Introduction
Data is Wealth in today’s digital world. Every site should maintain its database in order to study its consumers, Ad Sense, promotion, and for many other reasons. Thousands of websites and applications are affected by Blind SQL injection and there is a high risk of data theft and manipulation. Here is how it works
What is Blind SQL injection?
When a site or application is vulnerable to SQL injection, and the attacker is unable to see the server response to the injection or query, it is called Blind SQL injection. To understand it better, you should know what SQL Injection is.
SQL injection is the attacking technique, where attackers insert a malicious SQL statement (query) in the entry field as an input. Attackers use it to exploit security vulnerability, steal, and alter data. It is the oldest and common form of cyber attacks and is mostly used to attack websites, but it can be used to exploit any SQL Database.
In the case of Classic SQL injection, the attacker can see the response of his SQL query through the error but, in the case of Blind SQL injection, the attacker is blind to the output of the SQL injection. It makes the SQL injection process difficult and time-consuming but not impossible.
How does it work?
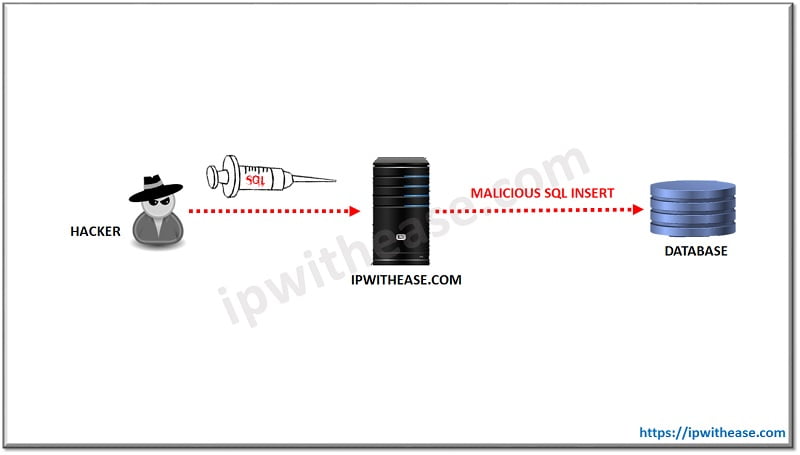
Before getting started, you should understand how the website and database work. All the details of the user of a website are stored in the database. SQL is the language used to store, retrieve, and delete data. Here is an example for you.
Let’s say a user enters his login credentials in the site (user Id and password). Now the SQL code acts and checks the details entered with the database. If it matches, it retrieves the data of the particular user shows it to him. In other words, he is allowed to log in.
Now let us see how the attackers use the SQL injection to get access to your account. The attackers enters the malicious SQL string in the User Id field. The server reads the input as SQL code instead of as an input. Now the server would show the error. By this, the attackers will know that the site is vulnerable to SQL injection.
But web server administrators realize showing errors to the general public is not a good choice. So the servers stopped showing errors. However, it doesn’t get rid of the vulnerability.
Attackers came up with the new technique called Blind SQL injection, where the attacker can still know whether the site is vulnerable to SQL injection even without the error messages. The Blind injection is operated in two ways, they are content-based and time-based.
- In content-based, Blind SQL injection the attackers ask true or false questions to the database through the SQL queries. If the website response is true, then it means the site is vulnerable to SQL injection.
- In time-based SQL injection, the attackers analyze the site’s response time by making the database performing time-intensive. If the website does not respond immediately then the site is vulnerable to SQL injection.
After, they make various requests or command to the server through the input field to exploit the server database. Sometimes SQL injection attack is executed with other cyber attacks like DDoS.
Consequences of Blind SQL Injection Attacks
- The attackers can steal sensitive user details, including login credentials, credit card numbers, and other personal information. It allows the attackers to impose as the user. And he can make payments and take action in his name.
- The attackers can read, add, update, alter, or delete the data or tables from the site database or execute an administrative command.
- Through SQL injection one can gain completed control over the web applications/operating system of the server.
How to prevent Blind SQL injection?
- Irrespective of the language and web development platform used, the administrator should use strong and follow the secure coding guidelines of OWASP.
- Use Parameterized queries instead of dynamic queries as they read the input as a separate string instead of the SQL code.
- Inputs should be filtered and checked. Whitelist all the special character use.
- It is better to use input encoding.
- Ensure no use of illegal characters in the input field.
- Encrypt all the database
- Minimal privileges and Strict access to control
- Continuous and effective scanning
SQL injection helps in spoofing identity, tampering data, and leads to reputation loss. In a recent study, an average web application received 4 attack campaigns per month. And the retail and e-commerce application received twice as many attacks as other industries.
Continue Reading:
What is CSRF Attack? – Cyber Attack
ABOUT THE AUTHOR

You can learn more about her on her linkedin profile – Rashmi Bhardwaj