Table of Contents
A buffer overflow occurs when more data is written to a buffer than it can hold, causing data to overwrite adjacent memory. Data is stored temporarily during program execution in a physical space or RAM in computer memory often referred to as ‘Buffer’. Buffers help in optimizing application performance, boost storage access and so on. Buffers are used in a variety of ways by applications such as during live video streaming buffering is used to prevent disturbance during network latency.
While streaming some part of the video is stored in a buffer and played from there. At times if more data is pushed to the buffer then the capacity it can hold the situation of ‘buffer overflow’ arises resulting in overwriting neighbouring memory locations.
The hackers can take advantage of this ‘buffer overflow’ limitation and launch an attack by supplying custom into an application, when the application tries to store the input into the buffer it overwrites the space meant to store executable code. The piece of code can be changed by a hacker by replacing executable code and changing the way the application will work.
Changed code / application becomes hacker code.
In this article we will learn about buffer overflow terminology, how buffer overflow attacks work, and their types, how to prevent buffer overflow attacks?
What is Buffer Overflow
Buffer overflow is a condition where buffer space cannot hold the amount of data being pushed to it due to which it throws data out of the buffer space or window. This process leads to application crashes and data corruption. Attackers often take advantage of buffer overflow issues and overload the system with malicious code to take control of applications to trigger actions and instructions. Arbitrary code is pushed into a web application stack which corrupts it and then the hacker takes the control of the application. Buffer space is a memory area which holds data. When more data is input then the capacity of the buffer overflow occurs. Hackers overwrite memory locations, modifying application execution paths.
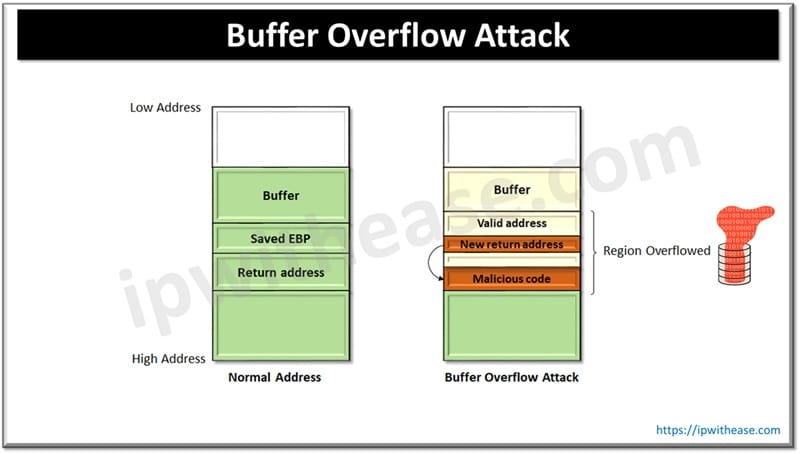
How Buffer Overflow Attack works
When a program writes more data to memory than the expected capacity it can hold hackers force applications to launch arbitrary code with a valid user input. The arbitrary code will crash the application and its control is taken over by the hacker. The hacker writes the memory locations or buffer of the executable program with its own malicious code and changes the way the program should work.
Usually buffer overflow attacks are targeted towards web applications which heavily use archives in web applications. Heap Overflow Vulnerability CVE-2021-22045 in VMWare Products is a classic example of buffer overflow vulnerability.
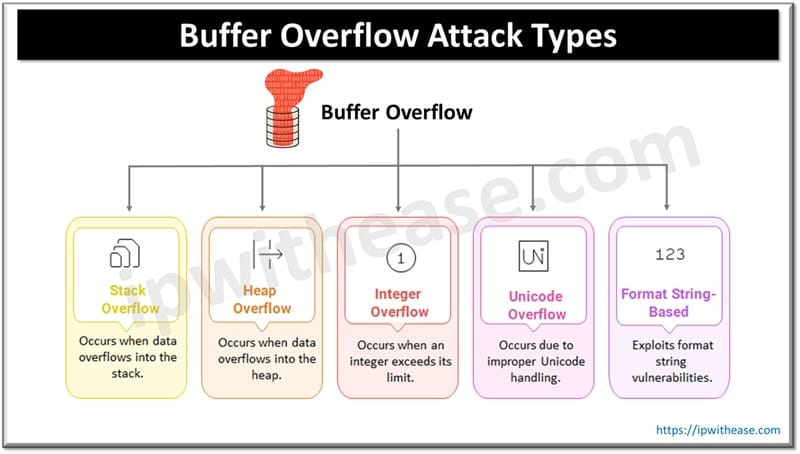
Types of Buffer Overflow Attacks
Stack Overflow
Data held in stack is corrupted and attackers overwrite memory locations which affect the pointer or data. Stacked memory vulnerability in C. C++ memory create pointer which execute arbitrary code as this is susceptible to system exploitation
Heap Overflow
Data written without checking the memory allocation for heap. Critical functional tables can be overwritten which are held in heap
Integer Overflow
This is an arithmetic overflow issue where integer is not stored in an allocated area in the memory or buffer. It could provide unexpected results as integers have a specific number of bits in memory and overflow causes inaccurate behavior such as financial manipulations.
Unicode Overflow
Transcription issues are handled by Unicode strings for any languages used in the program. This attack exploits improper handling of multi-byte Unicode characters, causing buffer overflows. It can lead to memory corruption, crashes, or remote code execution.
Format String-Based
A format string overflow attack occurs when untrusted input is unsafely used in functions, thereby allowing attackers to read or write memory. It can lead to information leaks or code execution.
Prevention of Buffer Overflow Attacks
There are certain ways in which buffer overflow attacks can be addressed as under:
- Address Space Randomization – technique randomizes memory address space locations for program executables, libraries etc to prevent exploitation of memory-based vulnerabilities by hackers. Address space randomization makes it difficult for hackers to identify the location of executable code without which an attack will not be successful.
- Data Execution Prevention – Certain areas of memory or buffer are flagged as ‘non-executable’ or ‘executable’ to prevent attackers from launching attacks.
- Structured exception handler overwrite protection – Management of software and hardware exceptions is taken care of by SEM by design. It prevents hackers from using SEH exploitation.
ABOUT THE AUTHOR

You can learn more about her on her linkedin profile – Rashmi Bhardwaj