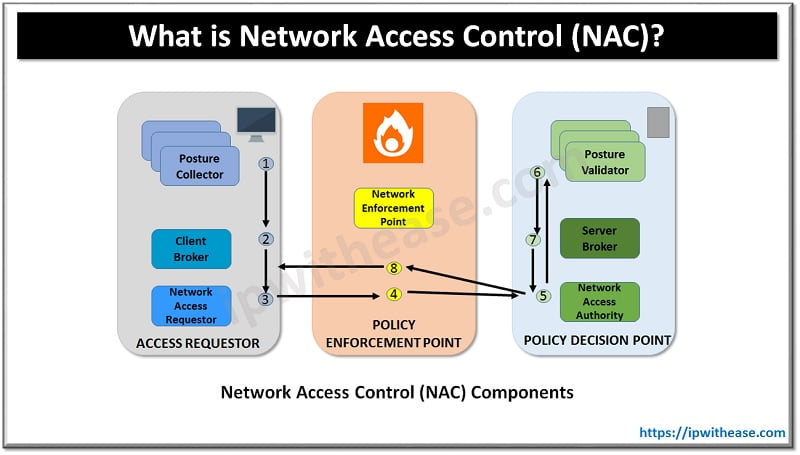
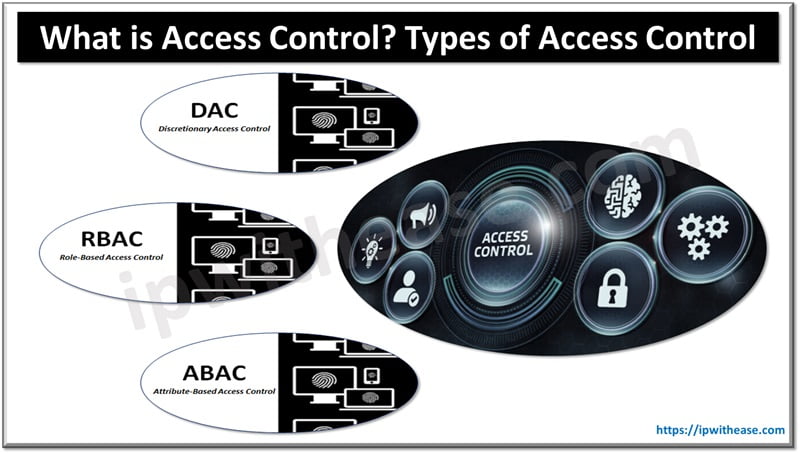
Table of Contents
The safeguarding of sensitive information has become an important concern for enterprises, governments, and institutions as the world becomes more connected. Insider threats, however, introduce a special issue for ensuring the safety of information. Many of these hazards come from within, either by men or carelessness. That’s where insider risk management plays a role, providing solutions designed to help reduce these risks while safeguarding important data.
The Insider Threat Is Growing
Insider threats for a long time have been seen as one of the most challenging problems in cybersecurity. External threats might be more visible, but internal threats can sometimes pose even greater risk. These risks stem from the very people who have the right to access an organization’s systems and data. Insiders can be employees, contractors, business partners, or anyone else who has authorized access to sensitive data.
In a 2020 report, Ponemon Institute reported that insider threats are becoming increasingly severe, and said 60% of data breaches were linked to insiders. This is a sobering statistic that points to the necessity of strong insider threat systems aimed at prevention, detection, and response towards threats within an organization.

Insider Threat Solutions: Preventing Data Breaches from the Inside
In the battle against insider threats, businesses have to implement a layered security strategy that incorporates data-centric strategies. Insider threat technologies may be available in different forms, ranging from tools to human resources solutions. With that in mind, here’s an outline of the most effective approaches for protecting sensitive data:
1. Implementing Access Control Policies
The principle of least privilege is one of the cornerstone principles in insider risk management. Access should be restricted so that only those people who need to feel trusted can access the data and systems; doing so will dramatically decrease the surface area for policy abuse. Access controls, like role-based access control (RBAC), go a long way to ensure sensitive data is kept away from unauthorized users. Apart from restricting access, organizations must also routinely re-evaluate and update access rights to ensure that staff, contractors, and partners all have only the necessary level of access at any given point in time. This is particularly important for larger organizations where roles often change between employees, or a team member may leave the organization altogether.
2. Monitoring User Activity
The key to discovering potential insider threats is consistent monitoring of user behavior. With the support of user and entity behavior analytics (UEBA) systems, companies can isolate out-of-the-ordinary or dangerous behaviors that signal potential bad actors. A suspicious activity could be if an employee is accessing sensitive information after hours or downloading a large amount of data.
By monitoring in real time, organizations can catch insider threats before they expose proprietary information and keep the damage minimal from those engaged in malicious activity. This keeps fraud/theft in check and also can identify employees needing additional training on security polices.
3. Data Loss Prevention (DLP) Technologies
Data Loss Prevention (DLP) technologies are another aspect of insider threat management. These types of tools are programmed for tracking and managing the flow of confidential information over the wire. DLP systems prevent the exchange of sensitive information with unauthorized devices or external systems to prevent protected data from leaving the organization.
For example, if one of the company’s workers attempts to send sensitive financial information through email to an external address, this DLP can either stop the action or produce an alert for the security department to check. This kind of preemptive tracking can help prevent data loss and a breach that is brought on by someone internal, whether knowingly or accidentally.
4. Employee Training and Awareness Programs
While technology is a critical part of insider threat solutions, human behavior often plays a pivotal role in the success of these strategies. Insider threats aren’t always the work of bad people; they are often a result of poor practices and carelessness. You will definitely have to train your employees to meet these types of risks.
Companies should have regular awareness programs teaching staff on topics like malicious emails, social engineering techniques, and the appropriate use of sensitive information.” Employees should also know what happens when data security policies are not adhered to. Skilled people are going to be less likely to undertake risky activities that could see you compromise sensitive data.
5. Creating a Culture of Security
Aside from individual training, companies must create a security culture that extends throughout the business. In other words, leadership needs to make security a paramount consideration throughout the organization from decision-making to everyday operations. A starting point for developing a culture of security is where employees understand that protecting data is everyone’s responsibility, not just the IT or security department.
Companies may also promote reporting of perceived suspicious activities by employees through these secure avenues. This enables employees to safely report potential threats and helps organizations to respond immediately and shield themselves from experiencing devastating security breaches.
Tackling Insider Threats: A Preventive Stance
And while most companies have some form of response plan, proactive action is the solution to mitigating insider threats. The name of the game for insider threat management revolves around recognizing, understanding, and neutralizing potential threats before they can do widespread harm. Here are some ways for companies to take a more preventive stance in protecting sensitive data:
1. Creating an Insider Threat Policy That is Clear
The first step to reducing threats is to have a well-defined insider threat policy. This policy should clearly include examples of threatening conduct and provide a reporting mechanism for it to be addressed. It should also spell out the key players, outline roles and responsibilities for HR, IT, legal, and security teams.
Properly written into an insider threat policy, such in-depth tools will ease the process of identifying areas of potential risk for businesses to act on before a vulnerability is exploited. It also serves as a reminder and makes EMPLOYEES realize that it is crucial to adhere to the security guidelines of the organization, and they can be penalized in case of non-compliance.
2. Performing a Frequent Review of Who is Accessing the Data
Regular audits are a critical part of any successful insider threat program. Data access logs, audit trails, and user permissions should be monitored periodically to look for anomalies and unauthorized activities. Frequent reviews can expose unforeseen risks and verify that all data access practices are consistent with those established security policies.”
Organizations should also invest in continuous monitoring technologies that automatically alert on suspicious or unauthorized access events. Such tools can deliver early warnings and enable security teams to act quickly on potential threats.
3. Collaborating with Third-Party Experts
Many organizations turn to third-party experts for help with developing insider risk management plans. They can secure cloud apps with 3rd party vendor advanced threat detection and assist enterprises when it comes to deploying best practice mitigations for insider threats. They can also perform comprehensive security reviews and recommend actions for better control internally.
Working with third-party providers can also improve an organization’s capacity to identify and respond to insider threats, and ultimately keep pace with developing vulnerabilities.
Conclusion: Being Prepared for Insider Threats
The practice of managing insider risk is an essential element in any well-developed information security plan. With the rise of new types of insider threats, organizations need to gain a proactive strategy when it comes to safeguarding sensitive information. With insider threat solutions like access control, user activity monitoring, and data loss prevention in place, organizations can minimize their risk exposure. It is also about employee training and a security culture that helps identify insider threats early on and respond to them in an appropriate manner.
In an era when data is one of the most treasured commodities a company has to offer, protecting it from insider threats is not only a security matter, it’s also a matter of trust. With the proper tools, policies, and approach, companies can secure that most sensitive information against those with the highest access to it.
ABOUT THE AUTHOR
IPwithease is aimed at sharing knowledge across varied domains like Network, Security, Virtualization, Software, Wireless, etc.