In large networks especially Data Centers, the ACLs can be too big – up to hundreds of lines and difficult to configure and manage. 
Object group-based ACLs provide the solution here – these are smaller, readable, and easier to configure and manage.
Not only are the static ACL, but also dynamic ACL deployments for large user environments are befitted.
Related – ACL on Router vs Firewall
The Object Groups feature allows us to classify users, devices, or protocols into groups and apply those groups to access control lists (ACLs).
This lets us create access control policies for groups and use object groups instead of IP addresses, protocols or even port numbers which are used in conventional ACLs.
The approach is to use a single ACE to allow an entire group of users to access a group of user or server groups.
Object Groups supports two types of object groups for grouping ACL parameters –
- Network object groups
- Service object groups
A Network object group is a group of any of the following objects:
- Any IP address
- Host IP addresses
- Hostnames
- Other network object groups
- Ranges of IP addresses
- Subnets
Related – Cisco ASA 5505 Factory Reset
A service object group is a group of any of the following objects:
- Source and destination protocol ports (Like telnet, SNMP etc)
- ICMP types (such as echo, echo-reply etc)
- Top-level protocols (such as TCP, UDP etc)
- Other service object groups
A Scenario will help understand the concept of Object groups and how with simple commands, we can reduce creating big ACL lines into just a few ones –
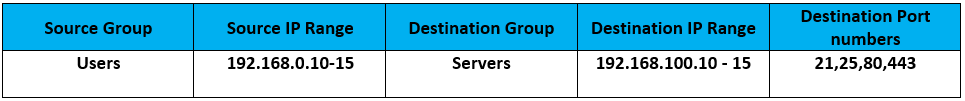
The requirement is to allow client machines to access some specific servers for services like Telnet, HTTP and SMTP.
Below table enlists the requirements –
Related – Cisco ASA Interview Questions
Configuration of Object Groups –
description USER Addresses
network-object host 192.168.0.10
network-object host 192.168.0.11
network-object host 192.168.0.12
network-object host 192.168.0.13
network-object host 192.168.0.14
network-object host 192.168.0.15
!
object-group network SERVERS
description SERVER addresses
network-object host 192.168.100.10
network-object host 192.168.100.11
network-object host 192.168.100.12
network-object host 192.168.100.13
network-object host 192.168.100.14
network-object host 192.168.100.15
!object-group service USER-SERVER-PORTS
service-object icmp echo
service-object icmp echo-reply
service-object tcp eq 21
service-object tcp eq 25
service-object tcp eq 80
service-object tcp eq 443
To reiterate , the 2 Group types used here are –
- Network – To specify IP addresses and subnets
- Service – To specify port numbers and protocols
Now we put it together in an ACL as below –
Lets view the outcome through “show access-list” output
access-list USER-2-SERVERS line 1 extended permit object-group USER-SERVER-PORTS object-group USERS object-group SERVERS 0xc17e46b0
access-list USER-2-SERVERS line 1 extended permit icmp host 192.168.0.10 host 192.168.100.10 echo (hitcnt=0) 0xa95de6ef
access-list USER-2-SERVERS line 1 extended permit icmp host 192.168.0.11 host 192.168.100.10 echo (hitcnt=0) 0x93544346
……
So in all total 216 line will be created which will encompass all the USER and SERVER communication ACLs along with port numbers and protocols.
Hence, to summarise a single line (via Object Groups) has done the work what 216 lines were originally supposed to perform via ACLs.
ABOUT THE AUTHOR

You can learn more about her on her linkedin profile – Rashmi Bhardwaj