Table of Contents
The IBM i platform is known for its legendary stability. But beneath that surface, many environments are quietly running on outdated or inconsistently applied Program Temporary Fixes (PTFs) – jeopardizing not just performance, but security, regulatory compliance, and supportability.
PTFs are IBM’s mechanism for delivering fixes to software defects, security patches, and updates across operating system components, licensed programs, and DB2. Yet in far too many organizations, PTF management is reactive, undocumented, and dangerously manual.
This blog dives deep into how modern AS400 support strategies can eliminate the inefficiencies and risks around PTF management, enabling enterprises to safeguard system health, accelerate issue resolution, and stay audit-ready – all without disrupting daily operations.

The Current State of PTF Management: Why It’s a Problem
PTFs aren’t optional upgrades – they are essential updates for known issues in core IBM i software. Yet many environments suffer from one or more of the following:
- PTFs applied years ago, with no tracking of current status.
- No formal schedule or policy for cumulative PTF applications.
- PTFs only applied post-incident (after a failure, vulnerability, or audit finding).
- Inconsistent application across Dev, QA, and Prod partitions.
- Manual documentation with no central inventory of what’s been applied or superseded.
This is a support risk with real-world consequences.
Why Neglecting PTF Management is a Strategic Risk
Here’s what poor PTF hygiene leads to:
| Risk Area | Consequence |
|---|---|
| Security | Unpatched vulnerabilities expose you to breaches. |
| Support | IBM support may refuse assistance for outdated OS levels. |
| Compliance | Inability to prove patch status during SOX, HIPAA, or GDPR audits. |
| Stability | System hangs, I/O errors, and corrupted jobs due to unresolved defects. |
| Upgrade Readiness | OS upgrades are delayed or fail due to missing prerequisites. |
PTF management isn’t just about being current. It’s about ensuring system integrity under changing operational conditions.
Why Many IT Teams Struggle with PTF Governance
While AS400 teams are often highly skilled, they are also stretched thin – supporting legacy systems while juggling modernization initiatives. Common barriers include:
- Lack of automated tools for PTF inventory and reporting.
- Fear of applying cumulative PTFs due to potential disruptions.
- Minimal documentation of what’s been applied, when, and by whom.
- Insufficient partition-level tracking across environments.
- Dependency on single individuals who “know where things are.”
What this creates is a fragile support model with no resilience – and no audit trail.
A Strategic Approach to AS400 PTF Management
A well-structured PTF management process should be:
- Scheduled: Run on a defined, risk-based cadence.
- Automated: Use tools/scripts to track and apply PTFs consistently.
- Documented: Maintain a central record of all PTF activity.
- Partition-aware: Ensure consistency across Dev, QA, and Prod.
- Tested: Include a defined validation window before deployment to production.
Let’s break that down further.
Core Components of a Robust AS400 PTF Management Strategy
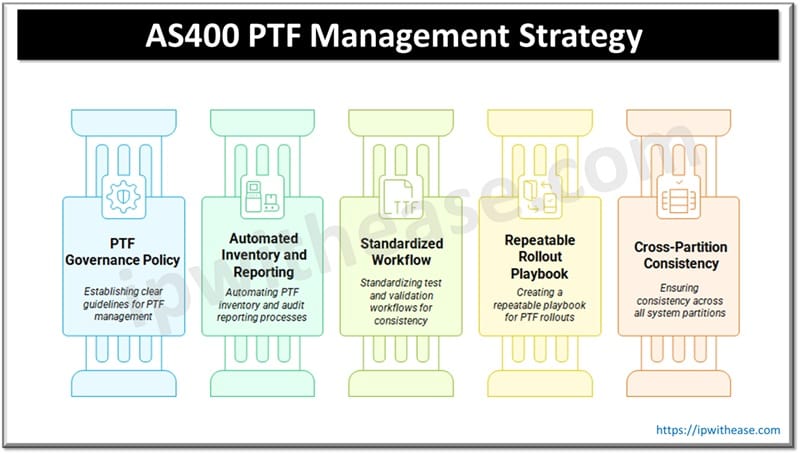
1. Establish a PTF Governance Policy
Every enterprise should have a formal PTF policy that covers:
- How often cumulative and group PTFs are reviewed (e.g., quarterly).
- Which systems are in scope and how priority is determined.
- Who is authorized to schedule, approve, and apply updates.
- How rollback and recovery plans are maintained.
Without policy, updates become discretionary, which is when critical fixes are missed.
2. Automate PTF Inventory and Audit Reporting
Manual tracking using spreadsheets is not sustainable. Consider implementing:
- PTF status check scripts that run weekly and generate logs.
- Automation tools (e.g., ACS PTF Management, iDoctor, or in-house CL scripts) to pull:
- Current OS level
- Last cumulative applied
- Missing Group PTFs (e.g., DB2, TCP/IP, Java)
- Email-based reporting to stakeholders for visibility.
This makes your PTF posture measurable and reviewable; a requirement for any well-audited environment.
3. Standardize Your Test and Validation Workflow
Fear of downtime is often what stalls PTF application. This can be addressed through:
- Validation partitions or test LPARs that simulate production.
- Scripted test cases for business-critical jobs and transactions.
- Defined observation period (e.g., 48 hours post-PTF application) before sign-off.
This builds confidence while ensuring you’re not pushing untested fixes into live environments.
4. Create a Repeatable Rollout Playbook
Every PTF application should follow a documented and repeatable process:
- Pre-checks: System backups, active job validation, IPL prep
- Deployment steps: Application using LODPTF, APYPTF, IPL
- Post-checks: Job reactivation, system log review, stakeholder confirmation
- Rollback steps (if needed): DLTPTF/restore sequence
This reduces dependency on tribal knowledge and ensures predictability.
5. Ensure Cross-Partition Consistency
It’s not uncommon for Dev and Prod partitions to be running different PTF levels – a recipe for hidden bugs and inconsistent behavior.
To solve this:
- Maintain a PTF status matrix for each environment.
- Align PTF levels during release cycles.
- Apply group/cumulative PTFs to all active partitions at the same milestone.
This ensures predictable test-to-prod transitions and simplifies support.
Best Practices to Sustain PTF Hygiene Long-Term
- Schedule Quarterly PTF Review Meetings with Ops, Security, and Compliance.
- Subscribe to IBM PTF Updates for early awareness of critical fixes.
- Document Every PTF Application, including approval, date, system, and result.
- Monitor for Superseded PTFs, especially in the case of OS-level upgrades.
- Train a Backup Resource to handle PTF management in case of attrition.
This turns PTF management into an operational rhythm – not an emergency patching exercise.
Measurable Outcomes When You Get This Right
| Improvement Area | Result |
|---|---|
| IBM Support Readiness | Faster incident resolution, no version-related delays |
| Audit Readiness | Immediate evidence of patch history and policy adherence |
| System Stability | Fewer unplanned outages tied to fixable defects |
| Operational Efficiency | Reduced manual effort in tracking and reporting |
| Security Posture | Lower exposure to known vulnerabilities |
Organizations that mature their PTF strategy not only prevent incidents – they also accelerate other modernization efforts by ensuring that the system baseline is always stable, supported, and secure.
Conclusion: PTF Management Isn’t Maintenance, But Risk Mitigation
If your organization treats AS400 PTFs as “just another IT chore”, it’s time to change that mindset. Program Temporary Fixes are foundational to:
- Keeping your IBM i environment supportable by IBM
- Preventing known bugs and security vulnerabilities
- Enabling future upgrades with confidence
- Meeting the scrutiny of modern compliance frameworks
A structured, documented, and automated PTF process isn’t a luxury. It’s a baseline requirement for any enterprise still relying on the AS400 for critical workloads.
ABOUT THE AUTHOR
IPwithease is aimed at sharing knowledge across varied domains like Network, Security, Virtualization, Software, Wireless, etc.