Table of Contents
In the digital age the cyberattacks are on rise exponentially, with increased use of artificial intelligence and cloud hosting services used by organizations where they need to rely on 3rd party services providers for data security.
There are a variety of cyber attacks used by bad actors to gain unauthorized access to organization systems, steal data, launch ransomware attacks and so on.
Stealing data on the way to its recipient is a popular technique used by bad actors in a silent way to gain access to sensitive information such as credit card numbers, account information, credentials etc.
MITM attack is one of the most widely used techniques on the Internet to steal data earlier done by bad actors and with the advent of AI it is also being carried out using AI Bots, so technically there is no human involved in the attack but a bot.
In this article we will learn more in detail about Man-in-the-middle attack technique, how it works, what are the safeguards that can be deployed to prevent it.
Understanding MITM Attack
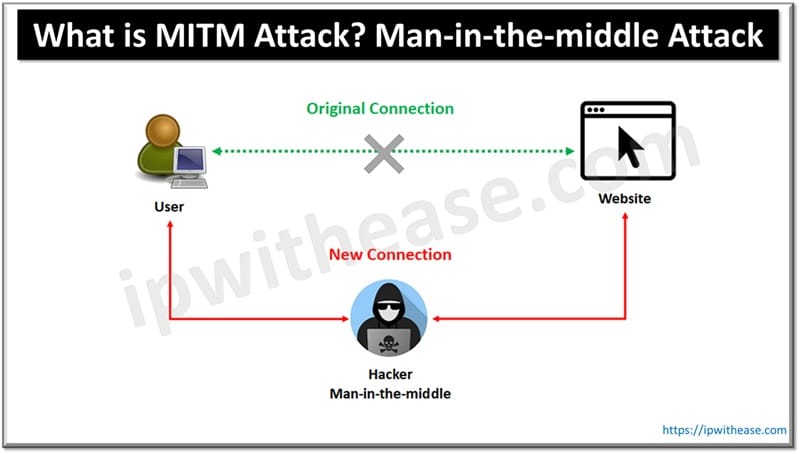
A Man-In-the-middle attack is the most widely used technique world wide to steal data. As per IBM statistics in the year 2024 there were 35% of attacks which were attributed to MITM attacks. Out of which 19% were successful. Attackers place themselves between two communicating parties here and intercept sensitive data by eavesdropping. Using steal credentials and other sensitive data attackers launch other cyber-attacks such as financial accounts hijacking, unauthorized purchases and identity theft etc.
The exchange can also divert and relay messages between sender and receiver thereby taking control of communication. Some organizations are now moving away from the term ‘Man-in-the-middle-attack’ as with the surge of AI it is not necessary to have a human between sender and receiver, it could be an AI bot. These kinds of cyberattacks are named as Machine-in-the-middle, on-path attacks, adversary-in-the-middle (AITM), manipulator-in-the-middle (MiTM).
How Man-in-the-middle Attack works
Man-in-the-middle attack exploits vulnerabilities across networks, systems, web browsers, email accounts, unsafe user behaviour or a security hole in the system or process. Cyber attackers launch MITM attacks using these weaknesses and position themselves between sender and business applications to control communication and intercept the data on the channel during transit.
Phishing attacks are a widely used and popular channel for MITM attacks. When a user clicks a malicious mail or links it launches a MITM attack in the browser. The system gets infected with malware which enables hackers to modify web pages, track user activity and perform malicious transactions.
Another common technique is use of public Wi-Fi hotspots. The routers in public wi-fi systems are less secure and makes it an easy target for hackers to hack the routers and collect user data.
In MITM attacks fake websites are also created to trick users to visit the fake website and collect sensitive data such as login credentials. Stolen credentials are used to login to genuine websites and perform unauthorized transactions.
How to Prevent Man-in-the-middle Attacks?
Let’s look at some security measures that can be taken to prevent man-in-the-middle attacks.
- HTTPS – Users should only visit websites having secure connections represented with HTTPS and a padlock icon on the address bar of the web page. Web pages having unsecured HTTP connections where data flows in plain text should be avoided. SSL and TLS protocols should be implemented to protect against malicious web traffic and spoofing attacks.
- Endpoint Security – Endpoints such as computers, laptops, phones and servers need to be secured with latest patches and anti-malware software to prevent MITM attacks.
- Virtual Private Networks – A VPN provides a secure and encrypted channel for communication over the public Internet and a good practice to prevent MITM attacks. In the event if hackers could breach the communication channel, they still will not be able to read sensitive details such as credentials etc. due to encryption.
- Multi-factor Authentication (MFA) – To further secure login credentials deploying MFA while login to devices or network provides an additional safety net, in the event login credentials are compromised, hacker will not gain access to system as MFA will act as secondary mechanism to check authenticity of the user.
- Encryption – Encryption is a basic requirement for defending against MITM attacks on networks. End to end encryption on all network communication, email accounts, DNS, applications can effectively deter the attack.
- Public Wi-Fi Networks – Users should not use public Wi-Fi networks for doing sensitive transactions such as buying services online etc.
ABOUT THE AUTHOR

You can learn more about her on her linkedin profile – Rashmi Bhardwaj