Table of Contents
Cybersecurity threats are advancing at an unprecedented speed in the modern world. Organizations are constantly under threat, and cybercriminals are in search of vulnerabilities they can exploit to gain access to sensitive information. As business operations become more technology-dependent, the drive for tight security becomes more urgent. One of the greatest ways to secure a network is through automated penetration testing. This advanced method not only enhances security postures but also ensures continuous vigilance and protection against potential threats. Following cybersecurity best practices is essential for organizations to protect their assets effectively.
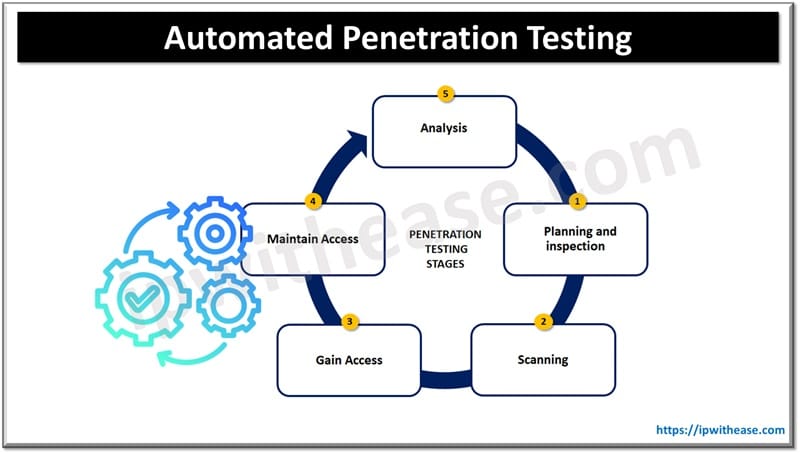
What is Automated Penetration Testing?
Penetration testing, or ethical hacking, is a proactive approach taken to identify and exploit vulnerabilities in a network, system, or application before it can be accessed by malicious attackers. In the past, penetration testing was an activity done manually, often a point-in-time exercise by cybersecurity professionals. With rising cyber threats and the IT environment growing with complexities daily, automated penetration testing has been considered an efficient and effective solution.
Automated penetration testing automatically emulates the process of a real-world attack, constantly using the most advanced tools and technologies. This approach helps identify security vulnerabilities in real time, ensuring that the response for their elimination is rapid. Through this process automation, a penetration test not only provides organizations with an understanding of their security posture but also helps them save on time and resources.
Benefits of Automated Penetration Testing
- Continuous Monitoring and Protection: Automated penetration testing provides continuous monitoring compared to traditional penetration testing, which is done once or at the most twice a year. This means that when vulnerabilities are discovered, they can be addressed at the time of discovery, thus narrowing down the window within which cybercriminals might exploit weaknesses. For organizations looking to enhance their security operations through continuous monitoring, integrating automated security operations can further strengthen their cybersecurity strategy.
- Cost-Effective Solution: Manual penetration testing may prove to be expensive and time-consuming, especially for large organizations with complex networks. Automated penetration testing reduces this excessive manual work and provides a cheaper alternative to allow cybersecurity teams to focus on more important strategic actions.
- Scalability: An organization keeps growing; the environment of a company is dynamically changing with increased complexities. Automated penetration testing solutions are scalable enough to fit in smoothly, covering wide coverage across all systems and applications.
- Accuracy and Consistency: One of the basic concerns with manual penetration testing is human error. Automated solutions do away with this risk because they provide consistency and accuracy in results, ensuring that no vulnerability is overlooked.
- Detailed Reporting and Compliance: Automated penetration testing tools provide detailed reporting, which highlights vulnerabilities, potential impacts, and recommended actions for remediation, helping organizations improve their security postures and meet regulatory requirements.
Implementation of Automatic Penetration Testing
Automated penetration testing is a strategic move for businesses looking to advance their cybersecurity defenses. It provides organizations with a complete solution containing both continuous and automated capabilities in penetration testing in real time for detecting and responding to vulnerabilities.
The right platform ensures that the company is well prepared for a cyber incident through network resilience against potential threats. And helps organizations to understand their security gaps by exposing them to real-world tactics, techniques, and procedures used by an attacker, which in turn allows these organizations to take proactive measures to better defend themselves. This increases confidence among stakeholders that data and assets are being secured within the network.
How IP Management Can Apply Automated Penetration Testing
Intellectual property, IP, is one of the most valuable assets to any organization. Cyber threats pose a great challenge to IP protection and, therefore, maintaining competitive advantage and ensuring long-run business success. Automated penetration testing plays a major role in IP management by identifying vulnerabilities that potentially lead to unauthorized access to highly classified information.
For any organization that processes IP, automated penetration testing is the technology layer that can improve safety for the technology, pharmaceuticals, and manufacturing sectors. It protects one’s trade secrets, patented technology information, and proprietary data from theft or corruption. This is of tremendous importance for maintaining the organization’s market position and reducing financial damage related to the theft of its IP.
Best Practices in Implementing Automated Penetration Testing
To maximize the benefits of automated penetration testing, organizations should follow these best practices:
- Interoperability with existing security infrastructure: Make sure that the automated penetration solutions are inter-operating with the existing security systems and processes for this integrated monitoring and management of vulnerabilities.
- Regularly update testing parameters: Cyber threats are dynamic; hence, the testing parameters need to be regularly updated. This should ensure that the organization is well-prepared to counter new and evolving threats by updating testing tools and methodologies.
- Work with Cybersecurity Experts: Automation delivers great benefits, but human expertise is key. Collaboration with cybersecurity experts is necessary during the analysis and design of effective remediation strategies. For more insights on enhancing your team’s skills and staying updated on the latest cybersecurity trends, consider exploring advanced techniques for cybersecurity upskilling.
- Prioritization of Vulnerabilities Based on Risk: Not all vulnerabilities are risky in nature. Use automated penetration testing to assess the vulnerabilities that might reap more often than not and hold the potential of getting exploited.
Conclusion
Automated penetration testing provides proactive and efficient protection for organizational networks and intellectual property, which are under the threat of growing risks in cybersecurity. Companies using automated tools will have adequate 24/7 protection at reduced costs while maintaining a strong security posture.
The strategies that are developed to counter these cyber threats, too, need to evolve. Automated penetration testing is not only about technological development but also about a strategic necessity for organizations that are serious in safeguarding their digital assets and intellectual property.
ABOUT THE AUTHOR
IPwithease is aimed at sharing knowledge across varied domains like Network, Security, Virtualization, Software, Wireless, etc.