Table of Contents
Choosing between SOCKS5 and HTTP proxies is not just about personal taste. It affects:
- Which apps work well,
- How smoothly voice and game traffic runs,
- How much you can see and measure,
- And how much extra “weight” (overhead) your system adds.
This guide is here to help you compare SOCKS5 and HTTP proxies in a smart way. We’ll look at how they work in practice, what each one is best at, and how big internet trends (like more HTTP/3 and bigger web pages) should shape your choice.
In short: we’ll go through the basics, show what today’s data says, and help you get ready for what’s coming next.
The Basics: Defining HTTP and SOCKS5 Proxies
A SOCKS5 proxy is a general helper for many kinds of internet traffic. It can work with both TCP and UDP, which are the main ways data moves online.
Here’s what happens:
- Your device connects to the SOCKS5 server.
- If needed, it proves who it is (with a username and password, for example).
- Then it asks the server to open a connection (CONNECT), listen for one (BIND), or handle UDP traffic (UDP ASSOCIATE).
HTTP proxies are mainly made for the web. In normal use, they understand HTTP messages (the way browsers talk to websites).
If a program needs a simple tunnel, it sends a special CONNECT request to the proxy, asking it to open a “pipe” to a certain server and port.
Once that tunnel is made, the proxy just passes data back and forth until the connection is closed. It does not need to look inside the data, which works well for HTTPS and other fully encrypted traffic.
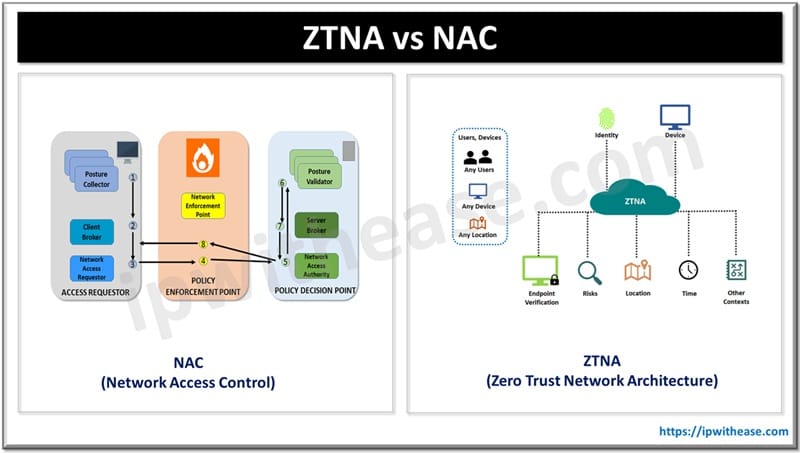
Technical Differences: The OSI Model
Thinking in layers clarifies why these tools feel different in practice. SOCKS5 acts between the application and transport layers and relays TCP or UDP without understanding the application messages. HTTP CONNECT is an application layer method that asks the proxy to create a transport tunnel.
Key layer behaviors and defaults
| Feature | HTTP Proxy (CONNECT) | SOCKS5 Proxy |
|---|---|---|
| OSI Placement | Layer 7 (Application)Creates a tunnel, then blinds forwarding. | Layer 5 (Session)Shim between app and transport. |
| Default Ports | 80 / 443Often blends in with normal web traffic. | 1080Standard convention for SOCKS. |
| Addressing | HostnamesThe target is usually host:port. | IPv4 / IPv6 / DomainsMore flexible addressing. |
| UDP Support | No Not provided by HTTP CONNECT. | Yes Supported via UDP ASSOCIATE. |
Security and Anonymity
Neither approach provides end-to-end encryption to the final destination by itself. Security on the last leg still depends on using TLS or another secure protocol between the client and the target server. HTTP proxies can require client authentication using standardized HTTP schemes, but the details of those schemes are independent of the tunnel itself. SOCKS5 defines a negotiation step where client and server agree on an authentication method, with a simple username and password option available as a sub-negotiation.
For anonymity, both options hide your source IP from the destination by placing the proxy in the path. Once CONNECT or SOCKS5 forwarding begins, the payload is opaque to the proxy if you use TLS end-to-end to the target. In many deployments the more important security differences are operational. HTTPS proxies on port 443 can blend into standard egress rules and are easy to monitor with existing HTTP tooling. SOCKS5 gives you a single, protocol-agnostic access point for TCP and UDP that you can lock behind authentication. In either case, pair the proxy with strong TLS end-to-end and avoid sending credentials over cleartext links.
Performance & Strategy: The Impact of HTTP/3
The strategic question is not only which proxy works today, but which one lines up with where traffic is heading. HTTP/3 runs over QUIC on UDP. The IETF’s core spec notes that “QUIC provides applications with flow-controlled streams for structured communication, low-latency connection establishment, and network path migration.” That design reduces the cost of connection setup and avoids TCP head-of-line blocking. If a large part of your traffic already uses HTTP/3, a transport-level relay that can forward UDP cleanly will fit that pattern with fewer compromises.
Scale also matters. Cloudflare recently wrote that its edge establishes about 18 million TLS connections per second on average, and estimated that moving to a post-quantum signature scheme would add roughly 0.5 percent of current capacity as overhead. Even if your footprint is orders of magnitude smaller, the lesson is clear. Small bits of per-connection overhead add up fast at scale. In busy environments, favor proxy paths that keep handshakes short and avoid unnecessary parsing.
Matching Proxy Types to Your Traffic Mix
Where do HTTP proxies still shine? For strictly web traffic that must honor HTTP methods, headers, and cache hints, an HTTP proxy can provide protocol-aware features like header filtering, request logging in familiar formats, and simple policy controls at the application layer. It fits best when all client apps are browsers or HTTP clients and when UDP is not required. By contrast, a transport-level relay is a better match when you have mixed protocols, need UDP for real-time flows, want to push DNS resolution to the far side for privacy, or aim to minimize application-layer touch.
A practical way to decide is to map your top flows. If most of your high-value traffic is browser-based and stays on HTTP, an HTTP proxy keeps things tidy. If your environment mixes web, databases, messaging, and real-time media, pick a transport relay for the default path and add HTTP-aware controls only where you truly need them. Keep in mind the direction of travel. Rising HTTP/3 adoption, heavier pages, and evolving handshakes all reward solutions that keep extra trips and parsing to a minimum.
ABOUT THE AUTHOR
IPwithease is aimed at sharing knowledge across varied domains like Network, Security, Virtualization, Software, Wireless, etc.