Table of Contents
Introduction to Brute Force Attack
A “brute force attack” is a method where trial-and-error is used by hackers to guess a person’s user name, password, credit card number or cryptographic key. They try to use all the available combinations that will provide the best results. The excessive force means the persistence of these tries that can take from seconds to many years.
This kind of method, is being used for many years in the past trying to resolve long and complex passwords but is still effective and popular on today’s hacker community.
Categories – Methods of Brute Force Attacks
The most common categories for of a “Brute Force Attack” are the following:
- Dictionary Attacks: In this method, automated tools are used, which utilize dictionary databases in order to predict the correct information. The dictionary can also be a file, where information are stored by the user. In this way the chances of a successful attack increase significantly.
- Search Attacks: In this method, the main idea is to try all the possible combinations of a set of characters and all the numerical range of a full password length. This kind of method can take considerable amount of time due to mathematical dependency.
- Rule-Based Search Attacks: In this method, the idea is to create possible password variations from an existing username part. It also applies in guessing existing mask-words in the input of a menu frame.

Brute Force Attack Tools
They are many Brute Force Attack tools on the web. Most of them are for windows and linux operating systems. We did a small research on some of the most popular attacks tools and found the following:
- Aircrack-ng: When it comes to Wi-Fi security, there is no 100% safety for most of the users. Aircrack-ng is a very sophisticatel tool to crack passwords from ordinary Wi-Fi routers. It uses the very 1st method described earlier, called Dictionary Attack.
- LophtCrack: Another very commonly used tool for cracking mainly Windows passwords is being created with the name LophtCrack. The method used in this tool is also Dictionary Attack, including a few more advanced techniques such as scheduling and HAS extraction.
- Ncrack: This tool has been created to perform Brute Force Attacks, especially for cracking network authentications. It has the advantage of being used in MAC OS operating systems and utilizes various protocols, such as HTTP,POP3, FTP and Telnet.
Related – Cyber Attacks and their types
Mitigation from Brute Force Attacks
In the Cyber security community many people have been working and invented different solutions on how to prevent Brute Force Attacks. The most popular are the following:
- User Account Lockdowns: This method is very simple and it is used after many unsuccessful login attempts. The system or the server locks down any login process in order to avoid a Brute Force Attack. The advantage of this method is that the Administrator usually doesn’t have to unlock from Active Directory for so many users on the domain every 15 minutes or so.
- Two-Factor Authentication: Another very sophisticated method in security community for avoiding Brute Force Attacks especially on money transaction websites, such as online-banking, PayPal, etc. The main concept is to enable a second password on the mobile phone or to a secondary email address. The Hacker doesn’t instantly have the access to the network carrier or to a secondary POP3 server and he/she will cancel the process.
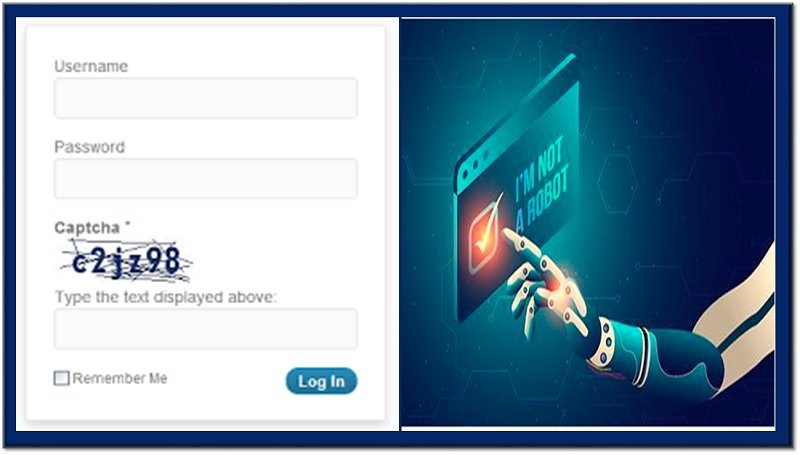
- CAPTCHA Authentication: This particular method is used on most of the web sites today. It is very effective against bots and automated machines. It includes simple steps where the user is required to enter a specific word like number of traffic lights on a generated picture etc., resulting in a highly intelligent and treacherous mechanism for hackers.
Conclusion
Brute force attacks are commonly used nowadays and its essential to inform that users should consider this type of attack seriously and try to avoid and protect themselves at all cost. Large organizations are dealing with Cyber security and hire computer scientists to create complex defensive mechanisms to deal with them. The future will be safer if everybody is keeping private information safe, so the Dictionary Method possibilities are reduced or extinguished. Another encouraging fact is that most government cyber security facilities have been created around the globe which provide many reliable services and everybody should feel comfortable to contact them via the local Police Department.
ABOUT THE AUTHOR

You can learn more about her on her linkedin profile – Rashmi Bhardwaj