Table of Contents
Phishing attacks remain top cyber security threats which puts organization information and data at the risk of exposure using deceptive emails, fake websites, and fraudulent messages. AI powered phishing detection is an innovative technology which uses machine learning and natural language processing (NLP), behavioural analytics and real-time threat intelligence which aid in detection and prevention of phishing attacks before they actualize and cause harm.
AI usage enhance filtering of emails, analysis of domain, user behaviour monitoring and makes it harder for cyber attackers to deceive the users but AI alone is not full proof to prevent phishing it should be accompanied by stronger organisation security policies, user awareness, access management and multi-factor authentication to prevent compromise of systems via this method.
In this article we will learn more in detail about how AI can be used to stop phishing attacks.
What are Phishing Attacks
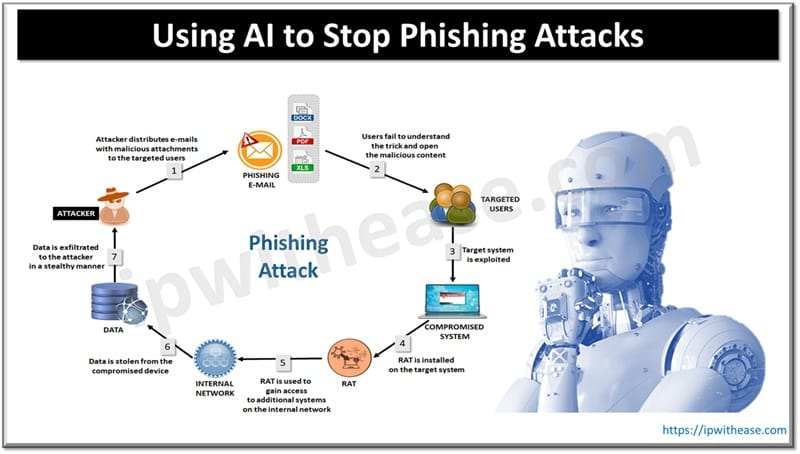
Phishing attacks are the most prevalent types of cyber-attacks which target individual users, businesses, and government institutions also. Cyber attackers send deceptive emails, create fake websites and trick users to click on them, malicious links meant to steal data such as credentials, financial data and personal details.
Phishing attacks come in various forms. Let’s look at them more in detail here.
- Email phishing is done by cyber attackers by sending fraudulent emails which appear to originate from legitimate sources such as financial institutions, social media or trusted organizations.
- Spear phishing is a kind of targeted phishing attack which uses specific details about its victim and tries to make it more authentic
- Smishing phishing is sms based phishing technique where attacks are sent via text messages containing warnings or malicious links asking its victim to take urgent action stating emergencies such as account lockout etc
- Vishing phishing uses phone calls to impersonate trusted individuals or agencies and manipulate its victim via social engineering tactics to reveal confidential details.
- Clone phishing is cloning of a legitimate email but has contents which are alerted to trick user to click a malicious link
- Whaling phishing is a targeted attack on high level executives often impersonating CEO, CFO or some senior official to trick employees in funds transfers or leak sensitive data
- Website spoofing phishing is done by creating fake websites which are near to legitimate website and trick users to visit them and disclose credentials
AI in Phishing Attacks
AI based phishing detection systems can perform vast amounts of data analysis and can detect and block suspicious activities in real-time which is not possible humanly. Let’s look at some AI techniques here used in phishing detection tools.
Pattern Recognition using Machine learning (ML)
- Analysis of millions of phishing mails, suspicious URLS and messages to identify common attack patterns
- Supervised learning models can classify legitimate and malicious emails
- Unsupervised learning models can detect new phishing techniques by identification of anomalies in messages and emails
Email Analysis using Natural Language Processing (NLP)
- Detection of fraudulent language, urgency in requests and suspicious keywords tracking and detection
- Grammatical errors, unnatural sentences and domain spoofing detection
Domain and URL Analysis
- Scanning email links and website URLs to detect domain spoofing, hidden redirections and typo squatting
- Shorten URLS and malicious domains detection
Logo and Image Recognition
- AI enabled computer vision can detect fake logs and branding used in phishing mails by comparing legit logos and fake ones
User Protection with Behavioral Analysis
- Monitoring user behaviours, sessions, keystrokes to detect phishing attacks
- On clicking phishing link AI can alert security teams or block access
Integration of Threat Intelligence
- Threat intelligence databases are used by AI to identify suspicious IP addresses, domains, websites and phishing patterns
- Real-time threat data is shared by AI powered tools to prevent large level phishing campaigns
Conclusion
Phishing attacks are a significant challenge in the cyber security landscape. AI powered phishing detection and prevention tools provide defense against persistent advanced threats by using machine learning, natural language process and real-time threat intelligence databases. AI enhances automation of phishing detection and educating users on phishing still AI alone is not fool proof to prevent phishing attacks due to involvement of human elements so it needs to be supplemented by stronger security controls around access management, user awareness and trainings
ABOUT THE AUTHOR

You can learn more about her on her linkedin profile – Rashmi Bhardwaj