ACL (Access Control List) – A method of keeping in check the Internet traffic that attempts to flow through a given hub, router, firewall, or similar device. Access control is often accomplished by creating a list specifying the IP addresses and/or ports from which permitted traffic can come. The device stops any traffic coming from IP addresses or ports not on the ACL.
ARP – Address Resolution Protocol (ARP). A network protocol that is used to convert IP addresses to physical network addresses by sending an ARP broadcast to request the address
AH – Authentication Header – Part of the Internet Protocol Security (IPsec) protocol suite, which authenticates the origin of IP datagrams and guarantees the integrity of the data.
BYOD – Bring your own device – The authorised use of personally owned mobile devices such as smartphones or tablets in the workplace.
DMZ – Demilitarized Zone – A DMZ is commonly provisioned between a corporate network and the internet where data and services can be shared/accessed from users in either the internet or corporate networks. A DMZ is established with network firewalls to manage and secure the traffic from either zone. The name is derived from the term “demilitarised zone”.
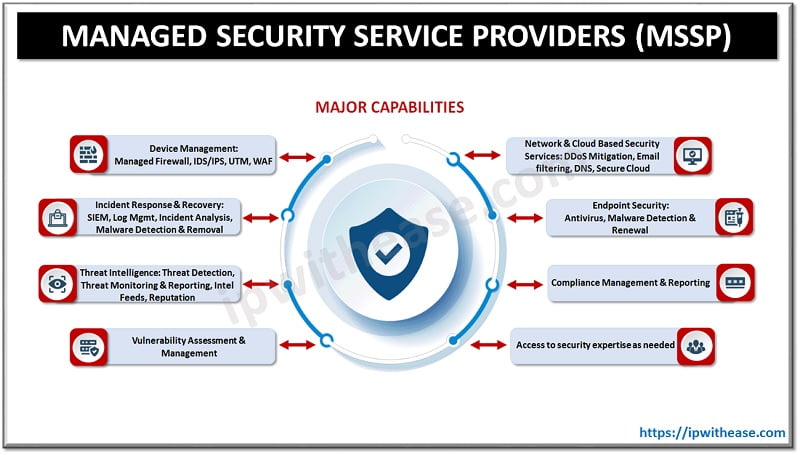
Firewall – Hardware or software Security system designed to prevent unauthorised access to a network from another computer or network.
ISP – Internet service provider – Service Provider that provides access to the internet and related services.
IDS – Intrusion detection system – Program or device used to detect that an attacker is or has attempted unauthorised access to computer resources.
IPS – Intrusion prevention system – System that also blocks unauthorised access when detected.
IKE – Internet Key Exchange – IKE establishes a shared security policy and authenticates keys for services like IPSec that require security keys. Before any secured (over IPSec) traffic can be passed, each VPN Gateway must verify the identity of its peer. This can be done by manually entering pre-shared keys into both hosts .
IPSec – IP Security – A framework that provides data confidentiality, integrity and authentication between IPSec peers. IPSec uses IKE to address the negotiation of protocols and algorithms based on local policy and to generate the encryption and authentication keys to be used by IPSec.
NAC – Network Access Control – NAC is a security approach that strengthens the security of a secured network by restricting the availability of network resources to endpoint devices that comply with a defined security policy of the organization or group.
RADIUS – Remote Authentication Dial In User Service – RADIUS is a networking protocol that provides centralized access, authorization and accounting management for users to connect and use a network service. When a person or device connects to a network ,”RADIUS” authentication is required as part of security control.
Phishing – Method used by criminals to try to obtain financial or other confidential information (including user names and passwords) from internet users, usually by sending an email that looks as though it has been sent by a legitimate organization (often a bank). The email usually contains a link to a fake website that looks authentic.
Proxy server – Proxy is terms used for device which sits between an end system and remote server and acts as a mediator. The client requesting the resource connects to the proxy server and once validated proxy connects to remote server and provides the requested content to the client.
VPN – Virtual Private Network – A VPN is a computer network that uses public telecommunication infrastructure such as the Internet to provide remote offices or individual users with secure access to their organization’s network.
Backdoor – A design fault, planned or accidental, that allows the apparent strength of the design to be easily avoided by traffic manipulation.
Certificate – An electronic document attached to someone’s public key by a trusted third party, which verifies that the public key belongs to a legitimate owner and has not been compromised. Certificates are intended to help you verify that a file or message actually comes from the entity it claims to come from.
CA – Certificate authority – A trusted third party who verifies the identity of a person or entity, then issues digital certificates vouching that various attributes (e. g., name, a given public key) have a valid association with that entity.
Encryption – The process of disguising a message to make it unreadable by humans. The resulting data is called ciphertext.
Event logs – A log of user actions or system occurrences which help in auditing and getting security breach.
Hacker – A user who breaks into sites for malicious purposes.
MD5 – MD5 is one of series of message digest algorithms which involves appending a length field to a message and padding it to a multiple of 512-bit blocks. Each of these 512-bit blocks is fed through a four-round process to result in a 128-bit message digest.
NAT – Network address translation – NAT hides internal IP addresses from the external network. When a firewall/Router is configured to provide NAT, all internal addresses are translated to public IP addresses when connecting to an external source.
Public-key encryption – A cryptographic system that uses two keys, public key known to everyone and a private or secret key known only to the recipient of the message.
RSA – A standard for public-key cryptosystems named after its inventors, Ron Rivest, Avi Shamir, and Rick Adleman . Its security is based on factoring very large prime numbers. The size of the key used in RSA is completely variable, but for normal use, a key size of 512 bits is common. The RSA algorithm is based on the fact that there is no efficient way to factor very large numbers.
SSL – Secure Sockets Layer – A technology embedded in Web servers and browsers that encrypts traffic.Its an Encryption technology for the Web used to provide secure transactions, such as the transmission of credit card numbers for e-commerce.
Stateful Inspection – A term 1st introduced in CheckPoint which allows a firewall to analyze packets and view them in context. (Also called stateful multi-layer inspection)
BOTNET – A botnet is a collection of internet-connected devices, which may include PCs, servers, mobile devices and internet of things devices that are infected and controlled by a common type of malware. Users are often unaware of a botnet infecting their system.
ABOUT THE AUTHOR

You can learn more about her on her linkedin profile – Rashmi Bhardwaj