In the previous posts, we discussed simple DMVPN phase 1 and DMVPN phase 2 where no mechanism for data protection is used. Usually, DMVPN tunnels are built over the internet and sending our data traffic over the internet without encryption won’t be a good idea.
Hence in this post we will discuss DMVPN over IPSec and see how we can add IPsec encryption to the data, thus securing our data while it traverses the internet.
Related- IPSEC vs SSL
DMVPN over IPSec
We will still use the same topology as the one we used in our earlier posts as below:

The configuration for simple DMVPN Phase is already up and running in this lab. For configuration details to bring up the simple DMVPN tunnels please refer to post for DMVPN phase 1. We were running EIGRP as the dynamic protocol for the route advertisement.
Related- GETVPN vs DMVPN
As per the logs below we see our tunnels are up:
R2#sh dmvpn | be peer
NHS Status: E –> Expecting Replies, R –> Responding, W –> Waiting
UpDn Time –> Up or Down Time for a Tunnel
==========================================================================
Interface: Tunnel0, IPv4 NHRP Details
Type:Spoke, NHRP Peers:1,
# Ent Peer NBMA Addr Peer Tunnel Add State UpDn Tm Attrb
—– ————— ————— —– ——– —–
1 9.9.0.1 192.168.10.1 UP 00:00:46 S
R3#sh dmvpn | be peer
NHS Status: E –> Expecting Replies, R –> Responding, W –> Waiting
UpDn Time –> Up or Down Time for a Tunnel
==========================================================================
Interface: Tunnel0, IPv4 NHRP Details
Type:Spoke, NHRP Peers:1,
# Ent Peer NBMA Addr Peer Tunnel Add State UpDn Tm Attrb
—– ————— ————— —– ——– —–
1 9.9.0.1 192.168.10.1 UP 00:00:56 S
R2#ping 3.3.3.3
Sending 5, 100-byte ICMP Echos to 3.3.3.3, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 100/123/156 ms
Now we add the following configuration to enable the IPsec encryption over the tunnels on each router:
encr 3des
hash md5
authentication pre-share
group 2
lifetime 86400
!
crypto isakmp key cisco address 0.0.0.0 0.0.0.0
!
crypto ipsec transform-set abc esp-3des esp-md5-hmac
!
crypto ipsec profile gre_protection
set security-association lifetime seconds 86400
set transform-set abc
!
interface Tunnel 0
tunnel protection ipsec profile gre_protection
After you configure the above on each router we see IPsec tunnels up and running:
R2#sh crypto isakmp sa
dst src state conn-id status
9.9.0.1 9.9.0.2 QM_IDLE 1001 ACTIVE
9.9.0.2 9.9.0.1 QM_IDLE 1002 ACTIVE
IPv6 Crypto ISAKMP SA
R2#sh crypto ipsec sa
Crypto map tag: Tunnel0-head-0, local addr 9.9.0.2
protected vrf: (none)
local ident (addr/mask/prot/port): (9.9.0.2/255.255.255.255/47/0)
remote ident (addr/mask/prot/port): (9.9.0.1/255.255.255.255/47/0)
current_peer 9.9.0.1 port 500
PERMIT, flags={origin_is_acl,}
#pkts encaps: 152, #pkts encrypt: 152, #pkts digest: 152
#pkts decaps: 153, #pkts decrypt: 153, #pkts verify: 153
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts compr. failed: 0
#pkts not decompressed: 0, #pkts decompress failed: 0
#send errors 0, #recv errors 0
local crypto endpt.: 9.9.0.2, remote crypto endpt.: 9.9.0.1
path mtu 1500, ip mtu 1500, ip mtu idb FastEthernet0/0
current outbound spi: 0x58B95824(1488541732)
PFS (Y/N): N, DH group: none
Similarly on R3 we see the crypto tunnels:
R3#sh crypto isakmp sa
dst src state conn-id status
9.9.0.1 9.9.0.3 QM_IDLE 1001 ACTIVE
9.9.0.3 9.9.0.1 QM_IDLE 1002 ACTIVE
IPv6 Crypto ISAKMP SA
R3#sh crypto ipsec sa
Crypto map tag: Tunnel0-head-0, local addr 9.9.0.3
protected vrf: (none)
local ident (addr/mask/prot/port): (9.9.0.3/255.255.255.255/47/0)
remote ident (addr/mask/prot/port): (9.9.0.1/255.255.255.255/47/0)
current_peer 9.9.0.1 port 500
PERMIT, flags={origin_is_acl,}
#pkts encaps: 160, #pkts encrypt: 160, #pkts digest: 160
#pkts decaps: 160, #pkts decrypt: 160, #pkts verify: 160
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts compr. failed: 0
#pkts not decompressed: 0, #pkts decompress failed: 0
#send errors 0, #recv errors 0
local crypto endpt.: 9.9.0.3, remote crypto endpt.: 9.9.0.1
path mtu 1500, ip mtu 1500, ip mtu idb FastEthernet0/0
current outbound spi: 0x43B7E0B9(1136124089)
PFS (Y/N): N, DH group: none
inbound esp sas:
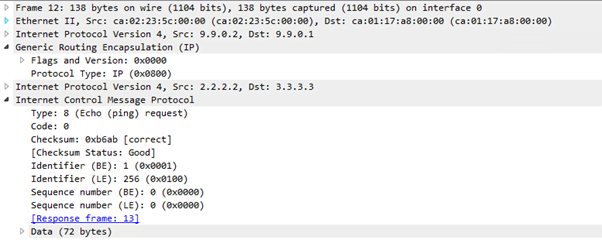
Now the traffic flows between R2 and R3 with IPsec encryption as seen in packet capture below:
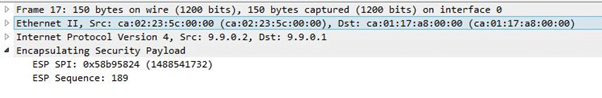
Traffic capture without encapsulation:
Related- DMVPN vs MPLS
ABOUT THE AUTHOR

You can learn more about her on her linkedin profile – Rashmi Bhardwaj