Table of Contents
In the earlier days of digital landscape, things were difficult and tiresome for administrators as managing infrastructures was a challenging and hectic job. The majority of tasks were managed manually by system administrators such as underlying hardware, software which need to be deemed fit to support application systems to work.
In recent years there is a major revolution in the field of digital IT landscape and many tools and technologies have emerged which work towards automating the process of deploying and managing IT infrastructure.
This has given rise to a new term called ‘IaC’. Infrastructure as a code or ‘IaC’ refers to a set of instructions or code written in a configuration file to build and deploy the infrastructure.
In this article we will learn more in detail about Terraform network automation tool, its working, its benefits and characteristics.
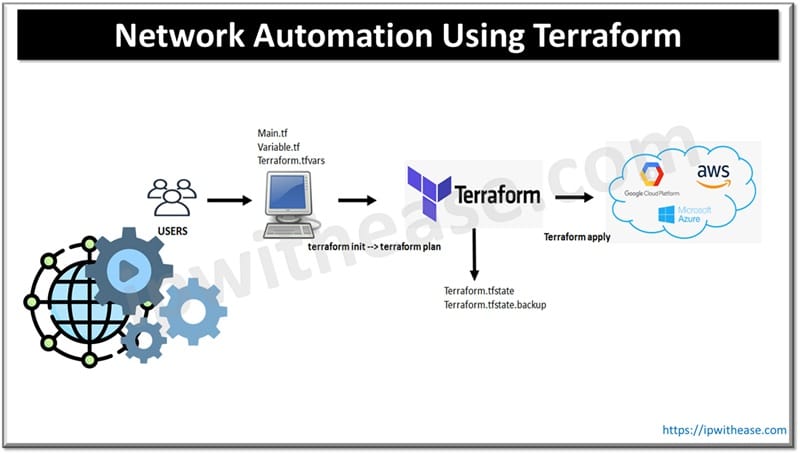
What is Terraform
There are many network infrastructure tools available in the market today in which Terraform is one of the most popular automation tools which is used for creating, changing, building and versioning infrastructure seamlessly, securely and efficiently. The configuration file will have all the code required to set up the application or build a data center. Execution plan is generated to build described infrastructure. Low level components such as compute instances and networking and high level components such as DNS, SaaS etc. both are managed by Terraform.
Features of Terraform
- It manages entire infrastructure as a code
- It manages virtual servers (AWS, Azure, Google etc.)
- It manages supporting services such as Email and DNS
- System services such as PostgreSQL, MYSQL is managed by Terraform
- It eliminates the need for manual configurations, reduction in human errors and ensure infrastructure configuration consistency across networks
Benefits of Terraform for Networks
- It automates provisioning of network components, configurations, reducing errors and improves speed
- Any changes in network configurations are recorded, they can be tracked, traced and reversible
- Network scaling becomes easier and faster as it eliminates need for individually configuring network asset instead a standard template being used
- Multi-cloud and hybrid cloud supports make it ideal for usage in diverse and enterprise network environments
Architecture of Terraform
The components of Terraform architecture comprises core, providers, configuration files and state management.
- Terraform core engine manages state, reads the configuration files and execute / apply changes
- Providers used for interacting with APIs – services such as Azure, AWS and Kubernetes
- Configuration files are in HCL language which defined required infrastructure in human readable format
- State management tracks infrastructure current setup and compares with desired state
Using Terraform for Network Automation
Terraform supports all major network vendors such as Cisco, Palo Alto, Fortinet, Juniper and others. Let’s take a typical example of a network device – firewall where configuration requires navigating thru GUI, establishing rules, and making Config changes which needs to be performed repeatedly for all firewalls. With Terraform all this can be defined in a file as code and then execute the configuration with minor changes in Terraform code before application such as firewall name.
Another benefit of Terraform is ‘state’ management as it maintains a state file which records the current state of resources, this helps Terraform in understanding what has changed since last execution thus there is no need to reapply the entire configuration. This state based configuration approach gives a clear and precise view of infrastructure which makes management and scaling easier and more efficient.
Setting up virtual network resources in a cloud such as AWS could be daunting as it takes time and effort to set up components such as VPCs, routing tables, EC2 instances and security groups. Terraform use simplifies the entire process and everything can be deployed.
Below is an example to block any-any traffic for explicit denial of all inbound and outbound traffic.
provider "aws" {
region = "us-west-1"
}
# Create a VPC (for context)
resource "aws_vpc1" "RBC1" {
cidr_block = "9.0.0.0/12"
}
# Create a Security Group that blocks all traffic
resource "aws_security_group" "block_all" {
name = "block-all-sg"
vpc_id = aws_vpc1.RBC1.id
# No ingress (inbound) rules -> all inbound blocked
# No egress (outbound) rules -> all outbound blocked
egress = []
ingress = []
tags = {
Name = "block-all-sg"
}
}ABOUT THE AUTHOR

You can learn more about her on her linkedin profile – Rashmi Bhardwaj


