Table of Contents
Losing data by businesses is bad, it erodes the customer confidence and impacts the brand value could result in financial losses, penalties, lawsuits, regulatory non compliances and exposure of organization intellectual property. All this raises the question of how to protect data from prying eyes and secure it in such a manner that only people authorized to access it only have means to access them? How to prevent data leakage also referred as data exfiltration for intentional or unintentional misuse.
Today we look more in detail about Data loss prevention technology and its related solutions. What are the different types of Data loss prevention techniques, their types, tips to prevent data exfiltration or data loss.
Data Loss Prevention (DLP)
Before we deep dive into what data loss prevention techniques or solutions, we need to understand why we need such software at all. Many regulations mandate protection and safeguard sensitive personal data especially in case of regulated industries like healthcare, government sectors, financial institutions such as banks are required by law to adopt measures to secure personal data held by them.
Apart from regulatory requirements businesses need to protect their proprietary information such as business structure and its operations, clients and partner details, formulas, patent information, business documents etc. Data loss prevention refers to a set of processes, policies, and tools which are meant to protect organization data, prevent its leakage for misuse – intentional or unintentional.
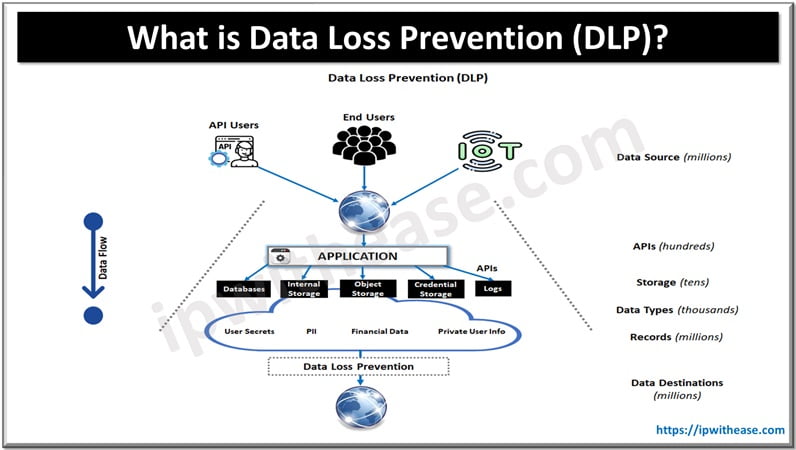
How does Data Loss Prevention work?
There are several ways to DLP security, which are implemented via best practices and tools. Let’s look more in detail on types of data loss prevention techniques.
- Data Identification – with this process an organization identifies sensitive information in their environment, and its location whether it resides in emails, cloud storage applications, collaborative applications or anywhere else within the digital ecosystem.
- Data Leak Identification – This is an automated process for detection and identification of misappropriated data, whether it was exfiltrated or misplaced within an organization’s infrastructure.
- Data in Motion – When data moves from one location to another during its transit, DLP ensures it is not tempered in between.
- Data at Rest – Safe storage of data locally or in cloud when it is not in transit or motion and protected against unauthorized access or use.
- Data in Use – data currently in use within an organization need to be protected from alteration, screen capturing, cut/copy/paste, printing , or moving information.
Data Loss Prevention Best Practices
Employee Awareness and Education
Training employees on what to do and what not to do with the organization data is the first step towards data loss prevention. Employee education and awareness systems should include safe practices to transfer, view, and store data. Training should be sponsored from the executive level and should be repeated at regular intervals for enforcement of good practices.
Data Handling Policies Establishment
Data handling policies need to be defined covering where data can be stored, how data can be transferred, who can view what types of data, what type of data is allowed to be stored and so on. Policies help to drive all data handling guidance.
Data Classification
Data classification taxonomy will help to define more stringent controls around different types of data. Common classifications include – confidential, public, restricted etc.
Sensitive Data Monitoring
Successful data protection entails monitoring sensitive data and all its aspects related to storage, and use including :
- User access
- System access
- Application access
- Types of threats
- Geographical locations
- Access timings
- Data context
DLP Solution to cover Shadow IT
You also need to consider access of data by shadow IT as more and more organizations are moving towards software-as-a-service (SaaS) applications it is becoming hard to accurately assess safety of cloud-based applications. Under the SaaS model provider is responsible for application only however users are responsible for data used by the application. Users may not be well versed to understand protection of data from attacks that may come through a compromised SaaS application.
Different Levels of Access and Authorizations
This practice goes hand in hand with data classification as combining both of them will grant access to data only to those who have authority to access the data. Zero trust data protection can be deployed using DLP software.
Continue Reading:
What Is Privacy Enhancing Technology? And How It Protects Your Data
Top 5 Data Breaches in Cyber Security and Possible Preventative Measures
Watch Related Video
ABOUT THE AUTHOR

You can learn more about her on her linkedin profile – Rashmi Bhardwaj