Table of Contents
Retrieval-Augmented Generation (RAG) combines retrieval and generation technologies, offering advancements in AI. This article explores RAG’s mechanics, benefits, challenges, and solutions, focusing on privacy.
Understanding Retrieval Augmented Generation
Definition of RAG
RAG combines information retrieval and natural language generation to produce accurate and contextually relevant outputs.
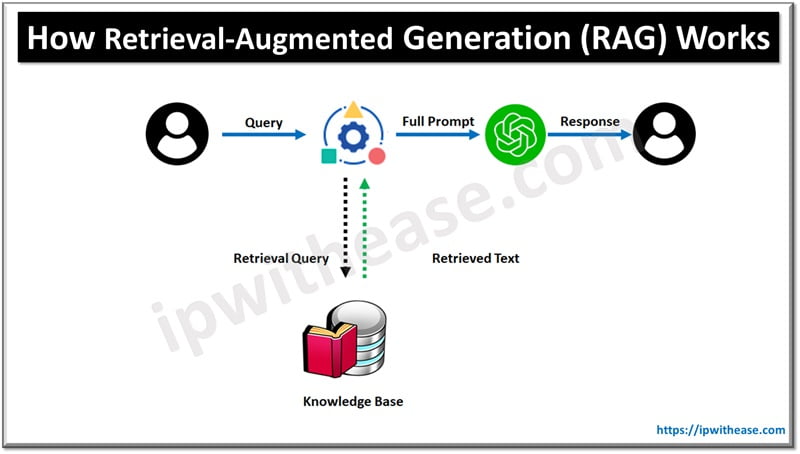
How RAG Works
Retrieval Component
The retrieval system fetches relevant data from large datasets, enabling the model to access up-to-date and precise information.
Generation Component
The generation system creates coherent and contextually appropriate responses based on the retrieved data.
Step-by-Step Workflow
| Step | Description |
| 1. User Query | The user submits a question or request to a RAG application. |
| 2. Similarity Search | The application performs a similarity search, usually against a vector database, to identify relevant document chunks. |
| 3. Data Retrieval | The application retrieves the necessary data from various sources such as file systems, APIs, or databases. |
| 4. Prompt Augmentation | Relevant chunks are injected into a prompt template to provide context for the language model. |
| 5. Response Generation | The language model generates a response using the augmented prompt, producing accurate and contextually relevant outputs. |
What Does RAG Solve?
Improved Accuracy
RAG enhances response accuracy by leveraging relevant data, minimizing outdated or irrelevant information. According to database experts this ensures that responses are based on the most current and reliable data available, leading to more precise and reliable outputs.
Contextual Relevance
RAG provides responses that are more contextually appropriate and informative, addressing issues with stale training data. By incorporating real-time information retrieval, RAG can adapt to the nuances of the user’s query, delivering answers that are not only accurate but also highly relevant to the context.
Reduced Hallucinations
Language models can produce plausible yet incorrect answers. RAG minimizes these hallucinations by grounding responses in retrieved data. This grounding helps ensure that the information provided by the model is backed by actual data, reducing the risk of misleading or false information.
Addressing Privacy Concerns with RAG
Data Anonymization
Techniques to anonymize data help protect user identities and sensitive information. By removing or obfuscating Personally Identifiable Information (PII) and other sensitive data, RAG systems can minimize the risk of privacy breaches while still providing useful and relevant responses.
Secure Data Storage
Implementing robust security measures for data storage ensures the safety of retrieved information. Encryption, access controls, and regular security audits are critical components of a secure data storage strategy, helping to protect against unauthorized access and data breaches.
Zero Retention LLM
Using zero-retention language models prevents the storage of chat histories, enhancing privacy. This approach ensures that once a conversation is complete, no record of the user’s queries or responses is retained, significantly reducing the risk of data leakage or misuse.
Best Practices for Implementing RAG
Transparency
Clearly informing users about how their data is used fosters trust and transparency. Providing detailed information about data collection, usage, and retention policies helps users understand the steps taken to protect their privacy and how their data is being utilized.
Regular Audits
Conducting regular audits helps identify and mitigate privacy risks, ensuring compliance with privacy standards. These audits should assess the effectiveness of data protection measures, identify potential vulnerabilities, and ensure that privacy practices align with the latest regulations and best practices.
User Control
Allowing users control over their data and its usage enhances trust and compliance with privacy laws. Providing options for users to view, manage, and delete their data gives them a sense of ownership and control over their personal information, which is crucial for building trust and ensuring compliance with privacy regulations.
Future Directions for RAG and Privacy
Enhanced Privacy Techniques
Exploring new methods to protect privacy within RAG systems is essential for future advancements. Techniques such as differential privacy, homomorphic encryption, and federated learning offer promising avenues for enhancing data protection while still enabling the benefits of RAG.
Regulatory Compliance
Adapting to evolving privacy regulations and standards ensures that RAG systems remain compliant and trustworthy. Staying abreast of changes in privacy laws and standards, and incorporating these into RAG systems, is critical for maintaining legal compliance and user trust.
Final Words
RAG offers substantial benefits but also presents privacy challenges. By understanding these risks and implementing best practices, we can leverage RAG’s capabilities while protecting user privacy.
Key Takeaways
- RAG combines retrieval and generation technologies for accurate, contextually relevant outputs.
- Proper data anonymization, secure storage, and user consent are essential to addressing privacy concerns.
- Regular audits and user control over data enhance trust and compliance with privacy standards.
- Future advancements in privacy techniques and regulatory compliance will shape the development of RAG systems.
By balancing the benefits of RAG with robust privacy measures, we can harness its full potential while safeguarding user information.
ABOUT THE AUTHOR
IPwithease is aimed at sharing knowledge across varied domains like Network, Security, Virtualization, Software, Wireless, etc.