Table of Contents
Shadow IT refers to unauthorized systems or software used within an organization without IT approval. While, Insider Threat involves individuals within the organization misusing access to harm the company, either maliciously or unintentionally.
About 10 years ago, a pandemic of shadow engulfed IT and security leaders. The large-scale consumerization of cloud computing and applications, bring your own devices (BYOD) sprawl, and remote workforce downloading non-authorized applications for work purposes fueled this phenomenon rapidly. Over time firewall rules were not enough to secure organizations data exfiltration. Sensitive company data was downloaded, stored, uploaded and transferred without the IT team knowing about it. Some of these unsanctioned applications have undisclosed vulnerabilities, some were not configured properly and many of them were targets of cyber-attacks.
In today’s article we understand the difference between shadow IT and Insider threat, the key risks, and how to tackle risks of shadow IT and insider threats.
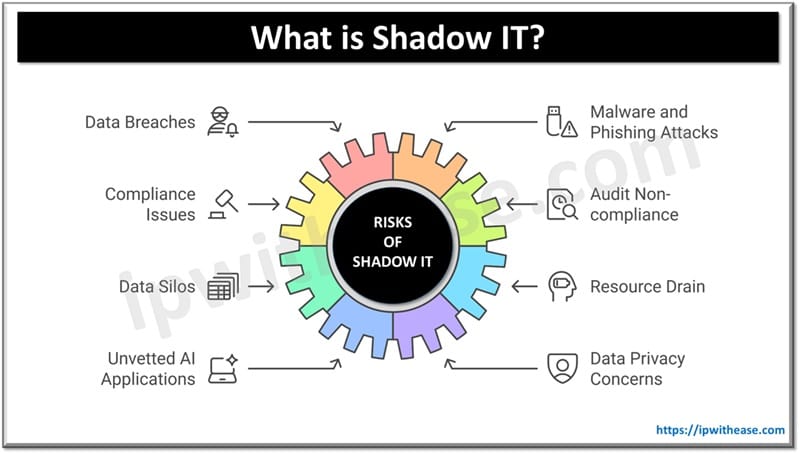
What is Shadow IT
The pandemic of shadow took a new spin in the year 2020 as the majority of organization networks were not configured to be safe access by remote workforce. Shadow IT is a term which refers to any systems, solutions, devices, applications or technology used within an organization without the approval or knowledge of the IT department. Common examples of shadow IT are cloud services, applications used for file sharing, and messengers or email apps which are not allowed as per organization security policies. The risk of using such software is very high as they could lead to sensitive data exposure due to cyber security flaws.
Related: Shadow IT vs Traditional IT
Risks of Shadow IT
- Lack of IT control – If the IT department is not aware that any system or software exists in the Corporate network they can’t check to ensure it is safe for usage and corporate assets are secured. Lack of control within the corporate network can expand the attack surface and increase risk.
- Data Loss and Leakage – Shadow IT solutions let employees gain access to data they are not supposed to get access. Unapproved applications do not ensure data backups and employees haven’t thought on recovery strategies which could pose risk of data loss.
- Unpatched Vulnerabilities and Errors – IT departments ensure that all approved software and systems are regularly patched for vulnerabilities or errors. In case of Shadow IT applications this does not happen as they are not aware of the existence of them.
- Compliance issues – Compliance with IT regulations, standards and laws is compromised if unsanctioned applications are in use which could lead to hefty fines, penalties and reputational loss to the organization.

What is Insider Threat
As the word ‘insider’ means from ‘inside’ anything which originates within your organization. Your employees, business partners and third-party contractors with legitimate access to organization network may pose significant risks to organization assets and data intentionally or unintentionally they can expose or destroy the data leading to reputation damage, fines etc. an insider threat is a security risk originated from within and may manifest in different ways such as negligence, malicious intent, data theft, system sabotage, cyber-attack and fraud. Insider threats are more challenging to detect as :
- Insiders have legitimate access to organization assets
- Insiders know where most valuable data is stored
- Insiders know organization cyber security system
Risks of Insider Threat
- Excessive access privileges – Data misuse risk increases when too many people have same level of access on critical assets with highest privileges
- Shadow IT – When employees install unapproved or unsolicited software or tools which are not managed by the IT department then it creates a shadow IT risk.
- Bring your own devices (BYOD) – When employees use personal devices such as mobile phones, laptops etc. for corporate purposes it could lead to additional security risks as personal devices are not that secure.
Comparison: Shadow IT vs Insider Threat
| Features | Shadow IT | Insider Threat |
|---|---|---|
| Definition | Use of unauthorized or unsanctioned systems, software’s, services by organization employees without the knowledge of IT department | Insider threat is a vast definition and may cover shadow IT as one type of insider threat where employee’s usage of unapproved software or systems could lead to vulnerabilities |
| Scope | Shadow IT scope is unauthorized systems, applications and services | Insider threat had a broader scope and can be generated by variety of means |
| Purpose | Shadow IT happens due to unintentional motive of employees such as to delivery work faster | Insider threat could happen due to un-intentional or intentional / malicious intent also |
| Outcome | Shadow IT may improve productivity with compromise on security | Insider threat do not improve productivity rather it causes damage to organization assets and data |
Download the comparison table: Shadow IT vs Insider Threat
ABOUT THE AUTHOR

You can learn more about her on her linkedin profile – Rashmi Bhardwaj