Table of Contents
A social engineering attack is a manipulation technique that exploits human psychology to gain unauthorized access to systems, data, or resources. Instead of directly hacking into a system, attackers trick people into revealing sensitive information, clicking on malicious links, or performing actions that compromise security.
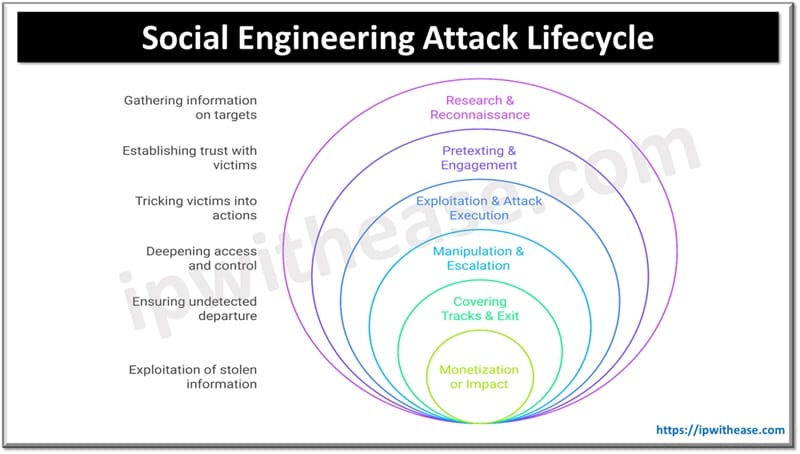
Social Engineering Attack Lifecycle
The Social Engineering Attack Lifecycle consists of several stages that attackers follow to manipulate victims and achieve their objectives. Understanding this lifecycle helps in recognizing and preventing these attacks.
1. Research & Reconnaissance
The attacker gathers information about the target, including personal details, job roles, organizational structure, and security policies. This is done using:
- Social media (LinkedIn, Facebook, Twitter)
- Company websites and public records
- Data breaches and leaked information
2. Pretexting & Engagement
The attacker establishes communication with the victim using a believable pretext (false identity or scenario). Methods include:
- Impersonating IT support, HR, or a manager
- Sending phishing emails
- Calling (vishing) or messaging (smishing) the target
3. Exploitation & Attack Execution
Once trust is established, the attacker tricks the victim into taking harmful actions, such as:
- Clicking malicious links or downloading malware
- Providing login credentials or financial details
- Granting access to secure locations or systems
4. Manipulation & Escalation
After initial access, the attacker escalates privileges or deepens the attack by:
- Gaining access to more sensitive systems
- Spreading malware within the network
- Stealing, modifying, or destroying data
5. Covering Tracks & Exit
The attacker ensures they are not detected by:
- Deleting logs or traces of the attack
- Using anonymized connections
- Leaving backdoors for future access
6. Monetization or Impact
Finally, the attacker exploits the stolen information for:
- Financial fraud, ransom, or identity theft
- Selling data on the dark web
- Disrupting business operations
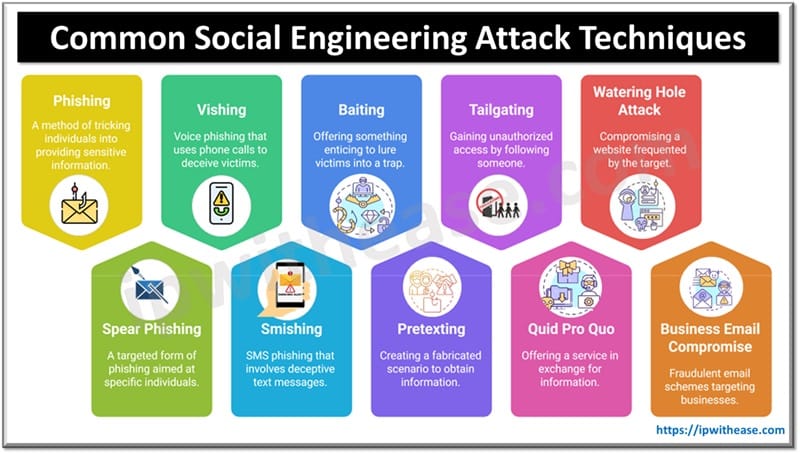
Common Social Engineering Attack Techniques
Here are the most common techniques attackers use:
1. Phishing
A deceptive attempt to trick victims into providing sensitive information, usually via email.
Example: Fake emails from banks, IT support, or popular services (e.g., PayPal, Microsoft) urging users to click malicious links.
Prevention:
- Check sender addresses for inconsistencies.
- Avoid clicking links or downloading attachments from unknown sources.
- Enable email filtering and anti-phishing tools.
2. Spear Phishing
A targeted form of phishing aimed at specific individuals or organizations.
Example: A fake email pretending to be from the CEO, asking an employee to transfer funds.
Prevention:
- Verify emails and requests through alternate communication channels.
- Limit the public exposure of personal and corporate details.
3. Vishing (Voice Phishing)
Scammers use phone calls to trick victims into revealing information.
Example: An attacker posing as an IT technician calling an employee to “reset” their password.
Prevention:
- Never share sensitive information over the phone.
- Verify caller identity before providing any information.
4. Smishing (SMS Phishing)
Attackers send malicious text messages to trick users into clicking links or revealing sensitive data.
Example: A message claiming “Your bank account is locked! Click here to verify your identity.”
Prevention:
- Avoid clicking on links in unsolicited text messages.
- Contact service providers directly if you receive suspicious messages.
5. Baiting
Attackers lure victims with free items or downloads containing malware.
Example: A free USB drive left in an office parking lot with a label like “Confidential Salary Info,” which, when plugged in, installs malware.
Prevention:
- Never plug unknown USB drives or download files from unverified sources.
- Use endpoint security solutions to scan external devices.
6. Pretexting
Attackers fabricate a convincing story to gain trust and extract information.
Example: A scammer pretending to be from HR asking for employees’ personal data to “update records.”
Prevention:
- Verify the identity of individuals requesting sensitive information.
- Avoid oversharing personal or company details.
7. Tailgating (Piggybacking)
An attacker gains physical access to restricted areas by following an authorized person.
Example: Someone pretending to be a delivery person follows an employee into a secured office without a badge.
Prevention:
- Implement access control systems and train employees to challenge unverified individuals.
- Never hold doors open for strangers in restricted areas.
8. Quid Pro Quo
An Attacker promises a benefit in exchange for sensitive information.
Example: A fake IT support person offering to fix a “computer issue” in exchange for login credentials.
Prevention:
- Confirm the identity of anyone offering unsolicited help.
- Never give credentials or sensitive information over the phone or email.
9. Watering Hole Attack
Attackers compromise legitimate websites frequently visited by their target to infect users with malware.
Example: A hacker injects malware into an industry-specific website to target employees of a particular company.
Prevention:
- Use endpoint protection and web filtering tools.
- Keep browsers and software updated.
10. Business Email Compromise (BEC)
Attackers impersonate high-level executives or partners to trick employees into transferring funds or sharing confidential information.
Example: A fake email from the CFO instructing an employee to make an urgent wire transfer.
Prevention:
- Verify payment requests via a second communication channel.
- Implement strict financial transaction approval policies.
Ways To Prevent Social Engineering Attacks
Social engineering attacks exploit human psychology rather than technical vulnerabilities. Here are key ways to prevent them:
1. Employee Awareness & Training
- Conduct regular security awareness training.
- Simulate phishing attacks to test and educate employees.
- Encourage a culture of skepticism—verify before trusting.
2. Strong Authentication & Access Control
- Use Multi-Factor Authentication (MFA).
- Implement the principle of least privilege (PoLP).
- Regularly review access permissions.
3. Verify Requests for Sensitive Information
- Confirm requests via a second communication channel (e.g., call back on a known number).
- Never share credentials or sensitive data over email or phone without verification.
4. Be Cautious with Links & Attachments
- Hover over links before clicking.
- Do not download unexpected attachments.
- Use email filtering to block suspicious messages.
5. Secure Communication Channels
- Encrypt sensitive communications.
- Avoid discussing sensitive information over public Wi-Fi.
- Use company-approved communication tools.
6. Monitor & Respond to Anomalies
- Implement behavior monitoring for unusual activities.
- Enable security logs and review them regularly.
- Set up alerts for potential social engineering tactics.
7. Physical Security Measures
- Restrict physical access to sensitive areas.
- Train employees to challenge unfamiliar visitors.
- Use ID badges and biometric authentication where possible.
8. Incident Response Plan
- Have a well-documented response plan for social engineering attacks.
- Encourage employees to report suspicious activities.
- Regularly update security policies based on recent threats.
ABOUT THE AUTHOR

You can learn more about her on her linkedin profile – Rashmi Bhardwaj