Table of Contents
Secure remote access to applications and services based on access control defined policies is the demand of 80% of organizations and more than 60% of organizations will intend to replace conventional remote access VPN as stated by a recent report from Gartner. The paradigm shift from relying on IP addresses to users and applications is the demand of the cloud based agile applications irrespective of locations they reside and also due to security concerns around IP Address based ‘trust’.
Today we look more in detail about ZTNA or Zero Trust Network access terminology, its features and use cases, advantages and disadvantages and so on.
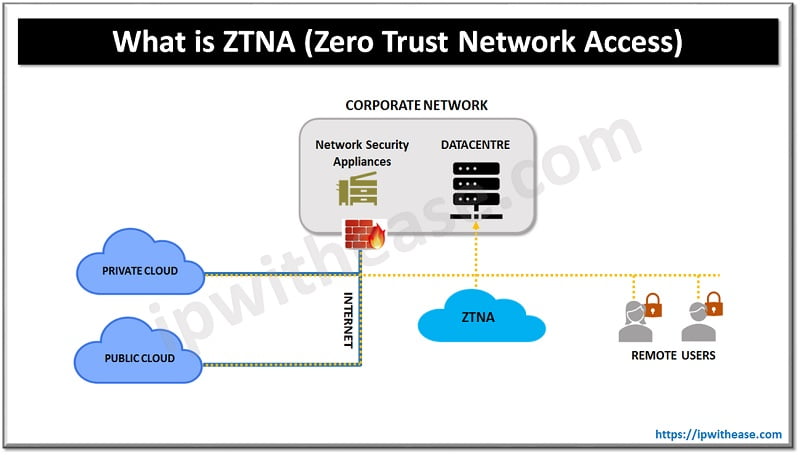
About ZTNA (Zero Trust Network Access)
Jericho forum formally established Network Access Control (NAC) architectures in 2004 and then in year 2010 Forrester coins ‘Zero Trust’ term. Later Google announced that they implemented Zero Trust security in their network which later on created interest in adoption of said technology within tech community.
It is a software defined perimeter service which provides secure and seamless connectivity to users and applications. Another name for Zero Trust Network access is Software-defined-perimeter(SDP) which comprises solutions designed for enforcement and implementation of zero trust policy of organizations.
Zero Trust security model allows users only those permissions which are required as per their job role which decreases the organization’s cyber risk and exposure to Cyber threats. User’s rights and permissions are defined using roles which are designed to map an employee role and position within the organization.
Benefits of Zero Trust Network Access
Secure Remote Access
Due to covid majority of the workforce has shifted to work from home, many organizations are using virtual private networks (VPNs) however it has several limitations such as scalability and lack of integrated security. One of the major issues with VPNs is that authenticated users are granted complete access to the networks.
Zero Trust networks implemented as part of Software defined WAN (SD-WAN) or secure access service edge (SASE) solution , gives ability to integrate Zero Trust network access into remote access solutions, reduction in remote workers access to network and restrict them only to what they require to perform as per their job role.
Secure Cloud Access
Most of the organizations are adopting or moving to cloud computing, reduction in attack surface to limit access to cloud resources is the ultimate goal for organizations. Each user and applications are assigned a role within Zero trust network access solution with appropriate permissions over cloud resources.
Minimize Risk of Account Compromise
Attackers try to steal or guess user credentials and use them to gain access to organization systems. Implementation of Zero trust network access help to minimize level of access and limit attacker ability to move laterally in the organization network
Support for Compliance Initiatives
Zero trust network access protects users and due to the cloak of invisibility the demonstration of compliance is simpler with all privacy standards.
Reduction in Data Breach Risk
Zero trust network access principle assumes every device, or workload is hostile. Each request is inspected and so is the authentication of users and devices. Trust is re-evaluated in the event when the moment of context is changed such as user location.
Ease of Integration
Organizations not using cloud computing may have different private networks and servers and other computing devices. Going through lot of procedures to integrate security modules could be a tedious task which is different in Zero trust network access as integration and implementation is easy and flexible (Based on access control policies)
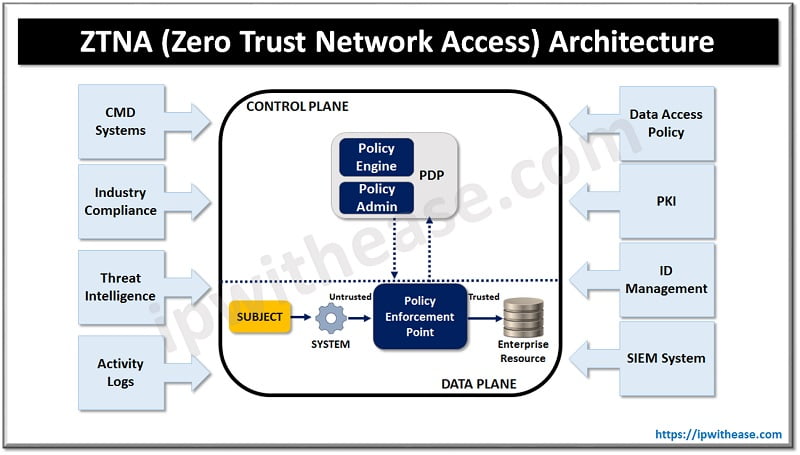
How to setup ZTNA (Zero Trust Network Access)
Zero Trust network access can be established in several ways in an organization as under:
Gateway Integration
Zero trust network access can be implemented as part of network gateway. Traffic trying to cross network boundaries implemented as gateway solutions will be filtered based on the access control policies defined at network gateway level.
Secure SD-WAN
It is implemented as a network across corporate WAN and secure SD-WAN will integrate a security stack into each SD-WAN appliance. Zero Trust network access can be incorporated into the security stack to provide centralized access management.
Secure Access Service Edge
SASE (Secure access service edge) takes SD-WAN functionality and hosts it as a cloud based virtual appliance. Which enables organization in a two-fold manner by maximizing network security and Zero trust network access functionality.
Continue Reading:
Microsegmentation vs Zero trust
SASE (Secure Access Service Edge): Cyber Security
ABOUT THE AUTHOR

You can learn more about her on her linkedin profile – Rashmi Bhardwaj