Table of Contents
Salesforce is a powerful cloud-based customer relationship management (CRM) system that allows you to manage your customers, leads, accounts, and more. It’s also a great security risk if not configured correctly. In this post, we’ll walk through some of the best practices for ensuring that Salesforce is secure and safeguarding your data from unauthorized access or breach.
Salesforce security is the protection of data from being accessed by unauthorized parties. Securing your Salesforce account is important because it contains sensitive information about your business, including customer and employee data. Without proper security, your sensitive customer information could be compromised and fall into the wrong hands. Servicenow cyber security services can help you to protect your data by ensuring that all of your Salesforce security settings are configured correctly and that they have appropriate permissions.
Whether you’re implementing new Salesforce functionality, upgrading to a new version of the software, or performing an upgrade on your existing instance, Servicenow’s cyber security services will ensure that your data remains secure throughout the process.
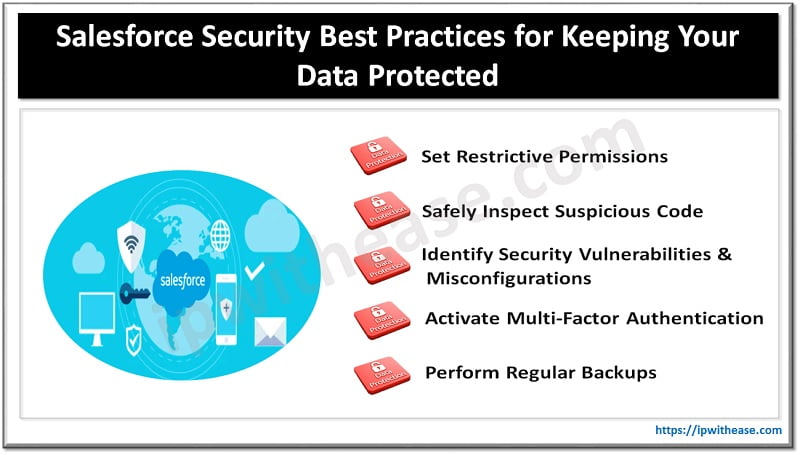
1. Set Restrictive Permissions
The Salesforce permission model is robust, with the ability to set permissions at the object level, field level, user level, and role level. These permissions can be inherited down to lower levels of the hierarchy. This provides you with a wide range of options for controlling access to your data in Salesforce.
2. Activate Multi-Factor Authentication
Multi-factor authentication is one of the most effective ways to protect your data. It requires someone who wants to log in to a Salesforce account to provide more than just a username and password. They also need access to the second piece of information that only belongs to them. This means no one else can get into your system without it.
When you activate MFA, you’ll be asked for an additional form of identification after entering your login credentials. There are many options available: an SMS text message with a code sent to your phone; an app like Authy or Google Authenticator; or even something as simple as an automated call from Zendesk Support asking if it’s really you trying to sign in right now!
Once activated, MFA makes it much harder for hackers who have stolen user credentials and want access beyond their initial targets (e.g., email addresses associated with specific individuals). The extra step required by multi-factor authentication stops these types of attacks dead in their tracks.
3. Identify Security Vulnerabilities and Misconfigurations
Once you have identified any security vulnerabilities, it’s important to understand how to identify misconfigurations. A misconfiguration is an error in the Salesforce platform that could open up your data and systems to unauthorized access or manipulation.
4. Safely Inspect Suspicious Code
The best way to mitigate these risks is to have a policy in place for dealing with suspicious code and then follow that policy. The important step is to use an automated tool that can inspect the code for you. These tools are typically free or available at a low cost and can help you find malicious code in your organization’s Salesforce. In addition, if you want to make sure everything looks OK, manually review the files!
5. Perform Regular Backups
Backups are a necessary part of data security. You should be performing regular backups at least once per week. Many organizations perform a full backup each night, as well as backing up the Salesforce org to an external location every week. If you have been using Salesforce for more than five years, it is likely that your org contains a lot of customizations and metadata that have been hard to maintain over time.
In fact, some companies will spend thousands of dollars per month on maintaining their customizations in order to keep them working properly with new changes in the platform or third-party applications they use with Salesforce (such as Service Cloud). Utilizing Salesforce ETL can facilitate structured data extraction and transformation, ensuring that critical data is backed up and seamlessly integrated into external storage or analytics systems.
If this sounds like something that might happen at your organization soon, it is important that you regularly backup all critical data so that if there ever comes a time when these changes become too complicated or expensive to maintain within Salesforce itself, you still have access to them elsewhere!
Final Thoughts
The Salesforce security best practices that we’ve outlined are just some of the many ways you can make sure that your data is safe. There are other measures you can take as well, such as keeping up with IT certifications and using data encryption software to protect your information.
For more information on how to protect yourself against threats like ransomware attacks and phishing scams (which involve email messages designed to trick users into downloading malicious attachments), check out our blog post on how to prevent identity theft by protecting yourself from these types of threats!
Continue Reading:
How To Stop Ransomware Attacks and Keep Your Data Safe
Protecting Against Spear Phishing
ABOUT THE AUTHOR
IPwithease is aimed at sharing knowledge across varied domains like Network, Security, Virtualization, Software, Wireless, etc.