Table of Contents
A dictionary attack is a type of cyber attack used to break passwords or encryption keys by systematically trying every word in a predefined list (called a dictionary) of likely passwords. This attack relies on the assumption that most of the users choose simple predictable passwords. Password compromises account for 81% of breaches due to weak or stolen passwords. ‘Weaker passwords’ are the easiest target for compromises and are favourite sport for hackers.
In dictionary attacks hackers attempt to break-in by guessing passwords using common dictionary words and their variants. The dictionary as the name suggested for this attack is derived from mostly commonly used words such as pet names, fictional characters, or for that matter any words from the dictionary used as password. At times some alphabets and names are converted into special characters such as “p@ssword”.
This kind of attack not just target online accounts but also the commonly shared files among a group of people that often have simpler easy to remember passwords.
In this article we will learn Dictionary attacks, how dictionary attacks work and what preventive measures can be taken to address dictionary attacks.
What is Dictionary Attack
In a dictionary attack, hackers try to enter the target system using a set of commonly used passwords, the aim is to find accounts with weak passwords so the system can be compromised without the account lock-out detections. A bot is used to launch a dictionary attack which uses commonly used “dictionary words” on a single or multiple systems/ accounts. This is considered an exhaustive technique to compromise a system or account.
It is a sort of brute force mechanism that aims to get into the system or account by exploiting weaker passwords. During online dictionary attacks their potency is limited by latency but in offline mode there is no such constraint and once hacker gets access to login password they get into the system undetected. Some typical examples of dictionary passwords are “Password123” or “iloveyou“.
Characteristics of a Dictionary Attack
- Target: Passwords or cryptographic keys
- Method: Attempts each word in a dictionary file as a possible password
- Speed: Faster than brute-force attacks because it tries only likely candidates instead of all possible combinations
- Effectiveness: Depends on the strength and unpredictability of the target password
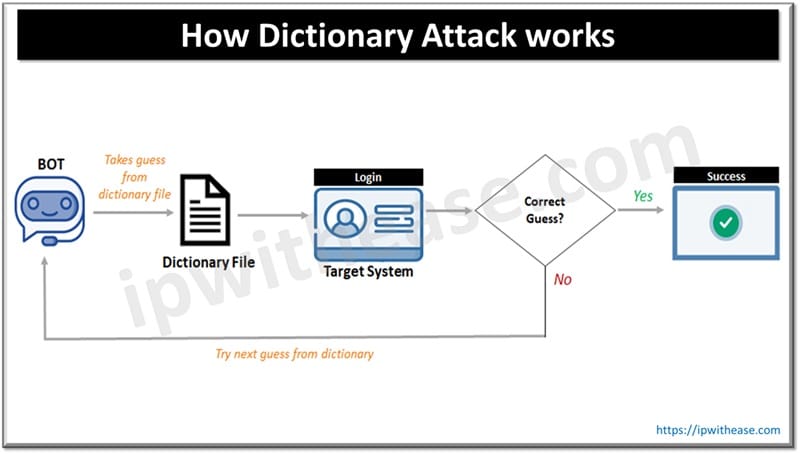
How Dictionary Attacks work
To launch a dictionary attack hacker acquires a dictionary file having lots of words, potential commonly used passwords and phrases. These are available for download online or can also be created using online free tools for password generation.
- An automated program launches the attack by feeding these passwords one by one into the target system, impersonating as if a legitimate user is trying his/her password to gain system access.
- If account password and dictionary password is a match then system or account control is with the hacker.
- Hacker applies a set of passwords to a single user account, if that fails it will try changing the user name and apply a set of passwords to that user.
How to Protect Against Dictionary Attacks
Enhanced Password Security
Using a long and complex password which is distinctive for each of the accounts helps to improve password security posture. Password generator tools can be used to create a strong password, which is unique and tough to guess due to its complexity with the use of uppercase, lowercase, special characters and numerical use.
Multi-factor Authentication
Password security can be enhanced with the combination of multifactor authentication where one additional verification step is assigned which could be a randomly generated number or code sent on authenticator app or as SMS over mobile phone.
Account Lockout Settings
Enforcing account lockout policy at domain level with group policy settings such as wrong password max 3 attempts and account lockout provides protection against dictionary attacks
Alerting and Monitoring
Tracking attempts to login-ins and log-outs provide a useful insight into a suspected dictionary or other types of password attacks. If a hacker is trying multiple passwords on a single or multiple accounts, a sudden increase in network traffic can give meaningful insight into this kind of attack. Alarms or alerts can be set to intimate administrators so that mitigating actions such as blocking traffic from malicious IP from which such requests are getting generated can be blocked.
ABOUT THE AUTHOR

You can learn more about her on her linkedin profile – Rashmi Bhardwaj