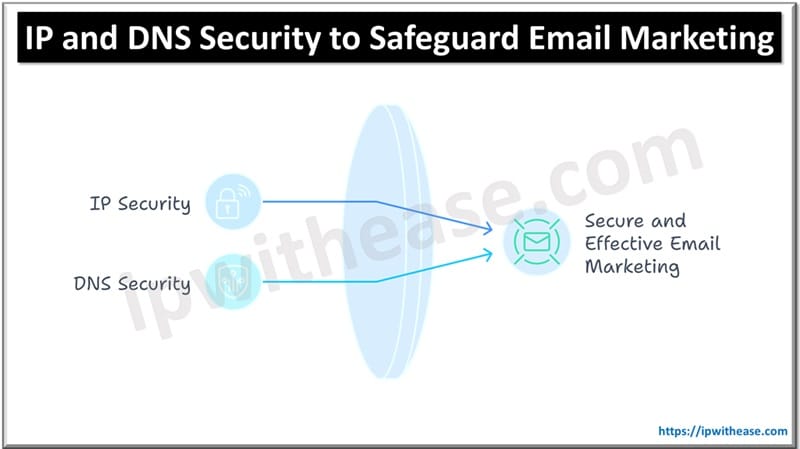
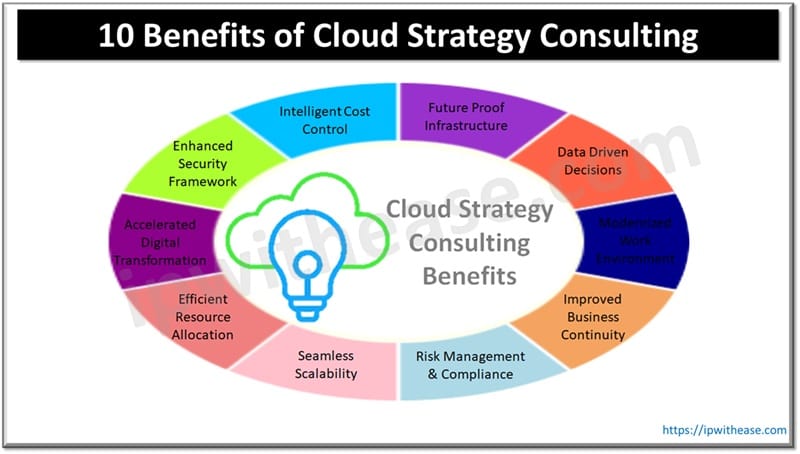
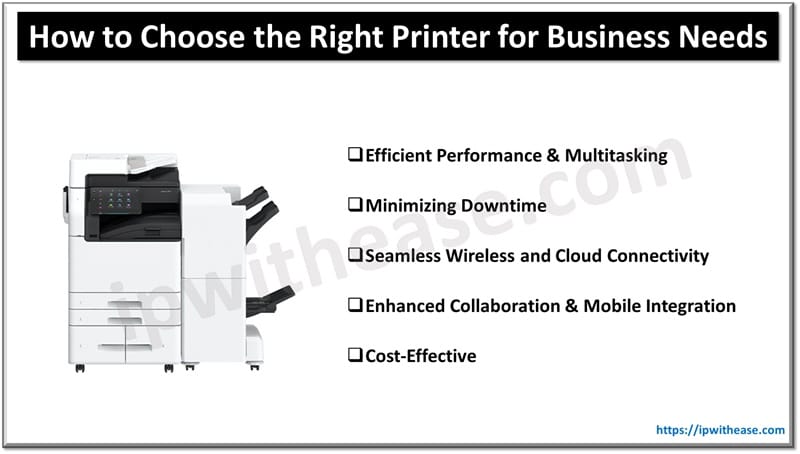
Table of Contents
Operational Technology environments play an important role in the overall industrial operations. These include managing critical infrastructures such as manufacturing plants, energy grids, and transportation systems. Increasingly common cyber threats targeting their networks require effective security measures. This blog post discusses the definition, advantages, and strategies of implementation of continuous monitoring in OT security.

The Core of Continuous Monitoring in OT Security
Real-Time Situational Awareness
The round-the-clock monitoring provides real-time insights and unparalleled visibility into the activities of OT assets and network provisions. By 2024 the cyber security market is projected to reach an impressive figure of US$185.70bn worldwide. This situational awareness will be a part of spotting abnormalities and possible threats, with which a timely resolution to incidents can be initiated before they escalate into significant issues. Vigilance fosters a better understanding of an organization’s operational environment and a more efficient response to vulnerabilities.
Proactive Threat Detection
Using advanced techniques such as machine learning and anomaly detection and continuous monitoring systems identify unusual patterns that reflect probable cyber threats or operational issues. Such an approach is key to maintaining proactive robust OT security solutions, and these sophisticated techniques allow the organization to stay ahead of possible threats by analyzing patterns in data and identifying deviations from the typical, hence preventing incidents before they occur.
Key Benefits of Continuous Monitoring
Reduced Downtime
Regular monitoring almost eliminates downtime due to cyberattacks or failures in operations. By early detection of any threats or anomalies, industrial processes could remain continuous and therefore efficient to minimize losses, both finances and reputations. That way, organizations can continue working and avert the expensive consequences of unplanned shutdowns.
Enhanced Incident Response
Deep insight into the activities in the network allows continuous monitoring tools to act fairly quickly in identifying and addressing incidents among security teams. Rapid responses are essential for reducing the impact of security breaches and for ensuring industrial networks remain secure.
Such tools provide real-time data or alerts, enabling immediate actions to contain and remediate the impacts of threats before they escalate.
Improved Regulatory Compliance
Continuous monitoring helps organizations meet regulatory requirements by providing necessary visibility and reporting capabilities. This ensures compliance with industry standards and regulations, which is crucial for maintaining cybersecurity for industrial networks. By offering comprehensive documentation and audit trails, continuous monitoring platforms assist organizations in demonstrating their adherence to regulatory mandates.
Critical Components of a Continuous Monitoring Platform
Comprehensive asset management, which involves identifying and inventorying all OT assets, is required for continuous monitoring in industrial networks to understand and protect the operational environment.
Keeping a current list of all devices and systems enables organizations to maintain an accurate representation of all assets and security over all assets. The detailed inventory can enable the identification of possible entry points for cyber threats and allow targeted security measures to be implemented.
Moreover, an advanced continuous monitoring system would require sophisticated functions for mapping vulnerabilities that recognize and classify risk-based vulnerabilities. This helps organizations target their resources toward the most critical areas, improving overall safety.
Vulnerability Mapping is about continuously scanning the network for weaknesses, assessing the severity, and understanding the impact on an organization’s operations. By systematic identification and assessment of vulnerability, organizations may always address key risks proactively through actions like patching software, firmware updates, and additional security measures.
It should be complemented by a framework for security incident response and threat intelligence-sharing initiatives, with continuous monitoring playing a key role.
Threat Detection and Anomaly Detection
Platforms should be provided with signature-based and behavior-monitored detection techniques to cover a complete list of threats from the known unknown malware rubric to subtle anomalies.
Such a multipronged approach is essential for industrial network security. By these means, of combination detection, an organization will be able to ensure thorough coverage as well as effective threat detection.
Implementation Strategies for Continuous Monitoring
Integration with Existing Systems
Continuous monitoring solutions should be integrated with existing OT and IT systems to provide a unified view of the operational environment. This integration facilitates better risk management and coordination between different security teams. By consolidating data from various sources, organizations can achieve a holistic view of their security posture and improve their ability to detect and respond to threats.
Regular Updates and Maintenance
To remain effective, continuous monitoring systems must be updated regularly to keep up with evolving threats and vulnerabilities. This involves updating threat intelligence feeds and ensuring that the monitoring tools are configured to detect new types of attacks. By continuously refining and enhancing their monitoring capabilities, organizations can stay ahead of emerging threats and maintain robust security.
Addressing Common Challenges in OT Security
Handling Legacy Systems
Most OT environments have legacy systems in terms of security capabilities. Continuous monitoring platforms have to be adapted to fit into such systems without disturbing operations. This is crucial as part of the OT security solutions to complement them. By employing monitoring solutions that integrate with older systems, organizations can strengthen their security posture without disrupting operational efficiency.
Balancing Safety and Security
The most important things in operational technology environments are safety and availability. Continuous monitoring solutions should ensure that the security measures do not interfere with safe and reliable operation of industrial processes. This balance is critical in addressing industrial cyber threats. Organizations can thus ensure the protection of their operations by ensuring that safety is matched by security so that there is no doubt of continuous production.
Conclusion
Continuous monitoring is a critical component in reducing OT security risks in industrial networks. By offering real-time situational awareness, proactive threat detection, and comprehensive asset management, continuous monitoring ensures the safety, availability, and regulatory compliance of industrial operations. As cyber threats continue to evolve, adopting robust continuous monitoring solutions will be essential for maintaining the security and integrity of OT environments.
FAQs
1. How do we ensure the security of OT equipment against cyber threats?
To safeguard OT equipment from cyber threats, organizations should implement the following practices: Network Mapping and Connectivity Analysis, Detection of Suspicious Activities and Malware, Zero-Trust Framework, Remote Access Tools, and Identity and Access Management (IAM).
2. Why is continuous monitoring important in cybersecurity?
Continuous monitoring is important in cyber security because it works as your organization’s early warning system against cyber threats. With the increasing reliance on technology for day-to-day operations, the need for robust information security measures has become more critical than ever.
3. What is the purpose of continuous monitoring in DevOps?
Continuous Monitoring in DevOps helps organizations track the operational performance of the app. It supports monitoring the user’s behavior at the time of new application updates. It helps teams understand the impact of recent updates, and real-time data on user interactions, and the overall user experience.
ABOUT THE AUTHOR
IPwithease is aimed at sharing knowledge across varied domains like Network, Security, Virtualization, Software, Wireless, etc.