Table of Contents
Introduction to SD-WAN Security
SD-WAN security is based largely on the use of IP security (IPsec), VPN tunnels, next-generation firewalls (NGFWs), and the network segmentation of application traffic.
Network Segmentation
As new and improvised attacks on assets are being developed globally, security continues to be a growing concern for most network deployments. In order to mitigate such attacks, more and more network administrators are looking at implementing network segmentation. Network segmentation is nothing new, as networks have been achieving network segmentation for years with solutions such as VLANs and VRFs. Network segmentation allows the network to isolate different lines of business or users from each other, unless specific policy allows communication between them. Here are a few common network segmentation use cases:
- To segment regular users from guest users.
- To allow extranet partners to access selective parts of the network.
- To separate PCI and/or HIPAA networks due to regulatory requirements.
By segmenting the control and data planes, we can build disparate topologies per network segment. With the Cisco SD-WAN solution, network segmentation is accomplished via VPNs. Fundamentally, this is the same thing as a VRF, using legacy terminology. There are three different types of VPNs in the Cisco SD-WAN solution:
- Service VPN: These VPNs are where user traffic lives. These VPNs are defined across the overlay and terminate the LAN side of the routers (service side). You can have multiple service VPNs in the fabric and have multiple topologies for different VPNs. These VPNs have a value from 1 to 511.
- Transport VPN: The transport VPN is where the physical (WAN) underlay transport will terminate. This VPN is usually referred to as VPN 0. VPN 0 is statically assigned as the WAN VPN and cannot be changed.
- Management VPN: This is the out-of-band management interface. It uses a VPN value of 512 that cannot be changed.
Each data packet will carry a VPN ID that identifies the VPN it belongs to on the overlay. Once the VPN is configured on WAN Edges, it will have a label tied to it. As the WAN Edge builds its control plane, it will send this label along with the VPN ID to the vSmart controller. The vSmart will then distribute this VPN-ID mapping information to other WAN Edges in the network. The remote WAN Edges in the network will then uses these labels to send traffic for the appropriate VPNs. Because the control plane and data plane have been separated, the solution allows us to build different topologies per VPN. Common topology types are hub-and-spoke, point-to-point, full mesh, and partial mesh. With no topology defined, all VPNs will be full mesh. Since the TLOC route influences how the data plane is built, we achieve these various topologies by filtering routes and TLOCs.
Data Plane Encryption
In overlay technology, encryption and authentication are achieved with IPsec, and Cisco SD-WAN is no different. Encryption handle with the key exchange.
Authentication: Authentication is the mechanism that ensures the two endpoints communicating with each other are valid and authentic.
- 2048-bit keys with RSA encryption.
- Cisco SD-WAN supports Encapsulation Security Payload (ESP) and Authentication Header (AH). These are used to authenticate the origin of the sender.
Encryption: The Cisco SD-WAN solution utilizes the AES protocol with a 256-bit key length to encrypt data.
Integrity: In this step, the data traffic is inspected to ensure that the traffic traversed the network without being tampered with.
- The Galois Counter Mode (GCM) variant of AES-256 has a built-in hashing mechanism that is used to verify data integrity.
- Anti-Replay Protection is also enabled to protect against duplication attacks.
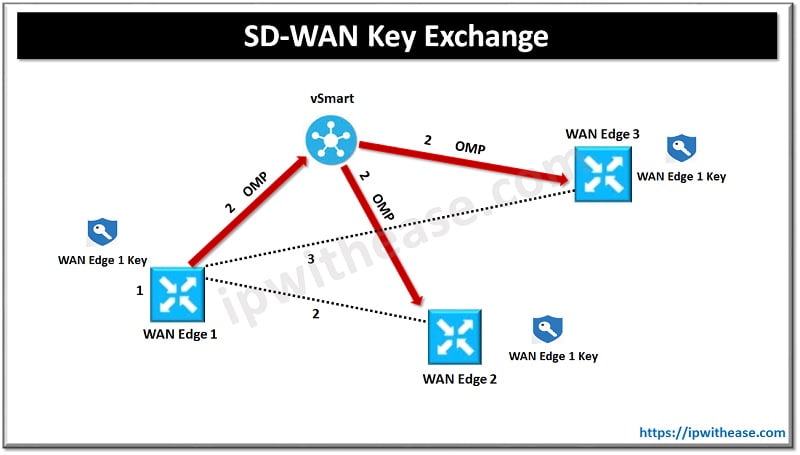
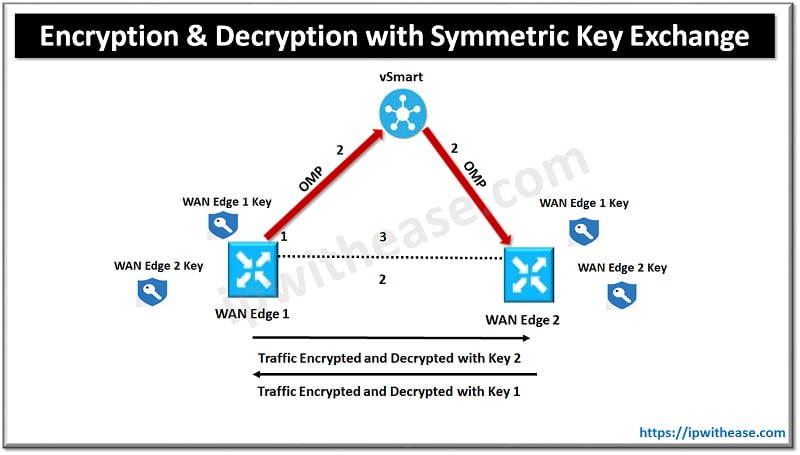
SD-WAN Key Exchange
The Cisco SD-WAN key exchange process consists of the following.
- WAN Edge 1 generates an encryption key.
- WAN Edge 1 advertises the key via an OMP route update. This key is received and reflected by the vSmart controller. (The same process happens on WAN Edge 2 and WAN Edge 3.)
- Now that the WAN Edges have their respective peer keys, IPsec tunnels can be built.
Now that both WAN Edges have the peer’s respective keys, encryption and decryption occurs using the following process:
- WAN Edge 1 and WAN Edge 2 generate encryption keys (WAN Edge 1 key and WAN Edge 2 key).
- Both routers advertise these via OMP.
- If WAN Edge 1 sends traffic to WAN Edge 2, it will use its WAN Edge 2’s key. WAN Edge 2 will use this same key for decryption of that data. For traffic that WAN Edge 2 sends to WAN Edge 1, Key 1 will be used in the same fashion but in reverse.
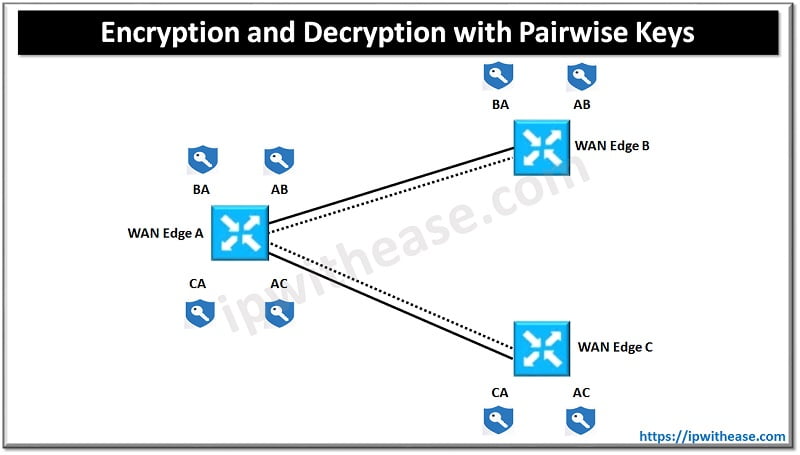
Data Plane Encryption with Pairwise
A recent introduction to the solution’s key exchange model described previously is the use of pairwise encryption keys. Pairwise keys provide some additional security measures in that the same key isn’t used across all devices in the fabric for encryption and decryption. Pairwise functions by generating specific key pairs between two WAN Edges. For example, consider a fabric with three routers: WAN Edge 1, WAN Edge 2, and WAN Edge 3. Encryption and decryption between WAN Edge 1 and WAN Edge 2 will use a key that is unique to that pair. Traffic between WAN Edge 1 and WAN Edge 3 will use a different pair. The public key is the only thing exchanged over OMP. The biggest benefit of this is that security-concerned customers don’t have to worry about the private key being exchanged as well. Key exchange still occurs via the vSmart, and unique pairs are generated per transport.
With Pairwise keys, the process for encryption and decryption is as follows:
- Each WAN Edge will generate a key for each transport and each peer. This key will be advertised via OMP to the vSmart.
- If Edge A needs to send data to Edge B, Session Key AB will be used. In reverse, Edge B will use Session Key BA.
- If Edge A sends data to Edge C, Key AC will be used. Edge C will use the key of CA when sending traffic in the reverse direction.
Continue Reading:
Introduction to Overlay Management Protocol in Viptela
SD-WAN Fabric Bring Up in Cisco Viptela
ABOUT THE AUTHOR

You can learn more about her on her linkedin profile – Rashmi Bhardwaj