Google ADs
Table of Contents
Importance of Cloud Security
Cloud security is a critical aspect of modern technology infrastructure, given the growing reliance on cloud services by businesses and individuals. Some of the key reasons to understand the importance of why cloud security are:
- Protection of Sensitive Data: Many organizations store sensitive data, such as customer information, financial records, and intellectual property, in the cloud. Strong cloud security measures ensure that this data remains confidential, preventing unauthorized access, breaches, and leaks.
- Compliance and Legal Obligations: Various industries are subject to regulatory requirements like GDPR, HIPAA, and PCI DSS, which mandate stringent data protection standards. Ensuring proper cloud security helps organizations maintain compliance and avoid legal penalties.
- Mitigation of Cybersecurity Threats: The cloud is a frequent target of cyberattacks, including data breaches, DDoS attacks, malware, and ransomware. Implementing robust cloud security measures, such as firewalls, encryption, and intrusion detection systems, helps mitigate these risks.
- Business Continuity: Cloud security helps ensure business continuity by protecting against data loss due to security incidents, natural disasters, or hardware failures. Disaster recovery plans and data backup strategies within the cloud are vital for minimizing downtime.
- Cost Efficiency: A data breach or loss can result in significant financial costs, including fines, legal fees, and the cost of rebuilding trust with customers. Proactive cloud security minimizes these risks, saving organizations from financial losses.
- Control Over Access: Cloud environments often involve multiple users and devices. Cloud security enables businesses to manage who has access to which resources through identity and access management (IAM) systems, reducing the risk of internal or external unauthorized access.
- Visibility and Monitoring: Strong cloud security practices provide better visibility into user activity and system operations. Monitoring tools detect unusual behavior or potential vulnerabilities, allowing businesses to take preemptive actions against security threats.
- Flexibility in a Hybrid or Multi-Cloud Environment: Many organizations operate in a hybrid or multi-cloud environment. Effective cloud security ensures consistent protection across various platforms, whether public, private, or a mix of both, without creating security gaps.
- Trust and Reputation: A security breach can severely damage a company’s reputation, causing customers and partners to lose trust in the business. Maintaining high cloud security standards reassures stakeholders that their data is safe and handled responsibly.
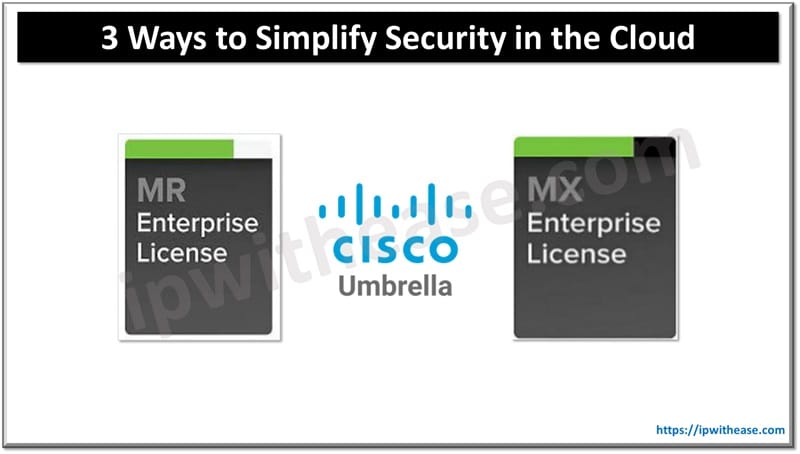
Ways to Simplify Cloud Security
Here are three ways to simplify security in the cloud using Cisco Meraki MR, Cisco Meraki MX, and Cisco Umbrella:
1. Unified Cloud Management for Network and Security (Meraki MR & MX)
- Meraki MR Access Points and Meraki MX Security Appliances are fully cloud-managed via the Meraki Dashboard, offering a single interface for both network and security management.
- With the Meraki Dashboard, administrators can:
- Easily configure security policies, content filtering, and firewall rules.
- Manage multiple sites and devices from one centralized dashboard.
- Utilize integrated security features, such as intrusion detection/prevention (IDS/IPS), threat protection, and auto VPN with a few clicks.
- This integration simplifies the security management of both wireless (MR) and wired (MX) networks, removing the need for separate tools and interfaces.
2. Integrated Threat Intelligence with Cisco Umbrella
- Cisco Umbrella provides DNS-layer security and Secure Internet Gateway (SIG), offering proactive protection by blocking malicious traffic before it reaches the network.
- By integrating Umbrella with Meraki MX, internet-bound traffic is automatically filtered through Cisco Umbrella’s threat intelligence platform, blocking malicious domains, IPs, and URLs.
- This setup enables simplified policy enforcement across distributed networks, reducing the complexity of configuring security rules across multiple locations. Policies are applied dynamically, ensuring consistent protection regardless of where users are accessing resources.
3. Automatic SD-WAN Security and Traffic Prioritization (Meraki MX & Umbrella)
- Meraki MX appliances offer built-in SD-WAN capabilities, allowing secure and optimized routing of traffic between branches and cloud environments. When integrated with Cisco Umbrella, it provides seamless cloud security for all internet-bound traffic, regardless of location.
- SD-WAN policies can automatically prioritize critical traffic, such as SaaS applications or VoIP, while routing less important traffic through secondary connections.
- With Umbrella SD-WAN Connector, you can dynamically route traffic through Umbrella’s secure web gateway based on application type, reducing the need for complex manual configurations and ensuring consistent cloud security across different traffic types.
These solutions work in tandem to reduce the complexity of managing security across different network components and cloud environments, streamlining administration while providing strong protection against cyber threats.
Google ADs
ABOUT THE AUTHOR

Founder of AAR TECHNOSOLUTIONS, Rashmi is an evangelist for IT and technology. With more than 12 years in the IT ecosystem, she has been supporting multi domain functions across IT & consultancy services, in addition to Technical content making.
You can learn more about her on her linkedin profile – Rashmi Bhardwaj