Table of Contents
The system boot process involves multiple steps. Devices running operating systems such as Windows have several requirements to boot into the operating system. Once the device firmware initializes all hardware, the device needs to ensure there is enough power for the boot process. The device needs to ensure it is booting into the appropriate OS depending on if the user wants to perform an update or restore, or boot the device into the main OS.
In today’s topic we will learn about the UEFI boot process, how UEFI works, its key features and usage.
UEFI Boot Process
UEFI or Unified Extensible Output System is a firmware interface which comes along with the system motherboard and works like an interpreter between the system firmware and the operating system (OS). It was first adopted in the year 2005 by industry, and it is the first program which runs on your system during the initial boot process. It has three main responsibilities – check which hardware components are attached to the motherboard, wake up the attached components and final handover to the operating system.
Initial start up is its main responsibility along with other uses. Uefi dictates at what frequency CPU, GPU, RAM should be operating as how much power they should draw from PSU (Power supply unit), the speed of fan, RAM latency, and other hardware released settings are governed by this low-level software. If the operating system is still corrupt, you can use UEFI to troubleshoot if it still recognizes what hardware is connected to the system.
UEFI was developed as an offshoot of its 64-bit titanium server architecture in the 1990s. The technology was developed to address memory and processing limitations in x86 servers.
How UEFI Boot Process Works
When UEFI starts initially it first goes for a power on self-test (POST), a diagnostic test to ensure hardware devices are functioning as expected. UEFI scans all bootable storage devices connected to a system having a valid GUID partition table (GPT) to find an EFI service partition to boot from, and directly loads the OS from the correct partition. To use UEFI both hardware and software of the system should support UEFI and system storage need to be a GPT disk.
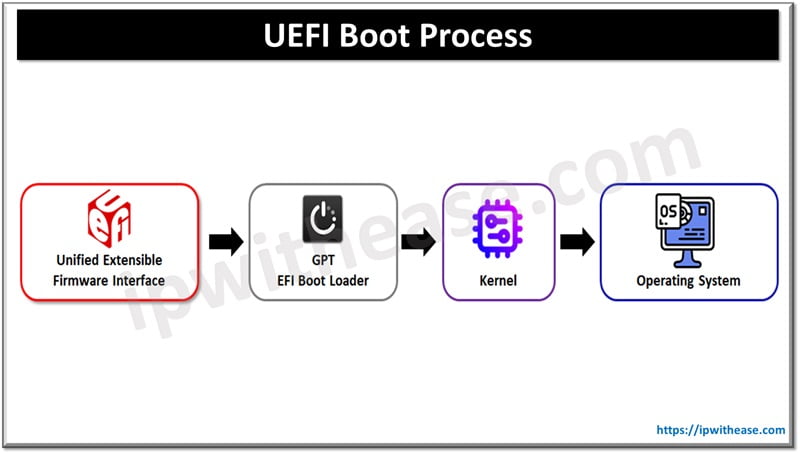
Systems using the UEFI method, UEFI firmware reads its boot manager data to determine which UEFI application is to be launched and from where. This is a lightweight alternative to BIOS which uses only the information required to launch the OS boot process. UEFI provides enhanced system security features and supports existing BIOS for backward compatibility. UEFI has platform related data tables and boot the runtime service calls used by Operating system loaders.
UEFI stores initialization data in an EFI partition table on non-volatile flash memory instead of firmware. It can load during boot from a drive or network share also. It deploys a more flexible partitioning scheme and uses 64-bit values to enable creation of up to 128 partitions. The EFI partition uses file allocation table (FAT) and supports FAT 16, FAT 32 or virtual FAT.
Most new systems bundle UEFI firmware which runs in compatibility support mode for older versions of 32-bit windows.
Features of UEFI
- Boot mode – Microsoft windows supports both 32-bit UEFI and 64-bit UEFI
- Drivers – Uefi supports 2.2 TB or larger capabilities including drivers with capability of (9.4 Zettabytes)
- Discrete Drivers – discrete drivers are supported by UEFI
- Graphical user interface – enablement of new modules in GUI easily, such as motherboard device drivers, and attached peripheral devices
- Multi-OS support – UEFI supports users to install Debian based Ubuntu and other Linux variants, windows OS loaders in same EFI partition
- Programming – it is written in c language which enable users to add or remove functions with lesser programming as compared to BIOS
- Security – Secure Boot is UEFI protocol for windows ver 8 and later. It makes system firmware the root of trust for device verification and integrity of the system. This capability helps to prevent rootkit attacks in the time between boot and handover to the operating system.
ABOUT THE AUTHOR

You can learn more about her on her linkedin profile – Rashmi Bhardwaj