Table of Contents
RDP or Remote Desktop Protocol allows direct access to a remote computer’s desktop interface, transmitting screen and input data. On the other hand, VPN creates a secure tunnel between your device and the network, allowing safe access to network resources as if you were physically present. Choosing between RDP and VPN for remote access first requires an understanding of differences between the two and then assessing your requirements.
In this article, we will compare RDP and VPN for remote access on the basis of security, performance, and accessibility.
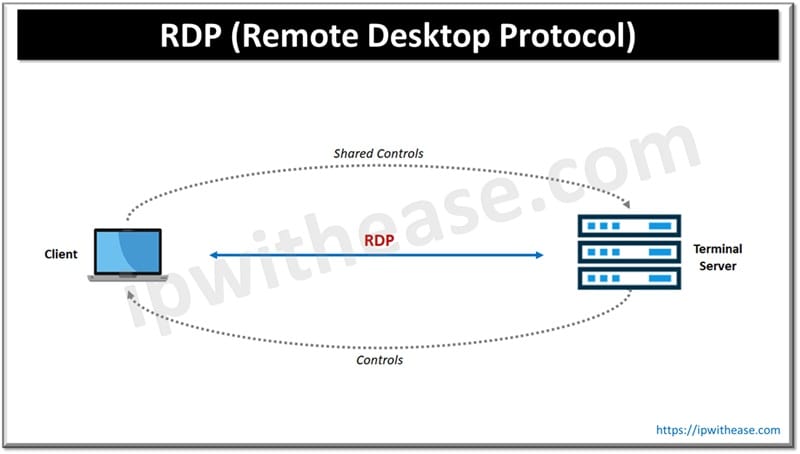
What is RDP (Remote Desktop Protocol)
RDP is a proprietary protocol developed by Microsoft. It enables users to connect to and control another computer over a network. It transmits the remote computer’s screen to the user’s device and sends keyboard and mouse inputs back to the host. It operates over TCP port 3389 and supports encryption, multi-monitor setups, and clipboard redirection.
Benefits & Drawbacks of RDP
| Benefits of RDP | Drawbacks of RDP |
|---|---|
| • Quick, secure access to your remote infrastructure • Full remote desktop control • Optimized for environments with low bandwidth • A graphical user interface for tasks such as system management • Reduction in hardware and software expenses • Elimination of local resources by clearing the page • Enhanced security features (refer to NLA, encryption, MFA) • Support for cross-platform RDP clients • Simplifies the administration of remote systems | • Security Vulnerabilities (if not secured correctly) • Requires complex configuration • Disconnect if the remote machine reboots • No multi-session on standard Windows platforms • Not supported in some Windows home editions • Reliant on a steady internet connection • Prone to connection errors |
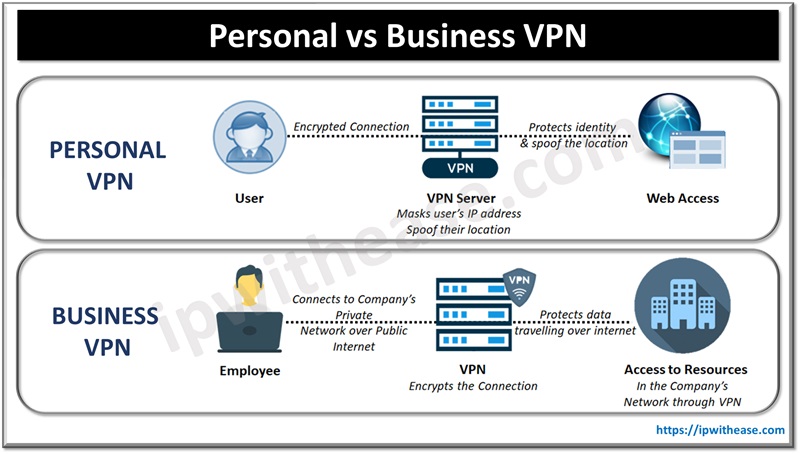
What is VPN (Virtual Private Network)
VPN allows users to securely connect to a private network (like a company’s internal network) over the internet. It creates an encrypted tunnel between the user’s device and the organization’s network, ensuring that data is protected from eavesdropping or tampering. Once connected, users can access files, applications, and internal systems as if they were physically present in the office.

Benefits & Drawbacks of VPN
| Benefits of VPN | Drawbacks of VPN |
|---|---|
| • Simple and quick to establish a secure connection • Guarantees robust online privacy • Efficient with minimal bandwidth usage • Enables access to resources from any device • Protects public Wi-Fi with strong encryption measures • Conceals your IP address to reach restricted websites using this swift and modern web proxy • Masks IP and circumvents geo-restrictions • Encrypts and safeguards sensitive information • Maintains data integrity throughout transmission • Provides centralized management of user access | • May necessitate additional hardware or software • Complicated setup for larger organizations • Potential lag and reduced connection speed • Relies on the quality of the VPN server • Security vulnerabilities if the system is breached • Observable by Internet Service Providers • Risk of detection and blocking of VPN traffic • Challenges in the troubleshooting process • Not supported by certain services • Latency problems for applications requiring real-time performance |
Comparison: RDP vs VPN
| Feature | RDP (Remote Desktop Protocol) | VPN (Virtual Private Network) |
|---|---|---|
| Purpose | Access a remote computer’s desktop and resources | Secure access to a private network over the internet |
| How it works | Streams the remote desktop interface to the local device | Creates an encrypted tunnel between device and network |
| Access Level | Full control of a remote system (GUI-based) | Network-level access, like being physically connected |
| Usage | Used for remote tech support, admin tasks, or remote workstations | Used for secure browsing, accessing internal resources remotely |
| Security | Can be vulnerable if not secured (e.g., via VPN or encryption) | Highly secure with encryption protocols like IPSec, SSL/TLS |
| Requires Remote PC On? | Yes, the remote PC must be on and RDP-enabled | No, connects to the network, not necessarily to a specific PC |
| Security | •Can be vulnerable to brute force attacks if exposed directly •Best secured when used over VPN or with multi-factor authentication | •Uses strong encryption (IPSec, SSL/TLS) •Secure tunnel protects all traffic- Better for broad secure access |
| Performance | •Requires more bandwidth (renders GUI remotely) •Can lag on slow networks •Affected by remote device performance | •Generally faster for file access and network apps •Lower overhead without GUI rendering •Can be optimized with split tunneling |
| Accessibility | •Access to a specific remote desktop only •Needs the remote device powered on and reachable | •Access to entire private network •Works on multiple devices and platforms •Does not require a specific machine to be online |
Download the comparison table: RDP vs VPN
RDP Use Cases
- Remote IT Support and Troubleshooting
- Remote Server Administration
- Running Business Applications Remotely
- Software Development and Remote Testing
- Remote Learning and Virtual Classrooms
- Secure Access to Medical Systems
- Remote Maintenance of Physical Infrastructure
- Working while traveling or on Business Tours
- Running trading bots 24/7
VPN Use Cases
- Employee Data Privacy When Working from Home
- Securing Public Wi-Fi Networks
- Defeating Geo-restrictions and Censorship
- Bypassing Geo-Restrictions and Censorship
- Private and Anonymous Web Browsing
- Private remote access to your company’s central server
- Accessing Files Through a Private Network
- Access the Internet as if you were in your home country with the best VPN for accessing local content overseas.
Final Words
When to use RDP?
When you need full control of a remote computer’s desktop, such as for IT support, administration, or accessing a work PC with all its applications and settings.
When to use VPN?
When you need secure access to a private network’s resources (like files, databases, or intranet) without necessarily controlling a remote desktop.
VPN can also be combined with RDP, for higher security, allowing remote desktop access through an encrypted tunnel.
ABOUT THE AUTHOR

You can learn more about her on her linkedin profile – Rashmi Bhardwaj