Table of Contents
Being able to login and to gain access to corporate resources is one of the most important part of every company’s IT setup. In this post we will understand concept of AAA, its framework, and commonly used protocols.
What is AAA?
AAA (Authentication, Authorization, and Accounting) is a framework used in computer security, networking, and access control to manage user access and monitor usage. It consists of three key components:
- Authentication
- Authorization
- Accounting
If users are logging into the network through VPN network or connecting to a command line of a switch, a AAA framework is essential to connect. The first step in using AAA framework is to verify the identity and validity of a user which is called as Authentication.
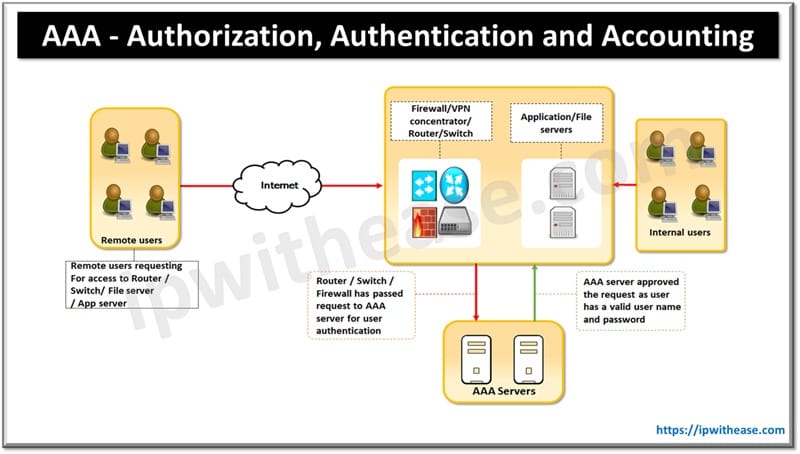
Let’s take an example – We try to retrieve package from the post-office where we need to produce our identity to prove as intended recipient. In same way, in networking world our identification could be a username and password, an SSL certificate or a combination of these.
- Without Authentication, an administrator could never control user (or Machine) access to network and related resources. Sometimes authentication and authorization may be confusing to understand as both are closely related.
- Authentication is when you are trying to log into Router/Switch or any system using your credentials (username/Password/ RSA token/ Finger Prints) by any authentication method.
- After system authenticates (access to enter the system is approved/granted) next, it verifies its internal database to see what resources we are permitted to access and what we have requested.
- If the requested resource matches with what has been permitted, this is what we call authorization. Same way when a user is allowed to view only configuration of devices and not allowed to enter configuration mode.
AAA Framework
- Authentication – Verifies a user’s identity (e.g., username & password, biometrics, tokens)
- Prove you are who you say you are
- Password and other authentication factors
- Authorization – (Determines what actions or resources the user is allowed to access)
- Based on your identification and authentication, what access do you have?
- Accounting – (Tracks user activities, such as login times, data usage, and commands executed)
- Resources used: Login time, data send and receive and logout
There are various type of Authentication Method, Lets focus on the some commonly used Methods
- Form Username and password but can also be a PIN code or something else
- Smartcard or Physical token
- Physical attribute (a biometric)
- Multi Factor authentication or two factor authentications (combining password authentication and security tokens)
Commonly Used Protocols
There are several different types of Centralized authentication technologies and protocols available. Some of commonly used protocols are:
- RADIUS (Remote Authentication Dial-In User Service) – Common in ISP and enterprise networks.
- TACACS+ (Terminal Access Controller Access-Control System Plus) – Used by Cisco and provides more granular control than RADIUS.
- Diameter – A modern replacement for RADIUS with enhanced features.
RADIUS vs TACACS
Both the protocols provide the communication between your network devices (for access) and AAA servers. Let’s further understand the difference between Radius and TACACS protocols –
| Parameter | RADIUS | TACACS |
| Abbreviation for | Remote Authentication dial-in user service | Not real time |
| OSI Layer | layer 4 transport protocol | layer 4 transport protocol |
| Connectionless / Connection oriented | Connectionless | Connection oriented |
| Protocol and Port numbers | Uses UDP ports: 1812/1645 (Authentication) 1813/1646(Accounting) | Uses TCP port 49 for Authentication and accounting |
| Encryption | Encrypt only the passwords | Encrypt full payload of each packet |
| AAA component separation | Combines authentication and authorization | Separates all 3 elements of AAA, Making it more flexible |
| Logging | No command logging | Full command logging |
| Security | Less secured | More secure |
Download the comparison table: radius vs tacacs
ABOUT THE AUTHOR

You can learn more about her on her linkedin profile – Rashmi Bhardwaj