a weekly, monthly, or quarterly basis, depending on your setup.
- The final product is a report that lists possible flaws, ranks them according to severity, and offers solutions.
Why It’s Useful
- It’s efficient; you can scan hundreds of systems in one go.
- It’s reasonably priced.
- It assists in identifying issues early on before they worsen.
- It demonstrates to regulators and auditors that you are continuously keeping an eye on your surroundings.
The limitation? Although a scan can identify the locations of cracks, it cannot determine whether someone could actually enter through them.
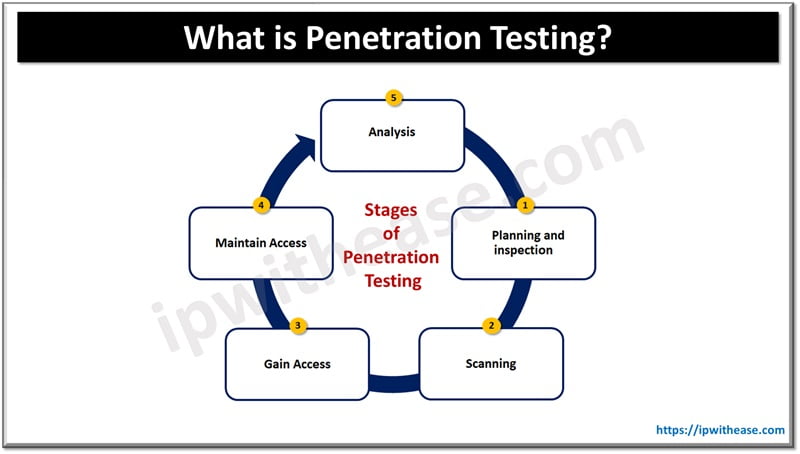
What About Penetration Testing?
Penetration testing is a test drive in which the car is purposefully driven to its limits, whereas vulnerability scanning is the diagnostic for the vehicle.
Penetration testing, sometimes referred to as ethical hacking, involves qualified security experts trying to gain access to your systems in the same way as a real attacker. Many businesses rely on customized pen test services to identify vulnerabilities that might not be obvious in automated scans.
How it’s different:
- It’s hands-on. Ethical hackers use both tools and manual techniques to probe defenses.
- It’s focused. Instead of scanning everything, pen tests usually zero in on critical systems or sensitive data.
- It’s less frequent. Many businesses conduct them annually, every two years, or following significant upgrades.
- In addition to listing issues, the report demonstrates how an attacker could take advantage of them, what information could be accessed, and the possible effects on business.
Why Pen Testing Matters
- It shows you what would really happen in an attack.
- It validates whether your security measures hold up.
- Fixes can be prioritized because not all vulnerabilities are equally dangerous.
- It increases trust with partners, clients, and auditors in regulated industries.
To sum up, vulnerability scanning finds unlocked doors, while penetration testing assesses whether a person can truly enter a door.
Comparison: Penetration Testing vs Vulnerability Scanning
| Category | Vulnerability Scanning | Penetration Testing |
|---|---|---|
| How It’s Done | Automated tools | Humans + tools |
| Depth | Broad, surface-level | Deep, real-world attacks |
| Cost | Lower | Higher (requires expertise) |
| Frequency | Frequent (weekly/monthly) | Periodic (annual/bi-annual) |
| Output | List of weaknesses | Proof of exploitation & impact |
| Who Runs It | IT staff or security team | Professional ethical hackers |
Why You Actually Need Both
This is not a binary decision. In actuality, they enhance one another.
- Continuous visibility is provided by vulnerability scans. They are excellent at identifying common problems and maintaining patch management.
- Penetration tests reveal whether those flaws have the potential to cause actual harm.
When combined, they offer the complete picture, including what is broken and what is most important in the event of exploitation.
A Quick Real-World Example
Let’s say a financial company runs a vulnerability scan. The IT staff fixes the outdated software that the scan identifies. Fantastic—issue resolved, huh?
Not quite. Afterwards, a penetration test shows that the system has inadequate access controls despite the software being up to date. Attackers can escalate privileges and obtain private client information thanks to that vulnerability.
The lesson? Although scans are useful, they don’t always capture the whole picture.
What Should You Pick?
Depending on your circumstances, yes. Consider this:
- Does your industry have any particular testing requirements, such as ISO 27001, PCI DSS, or HIPAA?
- How intricate is your system?
- What’s your budget?
- How much risk is acceptable to your company?
The best strategy for the majority of organizations is:
- To keep up with known problems, do vulnerability scans on a regular basis.
- To verify your defenses, plan penetration tests on a regular basis or following significant system modifications.
Bringing Everything Together: How Cybersecurity Is Strengthened by Scanning and Testing
Cybersecurity threats aren’t going away, and neither should your defenses. Vulnerability scanning and penetration testing are partners, not competitors. The first gives you a broad, continuous view of your environment, while the other explores in detail how attackers might exploit it.
Combining the two results in resilience development as opposed to threat response. And that’s what separates truly protecting your business from simply checking a box.
When you combine the two, you’re developing resilience rather than merely responding to threats. And that’s the difference between just checking a box and actually safeguarding your company.
ABOUT THE AUTHOR
IPwithease is aimed at sharing knowledge across varied domains like Network, Security, Virtualization, Software, Wireless, etc.