Table of Contents
Although IPSec is a very wide topic to cover but the following few commands and outputs are really helpful in initial troubleshooting.
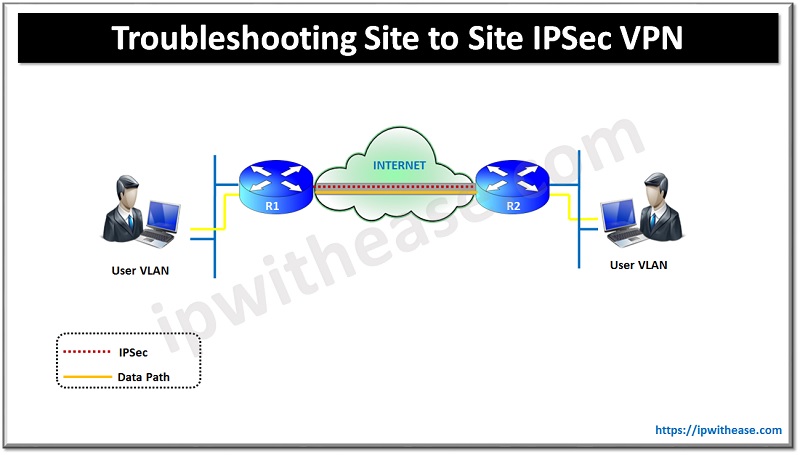
Troubleshooting Commands: IPSec site to site VPN
(A) “show crypto isakmp sa”
By this command we can test the present status of the IPSec peering. The state should be “QM_IDLE”. Any other state suggests an issue (i.e. issue in crypto map; expired digital certificates; etc.)
Router#show crypto isakmp sa
Dst
src state conn-id slot status
172.16.x.x 172.16.x.x QM_IDLE 11 0 ACTIVE
172.16.x.x 172.16.x.x QM_IDLE 12 0 ACTIVE(B) “show crypto isakmp sa detail”
This command shows the time (under lifetime parameter) by which the crypto session is established or stable. This clock runs in opposite manner. For example: – In below output, the time is 23:00:29, it means the crypto is established since 59 minutes 31 seconds. Somewhere it’s configured in span of 8 hrs & somewhere in 24 hrs span.
Router#show crypto isakmp sa detail
Codes: C – IKE configuration mode, D – Dead Peer Detection
K – Keepalives, N – NAT-traversal
X – IKE Extended Authentication
psk – Preshared key, rsig – RSA signature
renc – RSA encryption
C-id Local Remote I-VRF Status Encr Hash Auth DH Lifetime Cap.
11 172.16.x.x 172.16.x.x ACTIVE 3des md5 rsig 2 23:00:29 D
Connection-id:Engine-id = 11:1(software)Related – Site to Site VPN vs Remote Access VPN
(C) “Show crypto map”
This command shows some configured parameters like peer addresses, Access-list which will initiate interest traffic to make IPSec tunnel up, Interfaces which use this crypto map
Note:-All the interfaces including backup link (i.e. BRI in case of ISDN) should be included under Interfaces using crypto map.
Router#show crypto map
Crypto Map: “TESTMAP” idb: Loopback1 local address: 172.16.x.x
Crypto Map “TESTMAP” 5 ipsec-isakmp
Description: ipsec tunnel to HO
Peer = 172.16.x.x
Peer = 172.16.x.y
Extended IP access list 118
access-list 118 deny ip any host 10.10.10.x
access-list 118 deny ip any host 10.10.10.x
access-list 118 permit ip host 10.1.0.x host 10.6.0.x
access-list 118 deny ip host 10.1.1.x host 10.6.0.x
access-list 118 permit ip 10.1.0.0 0.0.1.255 10.0.0.0 0.0.255.255
Current peer: 172.16.x.x
Security association lifetime: 4608000 kilobytes/3600 seconds
PFS (Y/N): N
Transform sets={
XYZMAP,
}
QOS pre-classification
Interfaces using crypto map TESTMAP:
Loopback0/1
Serial0/0
Serial0/1
BRI1/0
BRI1/0:1
BRI1/0:2
BRI1/0:1
BRI1/0:2
Virtual-Access1(D) “Show crypto ca certificate”
This command’s output confirms whether the digital certificate has been expired. It contains a start & end date-time.
Instant remedy is to configure some preshared keys like “crypto isakmp key abcd45ef address 172.16.x.x (remote peer)
Router# show crypto ca certificate
Certificate
Status: Available
Certificate Serial Number: 5DD5248C6C89369E95898431A40539E
Certificate Usage: General Purpose
Issuer:
cn=XYZ VPN IPSec Certificate Authority
ou=XYZ VPN
o=XYZ Company Limited
Subject:
Name: Router.xyz.com
Serial Number: 1C6E42BE
serialNumber=1C6E42BE+hostname=Router.xyz.com
CRL Distribution Points:
ldap://directory.safescrypt.com/CN = XYZ VPN IPSec Certificate Authority, O
U = XYZ VPN, O = XYZ Company Limited?certificaterevocationli
st;binary?base?objectclass=*
Validity Date:
start date: 05:30:00 IST Jan 4 2010
end date: 05:29:59 IST Jan 5 2011
Associated Trustpoints: XYZ.comABOUT THE AUTHOR

You can learn more about her on her linkedin profile – Rashmi Bhardwaj