Table of Contents
Open Source Intelligence (OSINT) is the practice of collecting and analyzing publicly available information from a variety of sources to gain insights, assess risks, and make informed decisions. Its history can be traced back to the early days of espionage and military intelligence, but it has evolved significantly with the advent of the internet and digital technologies. OSINT sources include social media, websites, news articles, academic publications, and more.
Main uses of OSINT encompass national security, law enforcement, corporate intelligence, and competitive analysis. It aids in threat assessment, fraud detection, due diligence, and identifying emerging trends. Key features of OSINT include data collection, analysis, and visualization tools, as well as techniques for verifying information and protecting privacy.
In the future, OSINT is poised to expand further as the internet grows, offering even greater access to information. Advances in artificial intelligence and data analytics will enhance the ability to process vast amounts of data quickly. As the digital landscape evolves, OSINT will remain a vital tool for decision-makers across various sectors, helping them navigate an increasingly complex and data-rich world.
List of Best Open Source Intelligence Tools
1. NexVision
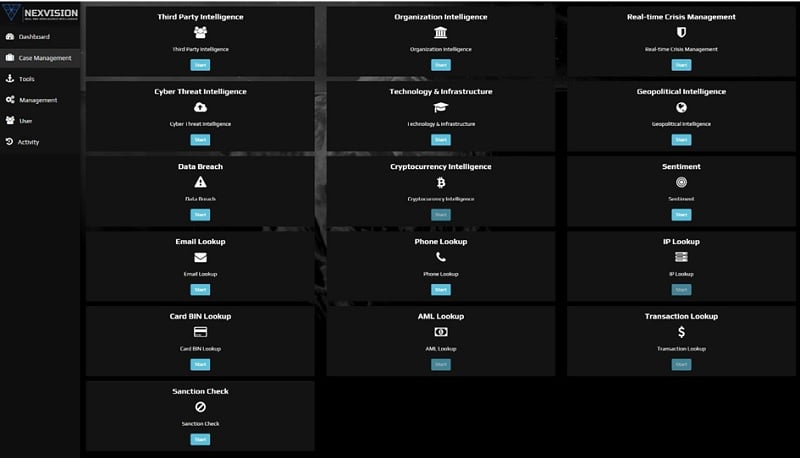
NexVision is an AI-powered OSINT tool that automates data collection and processing to drive decision-making.
NexVision stands as a game-changer in the world of open source intelligence (OSINT) tools. It’s not just a tool; it’s a powerful ally for corporations, governments’ entities, and researchers alike. Unlike its counterparts, NexVision boasts unparalleled comprehensiveness, offering the most extensive open source intelligence (OSINT) data collection from the surface and dark web, including a vast social media data lake.
What sets it apart is its utilization of cutting-edge artificial intelligence (AI) technology, which meticulously sifts through data to eliminate false positives, ensuring users access the most precise and reliable intelligence available.
Objective
- Provide accurate, timely, and actionable intelligence that empowers teams throughout the organization to make faster, more accurate decisions and amplify their impact — from security operations, compliance, incident response, fraud prevention, risk analysis, and threat monitoring.
OSINT Tools Features
- DARK Web Search Engine: NexVision’s dark web search engine is a game-changer, offering automated, in-depth exploration that goes beyond superficial landing pages. Utilizing cutting-edge technology, it reaches deep into authenticated, marketplace, and account-level sources, providing unparalleled access and invaluable insights for security, intelligence, and research applications.
- Real-time Crisis Management, which specializes in real-time crisis alerts. This module employs advanced technology to deliver timely alerts and comprehensive analysis during critical events. It caters to users seeking immediate, reliable information to make informed decisions in crisis situations. NexVision’s Intelligence Module is a valuable tool for staying updated and responding effectively to emerging crises.
- Geopolitical Intelligence, provide cutting-edge solutions for organizations seeking in-depth geopolitical insights. They offer real-time analysis, trend monitoring, and predictive intelligence to aid decision-makers in understanding global events and risks.
2. Social Links

Social Links, a software company, specializes in AI-driven solutions that extract, analyze, and visualize data from diverse open sources, including social media, messaging platforms, blockchains, and the Dark Web.
Their flagship product, SL Professional, empowers investigators and data security professionals by enhancing their efficiency in achieving work objectives.
SL Professional boasts a comprehensive suite of custom-designed search methods, spanning over 500 open sources. These advanced search queries, some leveraging machine learning, enable users to filter data effectively during collection.
But Social Links OSINT solutions go beyond data gathering; they also offer advanced analysis tools that refine information throughout investigations, providing accurate results for a clearer, more comprehensive understanding of the case.
Product Features
- A professional bundle of 1000+ original search methods for over 500 open data sources including all major platforms across social media, messengers, blockchains, and the Dark Web
- Utilizing machine learning for advanced automation, it swiftly retrieves a wide spectrum of information, ensuring precise results at impressive speeds.
- Bespoke analysis tools enable data to be significantly enriched and molded to the user’s particular purposes
- Seamless integration within any IT infrastructure
3. Maltego
Maltego OSINT, short for “Open Source Intelligence,” is a powerful and versatile data analysis tool designed for gathering and visualizing information from various publicly available sources on the internet. It’s particularly valuable for digital investigations, threat intelligence, and cybersecurity purposes.
Maltego enables users to connect, aggregate, and analyze data points from a wide range of online platforms, including social media, websites, DNS records, and more, helping users uncover hidden relationships, patterns, and insights. Its intuitive graphical interface and data visualization capabilities make it an essential tool for professionals seeking to conduct in-depth investigations and research in the digital realm.
Features
- Maltego enables users to generate visual graphs, depicting a wide array of entities including individuals, organizations, domains, IP addresses, and many others.
- Maltego integrates with numerous data sources, including public data sets, social media platforms, DNS records, online services, and more.
- Maltego assists in the automatic generation of links between entities, facilitating the identification of connections and relationships based on collected data.
- Maltego supports collaboration among users by allowing the sharing of graphs and collected data.
4. Recon-ng
Recon-ng is an open-source reconnaissance framework primarily utilized for information gathering and web reconnaissance in the realm of cybersecurity. Developed in Python, it provides a powerful and extensible platform for security professionals and penetration testers to automate the process of collecting, analyzing, and organizing data from various online sources, including search engines, social media, and public databases.
Recon-ng offers a wide range of modules and plugins that facilitate the discovery of valuable information such as subdomains, email addresses, vulnerabilities, and network infrastructure details. Its flexibility allows users to customize and extend its functionality, making it a valuable asset in ethical hacking, vulnerability assessment, and digital forensics.
Recon-ng simplifies the complex task of reconnaissance by providing a structured and efficient approach, helping security experts uncover critical insights and vulnerabilities in their target environments, ultimately contributing to better-informed decisions and enhanced cybersecurity defenses.
Features
- Modular Architecture: Recon-ng’s modular architecture allows users to easily extend its functionality. It provides a wide range of pre-built modules for tasks such as DNS enumeration, subdomain discovery, and email harvesting. Users can also develop custom modules tailored to their specific needs, making it highly adaptable to different reconnaissance objectives.
- Automated Data Gathering: Recon-ng streamlines the process of collecting information from diverse sources, automating tasks that would otherwise be time-consuming. Its modules can fetch data from search engines, social media platforms, public databases, and more. This automation not only saves time but also ensures consistency and thoroughness in data collection.
- Data Organization and Analysis: The framework excels at organizing and presenting the gathered data in a structured manner. It provides tools to analyze the collected information, helping users identify patterns, vulnerabilities, and potential attack vectors. Recon-ng’s reporting capabilities make it easier to communicate findings effectively to stakeholders.
- Customization and Extensibility: Recon-ng is highly customizable, allowing users to tailor their reconnaissance efforts to the specific requirements of a project. Security professionals can modify existing modules or create new ones, adapting the tool to evolving cybersecurity challenges and ensuring it remains a versatile asset in their toolkit.
5. SEON
SEON Identity verification through cross-referencing social media and online platform accounts is gaining prominence for compelling reasons. It erects a formidable barrier against fraudsters deterred by the effort and resources required to fabricate profiles. Moreover, this approach offers a comprehensive view of an individual’s digital presence and can provide insights into their socioeconomic status, especially in regions with limited financial data access.
Additionally, the choice of social media connections can offer valuable cues about a person’s identity, making it a multifaceted tool for confirming and understanding individuals’ authenticity.
Features
- Fraud Deterrence: One of the primary features is its effectiveness in deterring fraud. This high barrier to entry discourages fraudsters from attempting to deceive the verification process, enhancing overall security.
- Digital Footprint Analysis: By cross-referencing various online accounts, this method compiles a comprehensive digital footprint of the individual.
- Socioeconomic Insights: In regions where financial data is limited or unavailable, analyzing linked social media and online platform accounts can provide valuable socioeconomic insights
- Identity Validation: helps organizations and platforms confirm the authenticity of users and minimize the risk of identity theft or fraudulent activities.
Continue Reading:
How can Blockchain Technology be used?
What Is Threat Hunting? Everything You Want to Know
ABOUT THE AUTHOR
IPwithease is aimed at sharing knowledge across varied domains like Network, Security, Virtualization, Software, Wireless, etc.