Table of Contents
Introduction to VPS Hosting Security
Understanding Virtual Private Servers (VPS)
Virtual Private Servers, or VPS for short, are like having your own slice of a powerful server’s pie. Each slice runs its own operating system and applications, independently yet nestled within the same physical server. Think of it as renting a condo in a high-rise building; you manage your own space and can renovate as you wish, but you still share the building’s structure and common facilities. This balance of control and shared resources makes VPS a go-to for businesses needing more elbow room online without the full expense of a dedicated server.
Importance of Securing Your Business Network
It’s a digital world out there, and securing your business network is not just a luxury, it’s absolutely essential. From safeguarding critical data to maintaining network uptime, a secure network ensures the pillars of trust, confidentiality, and availability stand strong. In addition, search engines frown upon and may penalize unsecured sites, which could knock you down a few pegs in search rankings, affecting your visibility and credibility. So, network security is a vital lifeline for your business.
Pillars of a Strong VPS Security Framework
Regular Updates and Patch Management
Keeping your VPS running smoothly is a bit like maintaining a car, it needs regular check-ups and tune-ups. Enter regular updates and patch management. By staying on top of the latest software releases and security patches, you keep your system honed against vulnerabilities.
Fail-Safe Access Controls
By setting up strict ground rules on who gets the access, you ensure that only authorized users can enter. It’s all about the right balance: too lenient, and you risk intrusion; too strict, and you might hinder productivity. Implementing role-based access controls and keeping a tight ship on user privileges will make sure that everyone has just enough access to do their job, without leaving your virtual gates wide open for cyber invaders to storm in.
Step-by-Step Measures for Enhancing VPS Security
Implementing Strong Authentication Methods
Level-up your security game with multi-factor authentication (MFA). It’s like a double-check system where a stolen password alone won’t cut it for an intruder; they’ll also need a second key, which could be a fingerprint or a temporary code sent to a mobile device.
Strategic Firewall Configuration and Intrusion Prevention
Setting up a firewall for your VPS scrutinizes incoming and outgoing traffic, allowing the good while barring the bad. With strategic firewall configuration, including defining comprehensive rules and understanding the traffic patterns specific to your business, the firewall turns into an even more powerful guardian. In addition, Intrusion Prevention Systems alert you to potential threats so that an action is taken against them. Together, a well-configured firewall coupled with IPS makes for a formidable first line of defense, making your VPS a tough nut for cyber attackers to crack.
Advanced VPS Security Techniques for Businesses
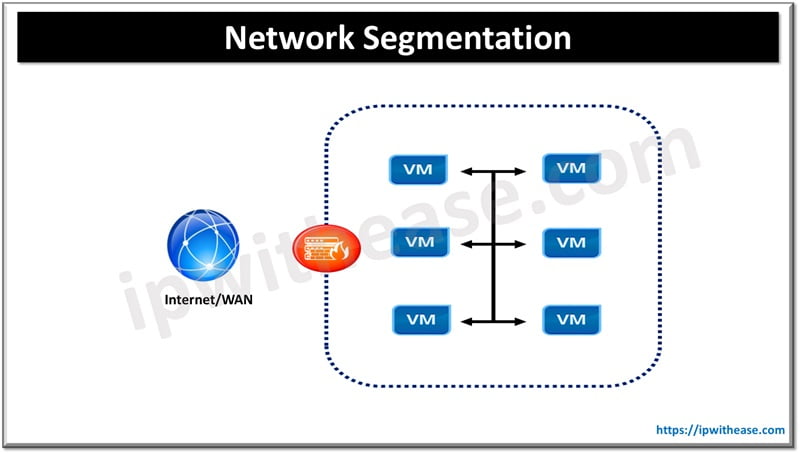
Network Segmentation to Shield Sensitive Data
Ever considered how a ship remains afloat even if one compartment is breached? It’s all thanks to segmentation; and the same principle can shield your VPS-hosted sensitive data. By dividing your network into distinct segments, or subnetworks, you create multiple, contained zones. If one is compromised, the breach doesn’t flood the entire network.
This compartmentalization means you can have highly sensitive data in one secure silo while less critical operations are in another, each segment with its own set of stringent rules and controls. This way, you create not just one barrier but a series of hurdles for any would-be attacker, making unauthorized access much tougher and its potential impact significantly less crippling for your business.
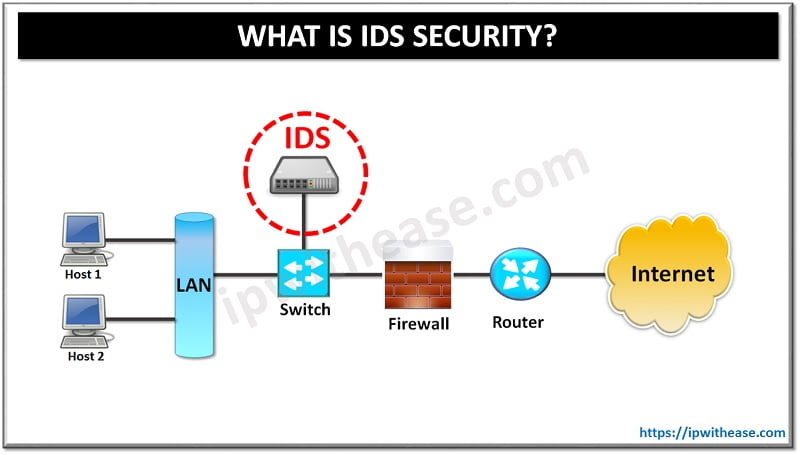
Intrusion Detection Systems: Proactive Threat Management
Unlike a standard firewall, Intrusion Detection Systems (IDS) actively examine traffic patterns for anything out of the ordinary. They meticulously analyze this data looking for signs of potential threats in real-time, keeping you one step ahead of the cyber-baddies. Pair them with Intrusion Prevention Systems, and you’re not just detecting threats; you’re actively blocking them as they arise.
Best Practices for VPS Maintenance
Regular Security Audits: A Critical Routine
Regularly scheduled audits are like reconnaissance missions uncovering any cracks in your digital defenses that could be exploited. They can sniff out outdated software, spot misconfigurations, or even flag an unnecessary open port before it becomes an open invitation for cyber intruders. By making security audits a staple in your routine, you keep your VPS hosting environment resilient and responsive, making sure the security posture isn’t just strong today, but ready for whatever tomorrow might bring.
Backup Strategies: Ensuring Data Continuity
Robust backups for your VPS is the smart play. And here’s a pro tip: the 3-2-1 rule. Have three copies of your data (that’s your original plus two backups), store them on at least two different types of media, and keep one copy offsite. It’s like an insurance policy for your data, ensuring if disaster does strike, your business continuity doesn’t skip a beat. Whether it’s about bouncing back from hardware failure, cyberattacks, or accidental deletions, a well-oiled backup strategy minimizes downtime and data loss anxiety.
Choosing the Right VPS Provider
Reliability and Reputation in Hosting Services
- Check out their track record
- Monitor their uptime figures
- Surf through the customer reviews and testimonials
A provider’s reputation is crafted over time through consistent performance and by the peace of mind they’ve provided to other businesses like yours. So, choose wisely.
Understanding the Role of Encryption in Provider Offerings
When you’re deciphering the offerings of various VPS providers, encryption should be a star player on your checklist. It’s the secret code that keeps your data under wraps, transforming sensitive information into an unreadable format for anyone who isn’t supposed to see it. Providers worth their salt will support SSL/TLS protocols, ensuring that data shuttle service between your site and its visitors is secure, keeping eavesdroppers at bay. And for data at rest? Your provider should offer options for encryption too, locking down your stored data as tightly as your in-transit info.
Preparing for the Worst: Incident Response Planning
Crafting an Incident Response Plan for Your VPS
When cyber trouble comes knocking, an incident response plan isn’t just handy, it’s your playbook for swiftly tackling the crisis. Crafting this plan is about mapping out how to detect, contain, and eliminate threats, and then getting everything back on track. Detail every role, every step, and every communication to be crisp and clear, leaving no room for doubt in a high-pressure situation.
Learning from Security Incidents to Fortify Defenses
As the old saying goes, “What doesn’t kill you makes you stronger,” and this certainly applies to security incidents. When these unfortunate events do happen, they provide a wealth of insight. Harness these experiences as learning opportunities by conducting thorough post-mortem analyses. Dig into the ‘how’ and ‘why’ to unveil any weaknesses or slip-ups in your defenses. Then, take what you’ve learned to fortify your VPS against future attempts.
Empowering Your Team for Better VPS Security
Educating Users on Security Best Practices
- Tailor sessions to cover the essential do’s and don’ts, from crafting uncrackable passwords to spotting the cleverest of phishing attempts.
- Foster a culture where security is everyone’s biz, and remind them of the big WHY behind each guideline.
- When your whole crew is savvy about security, you’re not just relying on tech, you’re bolstering your defenses with a vigilant, informed workforce.
Review User Rights and Permissions Regularly
Having the right people with the right access is like fitting a puzzle perfectly with no piece out of place.
- To maintain this precision, regularly reviewing user rights and permissions is a must. It’s about affirming that everyone has just the access they need, nothing more, nothing less.
- Grant them carefully considered access.
- This routine checkup not only aligns with the principle of least privilege but also helps minimize potential insider threats.
- By keeping user rights in check, you’re fine-tuning a crucial layer of your defense strategy, ensuring tight control and oversight over who can touch what in your precious VPS environment.
ABOUT THE AUTHOR
IPwithease is aimed at sharing knowledge across varied domains like Network, Security, Virtualization, Software, Wireless, etc.