Table of Contents:
In the fast-paced realm of cybersecurity, staying ahead of constantly evolving threats is a perpetual challenge. Over the recent months, the landscape has witnessed remarkable innovations reshaping how we defend against cyber threats. From cutting-edge technologies to novel approaches, let’s explore some key advancements bolstering our digital defenses.
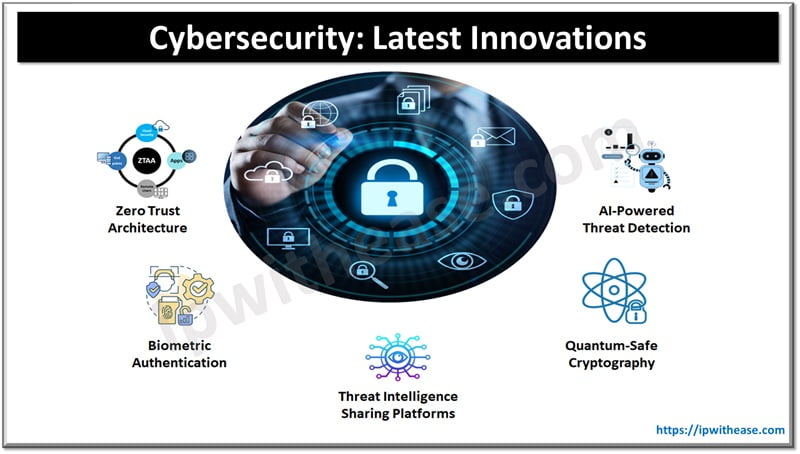
List of Latest Innovations in Cybersecurity
Zero Trust Architecture
Traditional security models centered around the notion of a secure perimeter, assuming that once inside, all was safe. However, the surge in remote work and sophisticated cyber threats demanded a reevaluation. Enter Zero Trust Architecture—a paradigm shift that advocates for continuous verification of every user and device. By eliminating implicit trust, organizations can significantly reduce their attack surface and enhance security in an era where boundaries are increasingly blurred. Seeking guidance from an expert cyber security consultancy will help to navigate these cutting-edge advancements effectively with the best knowledge that you could hope to be armed with.
AI-Powered Threat Detection
Artificial Intelligence (AI) has become a linchpin in modern cybersecurity. Machine learning algorithms analyze vast datasets to identify patterns and anomalies, enabling early threat detection. Advanced AI systems excel at distinguishing normal behavior from potential threats, offering a proactive defense mechanism against evolving risks. This innovation is instrumental in preventing data breaches and fortifying overall cybersecurity posture.
Biometric Authentication
The inadequacies of traditional passwords have led to the rise of biometric authentication, which is quickly taking over two-factor authentication. Technologies like facial recognition, fingerprint scanning, and behavioral biometrics provide a more robust and user-friendly alternative to quickly access the required data, making it more secure than other means. By incorporating unique biological traits into the authentication process, organizations can thwart unauthorized access attempts, offering a higher level of security in an age where data breaches are a constant concern.
Quantum-Safe Cryptography
The advent of quantum computers poses a looming threat to conventional encryption methods. Acknowledging this vulnerability, researchers have been actively developing quantum-safe cryptography. These cryptographic algorithms are designed to resist attacks from quantum computers, ensuring the continued confidentiality and integrity of sensitive information. As quantum computing technology advances, the integration of quantum-safe cryptography is crucial for future-proofing our digital defenses.
Threat Intelligence Sharing Platforms
In the spirit of collective defense, threat intelligence-sharing platforms have gained prominence. These platforms facilitate real-time information exchange about emerging threats among organizations. Members can fortify their defenses by pooling knowledge and resources and proactively responding to potential risks. Collaboration within the cybersecurity community has proven to be a powerful strategy for staying ahead of the rapidly evolving threat landscape.
Conclusion
As cybersecurity continues to evolve, innovation remains paramount in the ongoing battle against cyber threats. The highlighted advancements represent a snapshot of the progress made in recent times. Looking forward, the cybersecurity community must maintain its vigilance, fostering collaboration and pushing the boundaries of innovation to stay ahead of malicious actors. With these continued advancements, people can navigate the ever-changing digital landscape, ensuring the interconnected world remains secure and has a resilient future in the long term.
Continue Reading:
Microsegmentation vs Zero trust- What’s The Difference?
Top 5 Data Breaches in Cyber Security and Possible Preventative Measures
ABOUT THE AUTHOR
IPwithease is aimed at sharing knowledge across varied domains like Network, Security, Virtualization, Software, Wireless, etc.