Table of Contents:
Ever evolving cybersecurity landscape is the demand of modern organizations irrespective of their size, nature of business or industry. With the advent of cloud computing, Artificial intelligence, machine learning etc. Risks of ransomware attacks are on rise and a serious threat for the IT landscape. Impact of ransomware can be devastating as vital devices and data are made inaccessible to organizations until they pay a sum of money to threat actors. Vast majority of organizations are unprepared for such attacks; a recent study by IBM indicates 77% of the organizations do not have a CSIRP (Computer Security Incident Response Plan) applied reliably across their enterprise.
Today we look more in detail about a robust ransomware incident response plan, what steps are crucial in an incident response plan, why a ransomware incident plan is required? etc.
Ransomware Incident Response Plan
Ransomware attack is a criminal intrusion into organizations systems and data to encrypt them and demand a ‘ransom’ or payment. Cybercriminals use ransomware to lock data and systems and demand money in lieu of returning back the control. failure to pay ransom might result in leaking data on dark web or permanently blocking access to files etc., however paying too also does not guarantee release.
We will outline five steps with key pointers and best practice to create an effective ransomware response plan which could be further tailored to address organization specific requirements.
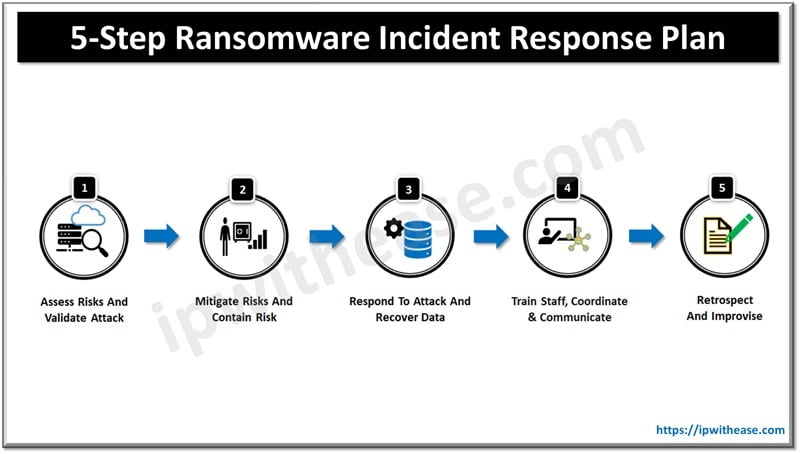
1. Assess Risks & Validate Attack
Organization risk posture assessment is the very first critical step before deriving the response plan. Conducting a thorough risk assessment and threat analysis to identify critical systems and data which could be potential targets. Threat analysis also needs to include understanding of types of ransomware attacks and organization appetite to risk.
You need to validate to understand if an attack is actually occurring. There are varieties of malwares – phishing, adware or other malware infections which exhibit symptoms similar to ransomware such as weird file extensions, unusual emails , system slow down etc.
2. Mitigate Risks & Contain Risk
Once organization risks are assessed ; now it is time to start the mitigation actions. This may include implementation of security measures such as firewalls, intrusion detection or prevention (IDS/IPS) systems, anti-virus software etc. also staff need to be trained to identify and respond to ransomware attacks.
If you assess an attack is happening or in progress then immediately initiate steps to contain it by isolation of infected systems, disable network access from affected systems, quarantine infected files, and contact law enforcement agencies.
3. Respond to Attack and Recover Data
A well defined business continuity and disaster recovery plan (BCP/DR) is required to ensure you can quickly respond and handle ransomware attacks effectively. A comprehensive and detailed backup and recovery plan is crucial to defy a ransomware attack apart from taking other measures to eradicate ransomware from systems such as systems and data restoration from backups, removal of ransomware infected files etc.
Restoration of data and systems is priority post attack. If 3-2-1 backup practice is followed then backup should be unaffected from attack so you can restore the ‘last good known version’ be it cloud or on premises.
4. Train Staff, Coordinate & Communicate
Comprehensive, contextual, and regular cyber security training are required to ensure staff is well versed in handling such situations. Sharing files or folders or accessing advice staff to follow ‘least privilege’ principle.
It is important to have clear communication and coordination with all relevant stakeholders during the entire incident response process. This involves working closely with different teams such as IT, security, legal, operations, or any other stakeholders inside or outside the organization.
5. Retrospect & Improvise
Effective ransomware incident plans require coordination between several teams and individuals inside or outside the organization. Everyone is required to be involved in a plan, need to understand their role and responsibilities clearly and a clear chain of command.
Conducting regular training on incident plans to ensure it is up to date and effective. Identify gaps and weaknesses in plan and address them before actual attack happens.
Once an incident is handled it is time to step back and analyze what has happened and understand the mistakes to improve the defenses against any future attacks. This post-incident analysis of how an attack happened, security posture weaknesses help in improving the incident response plan and lastly monitoring of new threats and risks is the most important step in an effective plan.
Continue Reading:
Whaling Phishing Attack – Cyber Security
Top 5 Data Breaches in Cyber Security and Possible Preventative Measures
ABOUT THE AUTHOR

You can learn more about her on her linkedin profile – Rashmi Bhardwaj